So much for a new year meaning a fresh start. 2017 brought us security vulnerabilities such as WannaCry ransomware and the Equifax hack, but things haven't got much better at the beginning of 2018.
We had only just finished welcoming in the new year when the next security bombshell hit the headlines. And it wasn't only one flaw, but two. Nicknamed Meltdown and Spectre, the vulnerabilities originate from computer microprocessors. In terms of severity and number of people potentially affected, experts have likened them to 2014's Heartbleed bug.
The bugs can attack all desktop operating systems, but in this article, we're only going to focus on Windows. Let's take a closer look at how the vulnerabilities work and how you can tell whether they have affected you.
Meltdown and Spectre: A Closer Look
Before we explain how to detect the two bugs on your own system, let's take a moment to fully understand what the two vulnerabilities are and how they work.
The same group of security researchers were responsible for finding both the problems. At an elementary level, they are flaws in processor architecture (i.e. the transistors, logic units, and other tiny components that work together to make a processor function).
The flaw allows a would-be hacker to expose almost any data that a computer processes. That includes passwords, encrypted messages, personal information, and anything else you can think of.
Meltdown only affects Intel processors. Worryingly, the bug has been present since 2011. It uses part of the out-of-order execution (OOOE) process to change the cache state of a CPU. It can then dump the contents of the memory when it usually would be inaccessible.
Spectre can attack Intel, AMD, and ARM processors, and can thus also affect phones, tablets, and smart devices. It uses a processor's speculative execution and branch prediction in conjunction with cache attacks to trick apps into revealing information that should be hidden within the protected memory area.
Spectre attacks need to be customized on a machine-by-machine basis, meaning they are harder to execute. However, because it's based on an established practice in the industry, it's also harder to fix.
Is Your Windows 10 PC Affected by Meltdown?
Thankfully, Microsoft has published a handy PowerShell script that you can run on your system. Follow the steps below and you can install and activate an additional module on your system. The results will indicate whether you need to take further steps.
First, run PowerShell as an administrator: press Windows key + Q or open the Start Menu, type PowerShell, right-click the first result (Windows PowerShell, desktop app) and select Run as administrator.
After PowerShell has loaded, follow these steps to find out whether your PC is affected by Meltdown. Note that you can copy-and-paste commands into PowerShell.
- Enter Install-Module SpeculationControl and press Enter to run the command.
- Confirm the NuGet provider prompt by entering a Y for Yes and hitting Enter.
- Do the same for the Untrusted repository prompt.
- Next, type Set-ExecutionPolicy $SaveExecutionPolicy -Scope Currentuser and press Enter
- When the installation has completed, type Import-Module SpeculationControl and press Enter.
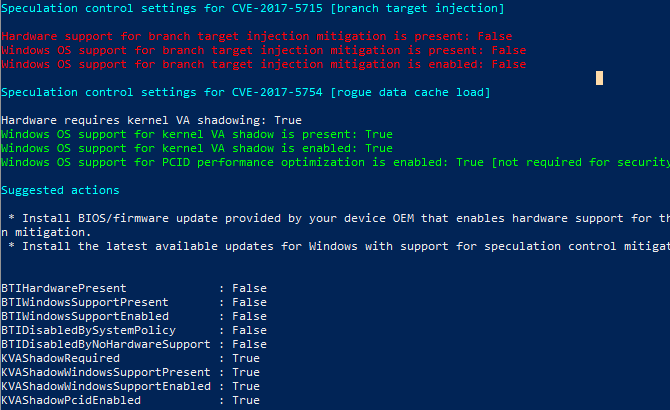
- Finally, type Get-SpeculationControlSettings and hit Enter.
After you have run these commands, check the output result for the results -- it will be either True or False.
If you see only True messages, congratulations, you are protected and don't need to take any further action. If a False pops up, your system is vulnerable, and you need to take further action. Be sure to note the suggested actions shown in the results. As shown in the screenshot above, our test computer requires a BIOS/firmware update and yet has to install a patch provided through Windows Update.
How Can You Protect Yourself Against Meltdown?
