"I don't get viruses because I run Linux!"
We've all heard this statement in some way shape or form. The fact of the matter is, that statement is nothing but a myth. Another common misconception is that privacy is entirely taken care of by Linus Torvalds and his team of ninja turtles.
In truth, all operating systems, combined with the people that use them, offer plenty of risks and vulnerabilities that can be exploited.
The good news is that there are some really basic steps to take to try and mitigate these risks. While you should never be lulled into a false sense of security, these steps will give you better peace of mind. They may even remind you of something so simple that it was overlooked at the time of install. Let's jump right in, shall we?
1. Password Protect Your Account
This should be a required step at the time of install. It does help however, to ensure you use a strong password. Not just strong in complexity, but in length as well. If you are an IT administrator either at work or (by default) at home, ensure you enforce strict password rules. All it takes is one vulnerable machine on your network which could lead to the apocalypse.
As ridiculous as this sounds, make sure passwords aren't written down either. Finding a post it stuck to a monitor with password on is not uncommon. As complex as your password needs to be, it should also be relatively easy to remember. Using anagrams or initialisms could be useful here. For example, "O say can you see, by the dawn's early light." could be condensed into something like "Oscys,b7deL." (Apologies if that is actually your password.)
You can see how easy it is to start forming a strong password that can be easy to remember and complex at the same time.
2. Encrypt Your Data
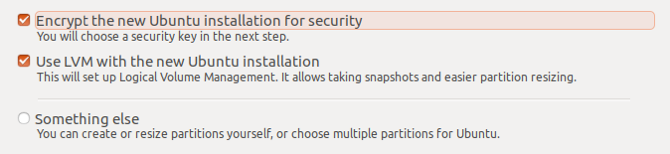
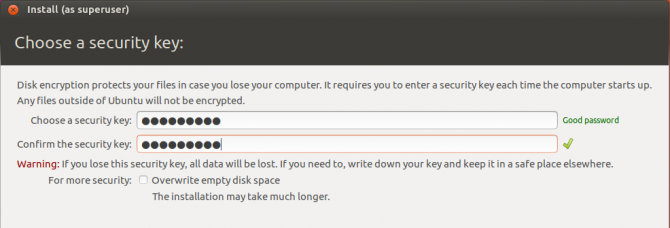
Encrypting your data is invaluable. In the unfortunate event that your device is stolen, the thief could remove your hard drive and plug it into another device. This would give them access to your archive of cat photos. Ubuntu offers two levels of encryption. Encrypting your entire drive or just encrypting your home folder.
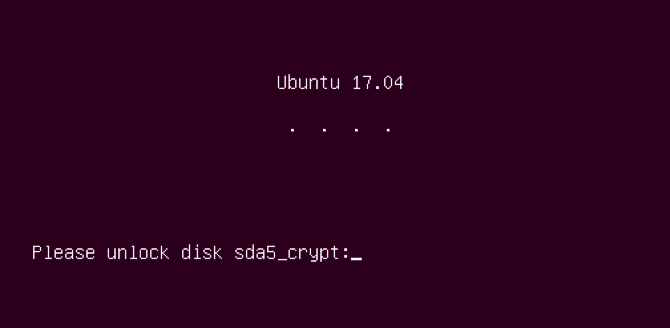
The above options will encrypt your entire drive with a security key. You will be required to enter the security key every time the computer starts up. This way, no one will be able to browse your device, let alone view your files.
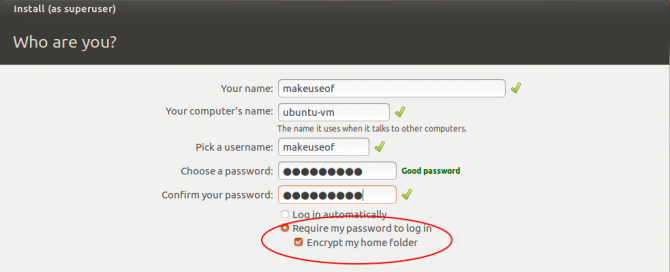
Encrypting the home folder does exactly that. Rather than encrypt the rest of your system, it secures just your personal files. Note, however, that there is a trade off with encryption in the form of CPU overhead. Fortunately, modern computers shouldn't bat an eyelid at this overhead.
