Internet privacy has been under sustained attack over recent years. Thanks to the heroic efforts of whistleblowers such as Edward Snowden and organizations such as Wikileaks, we are all wiser and can now take precautions to protect our right to privacy.
The list of organizations and companies that have access to your data or want to spy on you just keeps growing. As we rant about the NSA and other similar national agencies, Google continues to pervade our lives and collect loads of personal data with its numerous products. Facebook was also in the news lately for all the wrong reasons with its creepy psych experiments.
The browser you use is a key factor in protecting your privacy. Out of the box, Google Chrome and Firefox run JavaScript and accept cookies and while Internet Explorer blocks third party cookies, it also runs JavaScript. So, the most popular browsers don't do a great job at protecting your privacy. You could always use the private browsing feature that now comes with all the major browsers but advertisers and government agencies would still be able to track you.
We searched around and came up with the following three browsers that are designed to make your browsing as private and secure as possible.
The Tor Browser
In documents leaked by Wikileaks, the NSA has described Tor as "the King of high secure, low latency Internet anonymity" with "no contenders for the throne in waiting". Coming from the world's pre-eminent spying organisation, that is serious stuff! Logically, this should be your first stop when shopping around for a browser to protect your privacy.
Tor was originally a project of the United States Naval Research Laboratory which probably explains why it's built like a fortress. In fact, Onion Routing, the pre-dominant technology that Tor uses was patented by the US Navy in 1998. Today, Tor is run by the Tor Project, a research-education non-profit organization.
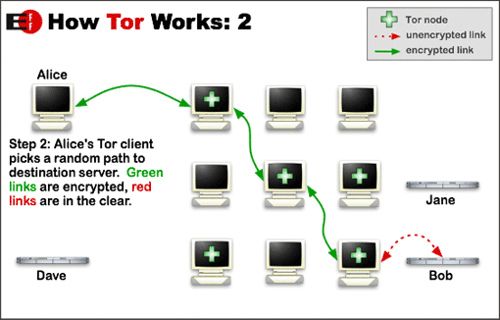
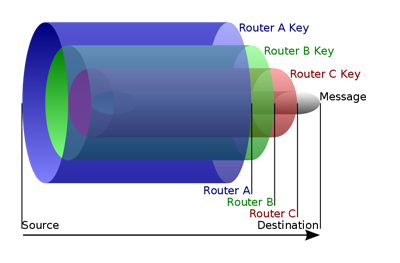
Tor protects personal privacy and the ability to conduct confidential communication. JavaScript and cookies are disabled on Tor by default. The browser directs Internet traffic through a free international volunteer network consisting of more than 5,000 relays. Each message transmission is "wrapped" in several layers of encryption and each layer is "unwrapped" (decrypted) like an onion by a relay in the circuit. A receiving node can only view the last intermediate node and the recipient relay in the circuit. The final node decrypts the innermost layer of encryption and sends the message to its final destination.
Tor is built using; a modified version of Mozilla Firefox, NoScript and HTTPS Firefox extensions, the TorButton, TorLauncher and TorProxy. It can be run from removable media and is available for Mac OS X, Windows and Linux. To learn more about the Tor browser, please read our Unofficial User's Guide to Tor.
Epic
If you are accustomed to the Google Chrome user interface and you aren't too concerned about anonymity then Epic is the browser for you. Epic comes with the same Google Chrome UI that many of us have fallen in love with.
On the download page is a list of 11 privacy leaks that Epic blocks. Out of the box, it blocks sites that track you and advertisements. It also offers a comprehensive default privacy browsing mode that doesn't store cookies, cache, history, auto-fill and any other personal data that other browsers store by default. Epic also deletes session data once you close it. Internet searches are routed via proxy to prevent a history of your searches being recorded using your IP address.
Another plus with the Epic browser is that it offers one-click proxy set-up via a plug icon on the address bar. This switches you to a US IP address and hence allows you to access content only available to US audiences such as Hulu videos. You can also set up an encrypted data connection when on a Wi-Fi network.
Epic also has nice little feature that allows you to check which service is tracking you on other open browsers on your computer. The feature is available in a new tab window.
While Epic is not as comprehensive as Tor, think of it as a highly improved version of Chrome's incognito mode.
The Pirate Browser
The Pirate browser is a creation of the guys behind The Pirate Bay (TPB), the world's most visited torrent directory. Like Tor, it is also built on a modified Firefox version and includes a modified Vidalia Tor client and the FoxyProxy Firefox addon.
The browser was originally built to bypass Internet censorship in countries where TPB is blocked but it also offers privacy features that you won't find on other browsers such as the additional settings in the Options window, giving you the option of telling sites whether you want to be tracked, or simply tell them nothing at all. In Firefox, the only option available is to "Tell websites I do not want to be tracked."
A Big Caveat
At the moment, Tor is hands down the King of Internet privacy. If you are really passionate about your privacy and want a "complete " solution, then Tor is the way to go. However, if your only concern is websites tracking you and selling your data, then you could go for a browser like Epic. If you merely want to circumvent blocked websites and have some additional privacy options, over and above those offered by your normal browser and privacy extensions, then The Pirate Browser is good enough.
Now, I'm sorry to rain on your parade but no browser can offer 100% Internet privacy. Even Tor cannot protect you from certain types of vulnerabilities. The best example of this is the FBI's recent take-down of the largest child porn site operating within the deep web of the Tor network. This was achieved by injecting malware into the browsers of users and voila, the FBI was able to obtain the IP addresses of site members. The lesson here is that when dealing with a government that has limitless time and resources, and lots of commitment you don't stand a chance especially if your interest in privacy is motivated by criminal intent.
What's your take on Internet privacy? Have you ever used any of these browsers and how did it work out for you? Please let us know in the comments below.
Image Credit: Electronic Frontier Foundation, Wikimedia Commons