To the company's credit, Microsoft originally moved quickly to issue a patch for Meltdown. You can find it through the Windows Update tool (Settings > Update & Security > Windows Update > Check of updates). You need to download and install patch KB4056892 for Windows build 16299.
Troublingly, the patch is incompatible with some antivirus suites. It only works if your security software's ISV has updated the ALLOW REGKEY in the Windows registry.
You should also update your browser. Google has patched Meltdown in Chrome 64 and Mozilla has updated Firefox in version 57 (Quantum). Microsoft has even patched the latest version of Edge. Check with your browser's developer if you use a non-mainstream app.
Lastly, you need to update your system's BIOS and firmware. Some computer manufacturers include an app within Windows so you can quickly check for such updates. If your PC manufacturer didn't supply one, or if you deleted it, you should be able to find updates on the company's website.
How Can You Protect Yourself Against Spectre?
Meltdown is the more immediate threat and is the easier of the two bugs for hackers to exploit. However, Spectre is harder to remedy.
Because of the way Spectre works, fixing it will require companies to completely redesign the way they build processors. That process could take years, and it could be decades until the current iteration of processors is entirely out of circulation.
But that doesn't mean Intel hasn't tried to offer its customers ways to protect themselves. Unfortunately, the response has been a shambles.
In mid-January, Intel released a Spectre patch. Immediately, Windows users started complaining that the patch was buggy; it was forcing their computers to randomly reboot at unexpected times. Intel's response was to release a second patch. It didn't fix the issue; the reboot problems continued.
At this point, millions of users have installed the patch. Intel told customers not to download either patch until it could fix the issue. But there was a problem for Windows users. The Intel patch was being delivered through the Windows Update app. Users continued to unwittingly install it; after all, we all know how opaque the current Windows update process is.
While random reboots are certainly annoying, the most worrying part of the buggy patch was the potential for data loss. In Intel's own words, "It caused higher than expected reboots and other unpredictable system behavior [...] which may result in data loss or corruption."
Fast-forward to the end of January, and Microsoft was forced to step in. The company took a highly unusual step. It issued an out-of-band emergency security update for Windows 7, 8.1, and 10 that completely disables Intel's patch.
How to Install the Microsoft Fix
Unfortunately, the new patch will not be available through the Windows Update app. You will have to install it manually.
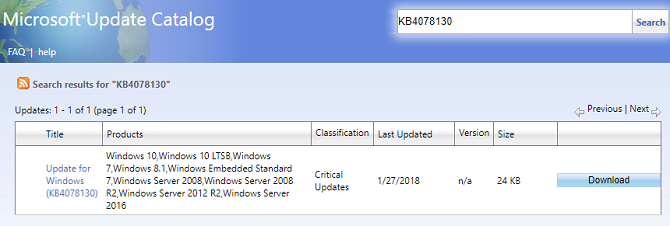
To begin, head to the Microsoft Update Catalog. You need to find Update for Windows (KB4078130). When you're ready, click on Download.
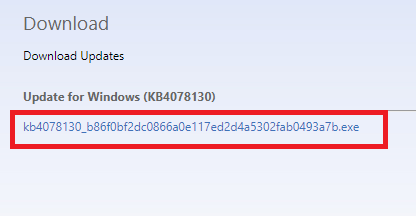
Next, click on the [string of text].EXE file.
The file is tiny and will only take a couple of seconds to download. When the download has finished, double-click on the EXE file and follow the on-screen instructions.
So, what about the future? If you've been following along, you'll have realized that affected users are back to where they started: exposed and unprotected.
Hopefully, Intel will release a more successful patch in the coming weeks. In the meantime, you'll have to sit tight.
Do Meltdown and Spectre Worry You?
It's understandable to feel worried. After all, our computers quite literally hold the keys to our lives.
But it's also important to take solace from the facts. You are highly unlikely to be the victim of a Spectre attack. The time and effort a hacker needs to put in for an unspecified return make you an unattractive proposition.
And the big tech companies have known about the two issues since the middle of 2017. They've had plenty of time to prepare patches and respond in the best way they are able.
Despite the facts, do the Meltdown and Spectre threats still worry you? You can let us know your thoughts and opinions in the comments section below.