Have you ever wondered where all of the Internet spam comes from? You probably receive hundreds of spam-filtered junk emails every day. Does that mean there are hundreds and thousands of people out there, sitting around sending them out manually? Unfortunately, no. The process is mostly performed by zombie computers.
Whoa! Zombie computers? That sounds dangerous, scary, and a bit apocalyptic, doesn’t it? In a sense, that could be a true description. There are millions of zombified computers all around the world that perform terrible acts, like sending out spam and malware. It’s not the end of the world yet, but it’s definitely a hassle. And worst of all, your computer might be one of those zombies.
What Is A Zombie Computer?
We’re not talking about computers that have risen from the dead - that would be a rather fascinating investigation of its own. Instead, when we talk about zombie computers, we’re describing a computer that has been infiltrated and hijacked by a third party. Most of time, this zombification occurs through malware, Trojans, and viruses.
What happens when your computer turns to the dark side? It can be controlled by a third party - whether that third party is a single person, a group of people, or even a corporation--to do things without your knowledge. Like, for example, sending out spam emails or performing denial of service attacks.
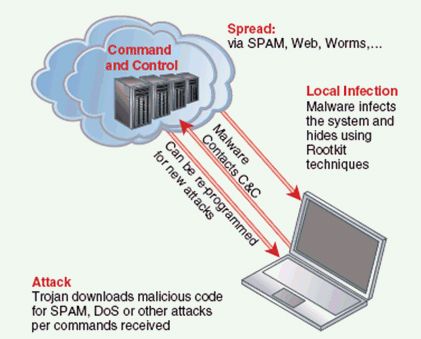
When a person has an army of zombie computers at their command, these armies are called "botnets". Botnets are used to cause mischief across the Internet because they are so difficult to trace back to the original controller. Most PC owners don’t even realize that their computers have been doing the bidding of another.
Is Your Computer A Zombie?
In most cases, zombie infections are not intentional--meaning that hackers don’t intentionally pick a specific computer to zombify. If anything, computers are zombified through contagious contact with malware links and virus-laden emails. So if your computer is a zombie, don’t immediately assume that someone is out to get you.
The thing about malware and virus infections is that they don’t want to be detected, which means it can be hard to determine if your computer is a zombie. Fortunately, there are a few ways that can point you in the right direction. Look for these symptoms on your computer:
- Zombie processes require use of the computer’s processor and network. If you’ve experienced a slowdown in your computer’s operating speed or your network speed, then you may have an infection.
- Check your email accounts--particularly their outbound messages. Botnets require bots to operate, which means that botnets are always “recruiting” new computers. This is done through the spread of malware. If you’re sending out emails that you’ve never written, then you may be infected.
- Zombie IP addresses are often put onto blacklists. If you suspect an infection, you can check to see if your IP address has been added to any blacklists. Copy this URL into your browser--http://www.robtex.com/ip/xxx.xxx.xxx.xxx.html#blacklists--and replace the “xxx.xxx.xxx.xxx” with your own IP address (use http://www.whatismyip.net).
If you have a zombie infection, the best course of action is to run a scan of your system using anti-malware and anti-virus programs. My own recommendations include Malwarebytes Anti-Malware and Lavasoft Ad-Aware Pro.
Preventing Zombie Infections
The best defense against zombie infections is a strong offense - meaning a proactive approach towards keeping yourself safe and out of malware’s way. Here are some ways to keep yourself as safe as possible:
- Patch Internet software applications as often as possible. Things like browsers, chat programs, cloud storage services, and others--all of these things require Internet access. A security vulnerability in a program can leave a hole open for malware to exploit.
- Run anti-malware and anti-virus programs regularly. This will catch problems on a regular basis, keeping your computer from being infected for too long.
- Use a firewall. I know, it can be pretty annoying at times, but a firewall is always recommended in security tips because firewalls work. Don’t neglect it.
- 7 Important Email Security Tips You Should Know About
- 5 Common Security Mistakes That Can Put Your Privacy & Money At Risk
Practice safe Internet habits and always be wary of suspicious links. When you have malware, clear it out as soon as possible. But all the same, don’t be too scared or paranoid of zombie infections. Yes, infections are annoying, but they won’t demolish your system. Just stay alert and you’ll be fine.
Image Credits: Zombie Computer Via Shutterstock, Botnet Via drdobbs.com, Malware Computer Via Shutterstock, Security Via Shutterstock