While you can choose to both encrypt your entire drive and your home folder, you need only choose one. Always ensure your backup routine is up to date, however, just in case things go awry.
3. Screen Lock
This is something that should be treated with a healthy serving of impulsiveness. Your screen lock needs to be an extension of your habitual nature. This is even more important in situations where you're in a public place or even a shared office. The keyboard shortcut to manually lock your screen on Ubuntu is as simple as Ctrl + Alt + L.
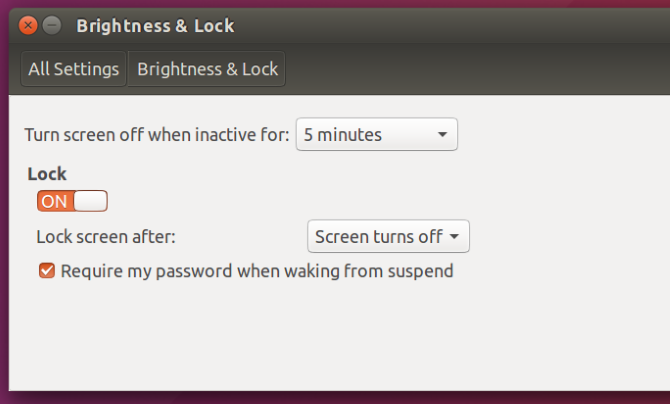
As a fallback however you should ensure your screen locks when the screensaver is activated. You can find these settings by navigating to Brightness & Lock under Settings in Ubuntu.
Some may find the added hassle of continuously typing their password in when returning to their computer slightly ridiculous. This tends to be a common feeling right up to the point where unauthorized access is gained. Don't let it be game over.
4. Remove Dead Weight
Having a lean machine has many benefits. Keeping only applications that are necessary will ensure maximum efficiency. It also reduces the risk of a poorly written application being the magic door that will expose vulnerabilities.
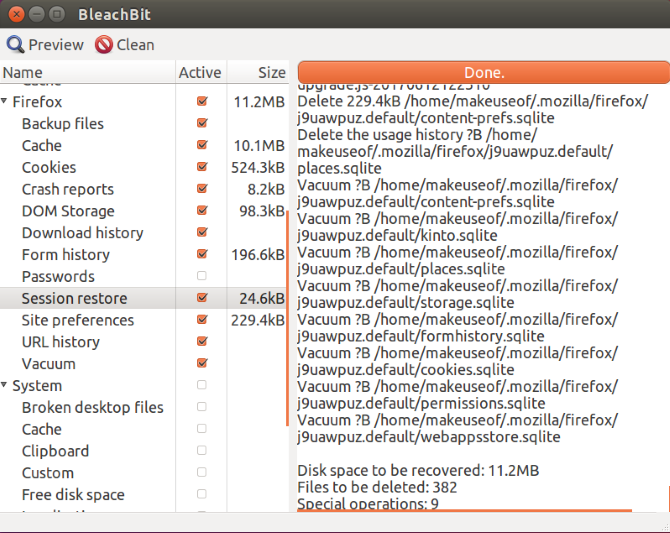
After you've perused the installed applications on your machine you could use a tool like BleachBit to do some deep cleaning. It can quickly delete cookies, free your cache, and obliterate temporary files. All while freeing up some disk space.
5. Beware the Rootkit
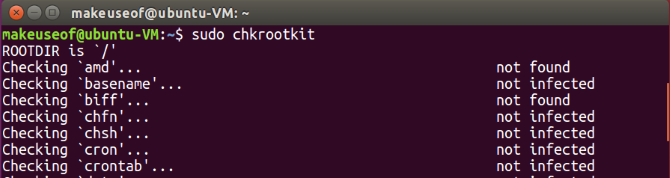
Rootkits are the scourge of the earth. Harbouring your device's performance is the least of your worries. Enter chkrootkit. Listed in the Top 100 Network Security Tools survey, chkrootkit locally checks for signs of a rootkit. To install chkrootkit run the following command:
sudo apt-get install chkrootkit
The install takes only a few seconds, and you can run chkrootkit by typing the following:
sudo chkrootkit
It may take a while to complete, but once the chkrootkit scan has done its thing, you'll know whether your Linux PC is secure or not.
