Debian is one of the most popular Linux distributions. It's solid, dependable, and compared to Arch and Gentoo, relatively easy for newcomers to grasp. Ubuntu is built upon it, and it's often used to power the Raspberry Pi.
It's also alleged to be in the grasp of America's intelligence apparatus, according to Wikileaks founder Julian Assange.
Or is it?
Speaking at the 2014's World Hosting Days conference, Julian Assange described how certain nation states (naming no names, cough America cough) have intentionally made certain Linux distributions insecure, in order to bring them under the control of their surveillance dragnet. You can view the full quote after the 20 minute mark here:
But is Assange right?
A Look At Debian and Security
In Assange's talk, he mentions how countless distributions have been intentionally been sabotaged. But he mentions Debian by name, so we might as well focus on that one.
Over the past 10 years, a number of vulnerabilities have been identified in Debian. Some of these have been severe, zero-day style vulnerabilities that affected the system in general. Others have affected its ability to securely communicate with remote systems.
The only vulnerability Assange mentions explicitly is a bug in Debian's OpenSSL random number generator that was discovered in 2008.
Random numbers (or, at least pseudorandom; it's extremely difficult to get true randomness on a computer) are an essential part of RSA encryption. When a random number generator becomes predictable, the efficacy of the encryption plummets, and it becomes possible to decrypt the traffic.
Admittedly, in the past the NSA has intentionally weakened the strength of commercial-grade encryption by reducing the entropy of the randomly generated numbers. That was a long time ago, when strong encryption was regarded with suspicion by the US government, and even subject to weapons export legislation. Simon Singh's The Code Book describes this era pretty well, focusing on the early days of Philip Zimmerman's Pretty Good Privacy, and the pitched legal battle he fought with the US government.
But that was a long time ago, and it seems like 2008's bug was less a result of malice, but rather stunning technological incompetence.
Two lines of code were removed from Debian's OpenSSL package because they were producing warning messages in the Valgrind and Purify build tools. The lines were removed, and the warnings disappeared. But the integrity of Debian's implementation of OpenSSL was fundamentally crippled.
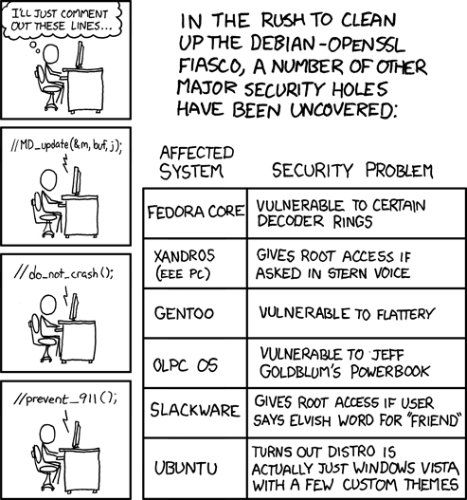
As Hanlon's Razor dictates, never attribute to malice what can just as easily be explained as incompetence. Incidentally, this particular bug was satirized by web comic XKCD.
Writing on the subject, the IgnorantGuru blog also speculates the recent Heartbleed bug (which we covered last year) might have also been a product of the security services intentionally trying to undermine cryptography on Linux.
Heartbleed was a security vulnerability in the OpenSSL library that could potentially see a malicious user steal information protected by SSL/TLS, by reading the memory of the vulnerable servers, and obtaining the secret keys used to encrypt traffic. At the time, it threatened the integrity of our online banking and commerce systems. Hundreds of thousands of systems were vulnerable, and it affected almost every Linux and BSD distro.
I'm not sure how likely it is that the security services were behind it.
Writing a solid encryption algorithm is extremely difficult. Implementing it is similarly difficult. It's inevitable that eventually a vulnerability or flaw will be discovered (they often are in OpenSSL) that is so severe, a new algorithm must be created, or an implementation rewritten.
It's why encryption algorithms have taken an evolutionary path, and new ones are built when deficiencies are discovered in order ones.
Previous Allegations Of Governmental Interference In Open Source
Of course, it's not unheard of for governments to take an interest in open source projects. It's also not unheard of for governments to be accused of tangibly influencing the direction or functionality of a software project, either through coercion, infiltration or by supporting it financially.
Yasha Levine is one of the investigative journalists I most admire. He's now writing for Pando.com, but before that he cut his teeth writing for the legendary Muscovite biweekly, The Exile which was shut down in 2008 by Putin's government. In its eleven-year lifespan, it became known for its coarse, outrageous content, as much as it did for Levine's (and co-founder Mark Ames, who also write for Pando.com) fierce investigative reporting.
This flair for investigative journalism has followed him to Pando.com. Over the past year or so, Levine has published a number of pieces highlighting the ties between the Tor Project, and what he calls the US military-surveillance complex, but is really the Office of Naval Research (ONR) and the Defense Advanced Research Projects Agency (DARPA).
Tor (or, The Onion Router), for those not quite up to speed, is a piece of software that anonymizes traffic by bouncing it through multiple encrypted endpoints. The advantage of this is you can use the Internet without disclosing your identity or being subject to local censorship, which is handy if you live in a repressive regime, like China, Cuba or Eritrea. One of the easiest ways to get it is with the Firefox-based Tor Browser, which I talked about a few months ago.
Incidentally, the medium in which you come to find yourself reading this article is itself a product of DARPA investment. Without ARPANET, there would be no Internet.
To summarize Levine's points: since TOR gets the majority of its funding from the US government, it is therefore inexorably linked to them, and can no longer operate independently. There are also a number of TOR contributors who have previously worked with the US government in some form or another.
To read Levine's points in full, have a read of "Almost everyone involved in developing Tor was (or is) funded by the US government", published on the 16th of July, 2014.
Then read this rebuttal, by Micah Lee, who writes for The Intercept. To summarize the counter-arguments: the DOD is just as dependent on TOR to protect their operatives, the TOR project has always been open about where their finances have come from.
Levine is a great journalist, one I happen to have a lot of admiration and respect for. But I sometimes worry that he falls into the trap of thinking that governments - any government - are monolithic entities. They aren't. Rather, it's a complex machine with different independent cogs, each with their own interests and motivations, working autonomously.
It's totally plausible that one department of the government would be willing to invest in a tool to emancipate, whilst another would engage in behavior that's anti-freedom, and anti-privacy.
And just as Julian Assange has demonstrated, it's remarkably simple to assume there's a conspiracy, when the logical explanation is much more innocent.
Have We Hit Peak WikiLeaks?
Is it just me, or have WikiLeaks's best days passed by?
It wasn't long ago that Assange was speaking at TED events in Oxford and hacker conferences in New York. The WikiLeaks brand was strong, and they were uncovering really important stuff, like money laundering in the Swiss banking system, and rampant corruption in Kenya.
Now, WikiLeaks has been overshadowed by the character of Assange - a man who lives in a self-imposed exile in London's Ecuadorian embassy, having fled from some pretty severe criminal allegations in Sweden.
Assange himself has seemingly been unable to top his earlier notoriety, and has now taken to making outlandish claims to anyone who'll listen. It's almost sad. Especially when you consider that WikiLeaks has done some pretty important work that has since been derailed by the Julian Assange sideshow.
But whatever you think of Assange, there's one thing that's almost certain. There's absolutely no evidence the US has infiltrated Debian. Or any other Linux distro, for that matter.
Photo Credits: 424 (XKCD), Code (Michael Himbeault)