Everyone with an Android device should know that your private information isn’t treated as private. For example, making an app purchase may expose personal contact information, including one’s name, physical address and email address, to developers. Another major debacle occurred when Path Inc. began lifting contact information from its users’ phones. In response to these privacy breaches, some legislators announced plans for legal action: California’s Attorney General, Kamala Harris, recently announced an agreement with major technology firms to improve user privacy standards, particularly on handsets.
However, at present, few users know of the potential security and privacy concerns. Few even know the difference between Android and iOS’s security measures. For example, the Android operating system’s security differs from the iPhone OS in one major regard: Apple exercises very strict quality control guidelines for apps, whereas Android permits a broader range of software. Android apps request “permission” from users to access your sensitive data. Unfortunately, Google doesn't fully explain the potential security risks that that some permissions present users. What we don’t know can hurt us, particularly when we install apps from the dark nether-regions of the internet.
This article explains how seven potentially deadly app permissions might hurt you and how best to avoid such calamitous installations.
What is a Permission?
Chris Hoffman explained in detail what app permissions are — permissions allow apps to access either the hardware features of a phone, such as the camera, or a user’s personal information. The diverse nature of this system permits a great variety of amazing software. For apps like Google Now to work properly, it must access tremendous amounts of data, as well as your phone’s GPS and data components. Most apps request this data without ill intent. However, a growing number of malicious apps can use these permissions in lethal concert with one another.
For the penultimate source on Android permissions, check out AndroidForums.com user Alostpacket’s comprehensive guide. Another handy source is Matthew Pettitt’s analysis of the top-twenty Android apps and their requested permissions. Both of these works contributed greatly to this article.
The Permissions
#1 Authenticate accounts: This permits an app to “authenticate” sensitive information, such as passwords. What makes it extremely dangerous is that a rogue app with this capability can phish a user’s password through trickery. The vast majority of these kind of apps legitimately come from big developers, such as Facebook, Twitter and Google. Because of the potential for harm, however, look very carefully at the apps you grant permission to.
#2 Read sensitive log data: This permission allows an app to access your handset’s log files. For example, the CarrierIQ scandal, an app used in most phones secretly mailed your phone’s log files back to its developer. However, it turned out that the app sent back logs which included keystrokes—meaning your passwords and logins were included in this file. While the company CarrierIQ maintained that these logs weren’t used maliciously (something we must take at their word), we have no idea how securely they stored this data. Essentially, log files can contain extremely sensitive information.
#3 Read contacts: Read Contacts allows an app to read all of your contacts. Often, malware-like apps will attempt to take advantage of unwary users in indirect ways. For example, after granting a rogue app this permission I received an email with attached files from a friend that I correspond frequently with. The attached files were some kind of malware. The email had been spoofed!
#4 Write secure settings: Allows an app to read and write system settings. I’ve never seen an app request this permission before, and I’m pretty sure that Google heavily polices apps using this feature. However, certainly there exist rogue software with this ability. For those with rooted phones, you should avoid apps that request this permission like they’ve got an infectious disease. It’s possible that they do have an electronic analog.
#5 Process outgoing calls: The ability to monitor the details of outgoing calls, such as phone numbers and other kinds of contact information, should belong exclusively to VOIP apps. Programs making such requests, not dealing explicitly with outgoing or incoming calls, are 'over-permissioned'.
#6 Send SMS: You should use caution in granting apps access to send SMS or MMS. There exist a number of companies that can tack on charges to individual SMS—you of course, would receive the bill for using such services. Unless the app specifically requires access to your SMS, this permission should not be permitted.
#7 Read social stream: Since the recent boom in social media, and the obvious privacy concerns, Google incorporated a permission that allows apps to read information gleaned from your social feeds. Considering the vast amount of personal information that’s being produced through social networks, the wrong app might be able to take advantage of this. For example, many of the average user’s security questions might be picked up from their social media feed.
How to Interact with Permissions
Some simple guidelines for avoiding potential problems:
- Make sure you’re installing apps from trusted sources. Even apps in the Play Store can potentially possess malware-like properties. In particular, read the reviews of the app and check out the developer on Google to make sure they have a clean reputation.
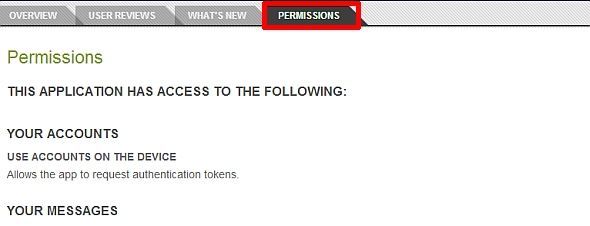
- Avoid installing apps requesting excessive permissions. For example, if a game that involves shooting unhappy feathered creatures at brick walls ever attempts to gain access to your contacts list, you should question their motivation. To check the permissions of apps before they're installed, go to the app's Play Store page. The Permissions tab is visible just below the banner for the app. Keep in mind that your phone's motion sensors can be a security risk, too. That's why it's also important to monitor hardware permissions closely.
- Remove apps that have no reasonable excuse for requesting certain permissions—also known as over-privileged apps. You can identify errant apps using software like Permissions Explorer, which can look at the apps on your device, filtered by permission. An alternative is to upload your apps to Stowaway, which performs an analysis as to whether or not the app requests too many freedoms with your data. However, Stowaway might present an issue to users not familiar with managing APK files, the Android executable file. Matt Smith did a great write-up on an alternative software, known as No Permissions, which illustrates what an over-privileged app looks like. Another option is aSpotCat. If you have root access, there's the Permissions Denied app.
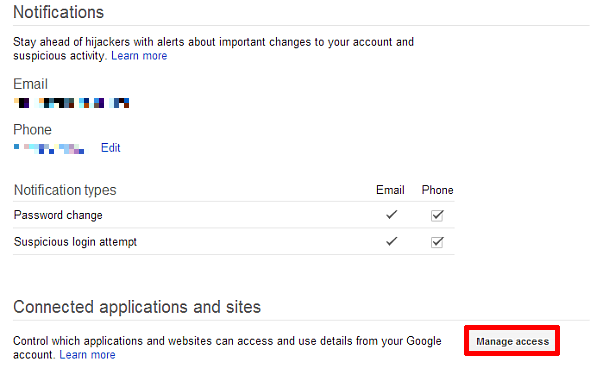
- Visit Google’s account page to see what apps you've given account access to. Remove those that you do not recognize—however, you should utilize discretion in this area as it may cause certain apps to cease functioning. To get there, simply scroll to the bottom of the accounts page and click on Manage access. After that, you may revoke access to any app, from any platform.
Conclusion
When I was targeted by malware, the hackers knew my email address, my friends email addresses, and the frequency with which I contacted them. This greatly increased their chances of successfully phishing my account password or installing some terrible virus on my handset. My ignorance could have caused great harm.
In the wake of several user privacy and security disasters we should all focus on just exactly what terms and conditions we are agreeing to and what our phones might be doing with our private information. Given the potential for coordinated attacks from hackers utilizing information gleaned from over-privileged apps, the need for increased user vigilance has never been greater. And as it has always been throughout time, knowledge is your best protection against exploitation.
Image Credits: Parchment via MorgueFile.com; Robot via MorgueFile.com; Stop via MorgueFile.com