6. Put a Leash on Remote Access SSH
If you use remote access SSH, you may have realized that there are some individuals with nefarious intentions already trying to breach your system. These malicious individuals use port sniffers to check which machines on the internet have the SSH port open. They then fire common usernames and passwords at the devices, hoping to gain access.
How can you stop this? Fortunately, security against remote access SSH can be accomplished with a few simple tweaks.
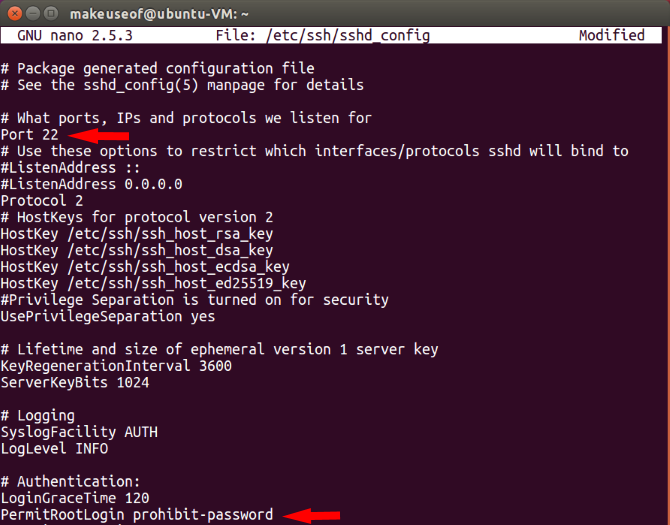
One of the first things you should do is restrict SSH login to using an SSH key-pair as opposed to a password to login. You should then change the default SSH port and disable root login. Simply open your SSH config by typing:
sudo nano /etc/ssh/sshd_config
Once the file is open look for the lines that say Port and PermitRootLogin. You should change the port to an uncommon number and one that isn't currently being used by your system. Look to the next point in the article on how to check which other ports are currently being used by other programs. PermitRootLogin can be set to prohibit-password if you still wanted to login via root using an SSH key-pair.
Once you have made said changes, you can restart your SSH service and bask in it's new found private glory by running:
sudo service sshd restart
7. Disable Unnecessary Daemons
You may have chosen a few services at the time of install that you won't actually need. These daemons could be listening on external ports. If you have no need for these services you could simply turn them off. This will help protect your privacy along with the possibility of improving your boot times!
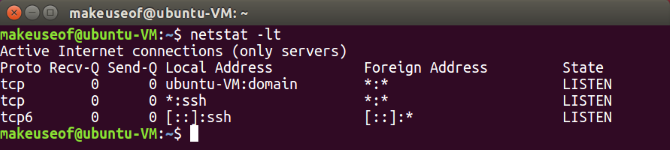
When you're ready to check who is listening run:
netstat -lt
8. Ensure Your System Is Updated
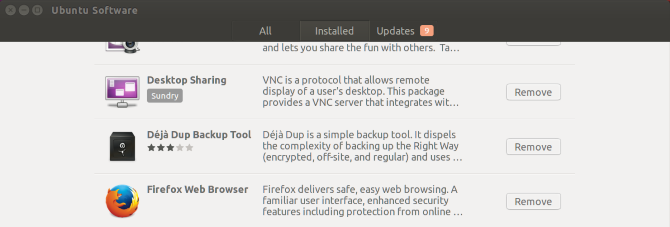
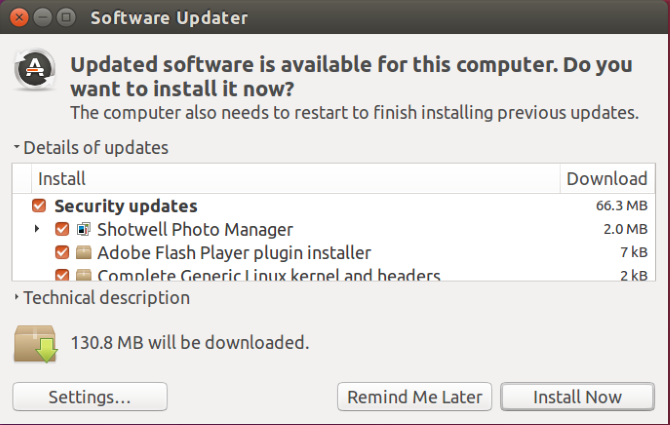
At the point of installing Ubuntu, you would have noticed an option to download updates during the install. The reason for this would be that since the time that the base downloadable version of Ubuntu was made available, there may have been a few system and critical security updates. This is a sign as to how essential and important it is to ensure your system is kept updated. If you want to be selective as to which updates are applied you can grab the Software Updater from the Ubuntu Software application.
