Until recently, I'd never actually met anyone that had received a copyright infringement letter for downloading films on the internet. Their Internet Service Provider contacted them directly, informing that they would be taken them to court unless they agree to pay a set fine.
My friend was culpable and not wanting to risk a court appearance as well as a large fine, settled with his ISP and the copyright holder.
Receiving a copyright infringement notice is worrying. What happens if you receive a copyright notice? How does your ISP know about your copyright infringement?
Should You Be Worried About a Copyright Infringement Notice?
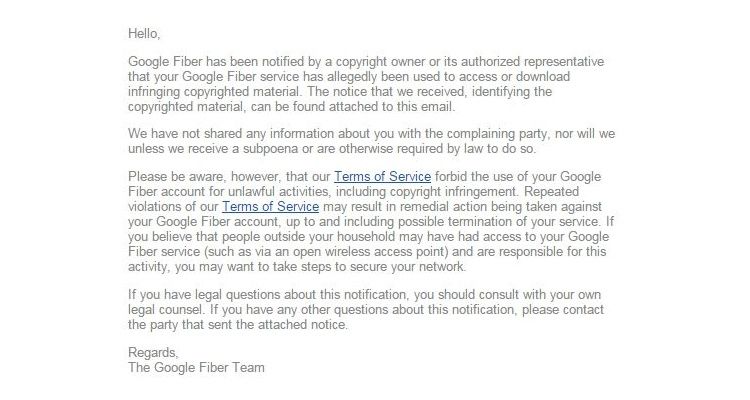
"We are writing to inform you that [your ISP] recently received notification from a copyright owner of a copyright violation that appears to involve [your ISP account]. The work(s) identified by the copyright owner in its complaint are listed below.
We are contacting you because our records indicate that the internet Protocol (IP) address provided to us by the copyright owner was assigned to your service on the date and time identified by the copyright owner."
A letter containing those words is usually a precursor for a series of negative events. Copyright infringement is a serious crime that ISPs have a duty to investigate. After all, their network is the focal point of the copyright infringement.
Your ISP is tracking your every movement online. They can see the sites you visit, when you visit them, how long you lurk there, and more. Your ISP can also see your download activity, including any peer-to-peer services (torrenting, for instance), which they will link directly to your IP address.
"Please note that we have not provided any of your private information to the copyright holder at this time. [ISP] will not provide your identifying information without a lawful subpoena or other lawful process. However, upon receipt of a lawful subpoena or other lawful process [your ISP] will release your information to the copyright owner."
Your ISP might not release your details immediately. The vast majority of ISPs release a warning similar to this after receiving a notice of copyright infringement. However, as the infringement warning states, if the ISP receives a lawful request, they have to comply. It is the law.
You cannot simply change your ISP to escape a copyright infringement notification, either. You might get a clean slate with a new ISP. But unless you are changing your address, and in reality, your name, that copyright infringement record will follow you around. As with many things relating to the law, it is difficult to run from your problems.
What Is Copyright Infringement?
When a studio releases a film or a musician releases an album into the public realm, the vast majority of the time, this content features copyright protection. It isn't just music or films. Photographs, paintings, books, articles, podcasts, and countless other types of content carry copyright.
Copyright is a legal right that protects work, granting the original content creator exclusive rights over the ownership and distribution of the work. Copyright can and does expire. Most major copyright holders extend the copyright of important works to maintain their control over their original content (or over copyright purchased from other creators).
When you receive a copyright infringement notice from your ISP, it will contain the exact copyright allegedly broken on your network.
For instance, a Comcast notice of claim of copyright infringement will feature an email subject line such as "Notice of Action under the Digital Millennium Copyright Act (DMCA)." The email body explains Comcast's obligation to notify the network user (you) that a copyright owner has found an infringement on your network.
The email will also list the copyright infringing work, usually using the exact file name, the infringing IP address, the infringement type (e.g., P2P, illegal stream, etc.), and the reporting copyright owner.