Once you launch Software Updater it will break down the updates into Security updates and Other updates. The absolute minimum should be to ensure that all the security updates are always kept up to date. Other updates will include important bug fixes and Ubuntu base updates if they are available.
9. Use a VPN
There are a plethora of VPN options available right now. Many of which have Linux clients natively available. A VPN will cloak and encrypt your internet traffic. This ensures that all your online activity is seemingly scrambled to anyone trying to intercept your traffic. Additionally, some VPNs can manipulate or spoof your IP address.
In short, this makes you appear to be in a different location or country. This can prove useful in a number of scenarios, including online gaming.
10. Green Is Good
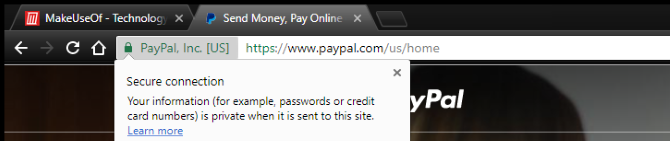
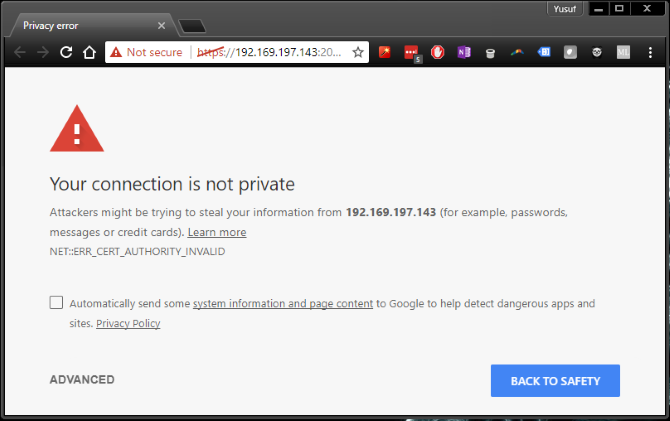
This is more of a best practice regardless of which device you're using. It is such an important point however, that we absolutely couldn't leave it out. If you're on a website that requires you input some personal information and or payment details, make sure to look out for the secure connection icon in the browser window. This is normally denoted by a green padlock icon on the left of the websites address or URL. This icon means that the website you are visiting has a valid Secure Socket Layer (SSL) certificate. This encrypts and secures all the traffic between your browser and the website.
If a website has an invalid SSL certificate you may see a warning similar to the screenshot below. You will notice the Not Secure in place of the almighty green padlock indicating that you should now proceed with the utmost caution.
If you do proceed to a website that is unsecure, make sure not to type in any personal information, passwords or payment details.
Does Privacy Matter If I'm Not Doing Anything Wrong?
Glenn Greenwald addresses this question in his 2014 TED talk. The example given is that there is nothing wrong with singing and dancing, yet some choose to do it in private because they don't want to do it in front of others. You may not have anything incriminating to hide, but that doesn't mean you shouldn't be allowed to hide when you want to sing and dance. Whether it be someone invading your privacy for malicious purposes or just a sense of freedom from our lives being removed, privacy matters.
While this article covers privacy and security, the point of vigilance should be echoed throughout. Getting into the habit of security best practices means your personal and confidential information is kept safe, and away from prying eyes.
Have you come across any ways which helps you protect your privacy? What are your thoughts on your information privacy in today's Linux world? Let us know in the comments below!
Image Credits: maimu/Shutterstock