The following Comcast DMCA notice was sent after the original poster downloaded the original World of Warcraft 1.12 Client using a torrent program:
Of course, it isn't just Comcast that send DMCA takedown notices. ISPs are compelled by law to send the notice, regardless of their "stance" on pirating. Word to the wise, ISPs stance on pirating isn't good.
The Google Fiber DMCA copyright infringement varies, depending on the "amount" of copyright infringement. However, the Google Fiber DMCA usually reads "Notice of Unauthorized Use of Copyrights Owned by [insert copyright owner]." Like the Comcast DMCA email, it instructs the network owner as to the copyright infringing work, the IP address, and so on.
Copyright infringement emails and letters from Verizon, Bell, Rogers, and other US-based ISPs all follow a similar pattern.
AMC Issues DMCA Threats Regarding The Walking Dead
Copyright infringement isn't always obvious, either. For instance, Season Six of AMC's The Walking Dead finished on a massive cliff-hanger. Understandably, during the off-season, fan sites began speculating as to the outcome of the cliff-hanger.
However, AMC threatened The Walking Dead fansite, The Spoiling Dead with legal action. If during their speculation regarding the cliffhanger they hit upon the correct outcome for the return to Season Seven, "AMC says they will sue us . . . Their stance is that making such a prediction would be considered copyright infringement."
Game of Thrones IP-Echelon DMCA Notices
Certain titles attract higher levels of pirating. In recent years, Game of Thrones copyright owner, HBO, has sent tens of thousands of copyright infringement notices as fans pirate the latest Game of Thrones series. HBO teamed up with the anti-piracy company, IP-Echelon, to serve and enforce the copyright infringement notices.
However, HBO also took another step to reducing the amount of Game of Thrones pirating taking place. Instead of restricting Game of Thrones to cable-only, it first added each series to its on-demand streaming service, followed by allowing an Amazon Prime channel add-on subscription (albeit at a steep price of $14.99 per month). The result was less piracy, more engagement, and potentially a happier audience.
How to Avoid Copyright Infringement?
If you receive a copyright infringement from Verizon, Comcast, Telus, Spectrum, or any other ISP, you are on a list. (Aren't we all on a list somewhere?) While you might not be able to have your name removed from that list, you can certainly ensure no additional copyright infringements appear alongside your name and IP address.
What measures can you take to make sure that there are no copyright infringements on your home network?
1. Stop All the Downloading (of Illegal Content)
It should go without saying… but stop downloading illegal content through illicit sources. If you are unsure what the copyright status of a file is, it is best not to download. Instead, you can head to the U.S. Copyright Office website and complete a search for whatever the file, film, album, or content is.
My tip is to use a keyword, rather than the exact file name.
The rise of Android-based Kodi boxes and other streaming services further complicates matters. Kodi boxes are sold openly in shops and online, but the streaming apps available on those boxes may well use copyrighted materials.
2. Talk to Your Housemates About Copyright Infringement
If you are certain it was not you downloading the latest episode of Squid Game, go and chat to your family, housemates, or anyone with access to your internet connection. Hopefully, you can have an honest conversation about the issue of pirating illegal content, as well as the potential repercussions.
(You could show them a few legal download alternatives, too.)
3. Check the Letter for Details, Watch Out for Scams
If you meet a wall of silence, head back to the email or letter and check for details. Copyright infringement enforcement letters list the infringing content, including the file name and download method. If you see the file is the latest Kendrick Lamar album, chances are it wasn't Great Aunt Ethel (but if she did, props to her).
Regardless, the information in the copyright infringement letter or email will help you narrow down who is downloading what on your internet connection. Talk to them about safe downloading, copyright infringement, and alternative sources.
The other thing to consider is if your copyright infringement letter is a scam. Some copyright infringement notices also contain a notice of payment, causing people to panic and pay without considering if the letter is real.
For instance, scammers piggybacking on the HBO Game of Thrones IP-Echelon copyright infringement sent thousands of scam emails including a direct settlement fee of $150 for the alleged copyright infraction.
If you receive an email from IP-Echelon, Lionsgate, Rightscorp, CEG TEK, or any other copyright enforcement firm, don't rush to pay. Do your research first.
4. Check Your Home Network for Intruders
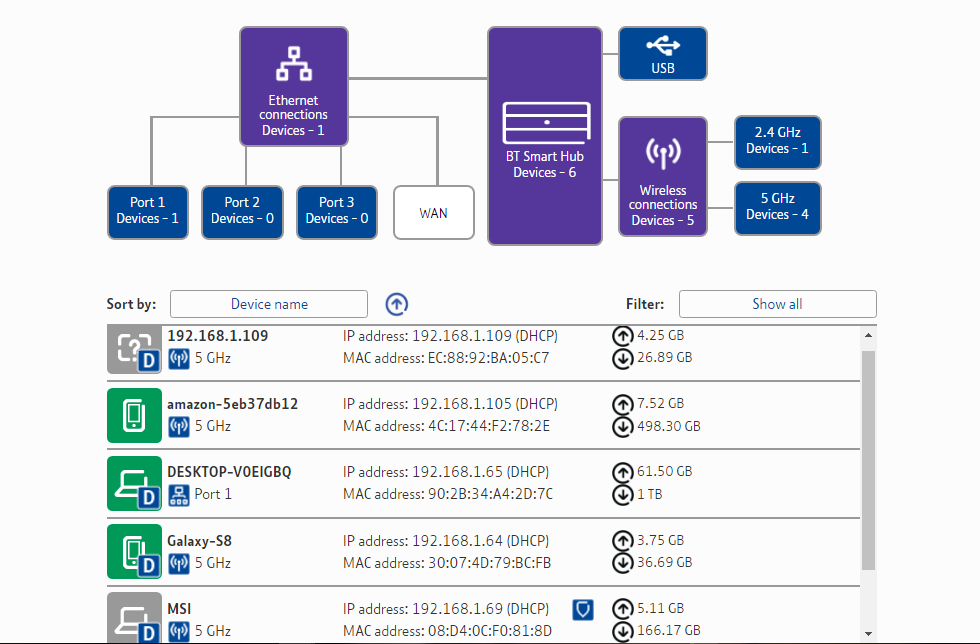
If it really is no one in your household, even after you give the kids and Great Aunt Ethel the third degree, you should check your home network. Your first stop is your router. Your kids might not be pirating copyrighted material, but what if they gave the internet password to a friend?
How about a neighbor piggybacking on your internet, stealing your bandwidth, and triggering the wrath of copyright holders?
Your router will show you any connections. Furthermore, some will even keep a log of recent connections. If there are more devices than you're aware of, it is time to consider your options.
Use your web browser to access your router interface. The address varies by router, but many companies now print the default router address on the device. My connected device list looks like so:
I can account for all of those devices. If you cannot, you might have found your copyright infringing culprit. Unfortunately, finding out exactly which neighbor is piggybacking is a bit more difficult (and you might not want to cause a confrontation). In this case, your router will have some form of IP address or MAC address filtering or blocking that you can apply.
5. Virus Scan
The last tip is the good old virus or malware scan. While somewhat unlikely, there is a chance that a Trojan is exposing your hard drive to the internet, resulting in unauthorized file sharing. Unlikely, but possible. There are better things to do with remote access to someone's computer than use it to download the Jumanji remake.
Use Legal Content Services to Avoid Copyright Infringement
I'm sure there are people out there that have never downloaded a copyright-protected file in their entire life. I'm not going to lie: I'm not one of them. But as internet services become better, and cater to a massive range of useful things, the need to lurk potentially dangerous download sites to find obscure Indonesian drum and bass becomes less and less.
Furthermore, protecting yourself has become easier, too. MakeUseOf certainly does not advocate downloading copyrighted material. But a VPN is excellent for protecting your personal online privacy, downloading content or not.
Get three FREE months of ExpressVPN when you subscribe for a year.