October is National Cyber Security Awareness Month (NCSAM), a joint effort between the U.S. government, industries, and security-centric organizations. It's a good time to pause, take a moment, and check if you are using safe practices online.
Internet miscreants are trying to get to your data all the time. You need to first check if your account has been compromised. Then you have to secure it against intruders.
You are making it far too easy for hackers if you don't take these five simple steps to strengthen your online security. They're free, they take less than five minutes each, and you will rest easy knowing you're protected.
1. Leaked Source [Broken URL Removed] (Web): Check If Your Account Has Been Compromised
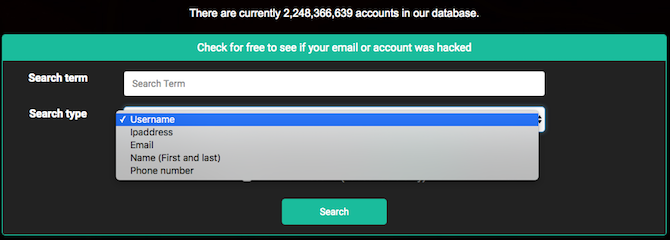
We often hear of malicious elements getting their hands on private accounts and passwords. Even a large service like Gmail has leaked 42 million account credentials. With so many online services, how do you know whether your account credentials are already known?
Leaked Source is an online database of all leaked emails, usernames, passwords, IP addresses, and other account-sensitive information. Go to the site, search for your email, username, name, phone number, or IP address. In minutes, Leaked Source will tell you if you figure on any of the leaked lists so far.
2. Lastpass Security Challenge (Chrome, Firefox, Safari, Opera): Update and Secure Your Passwords
You probably don't update your passwords nearly as often as you should. If you wait for your service provider to issue a message imploring you to change, that's already waiting too long. More importantly, since password leaks happen so commonly these days, you need to make them more secure as well.
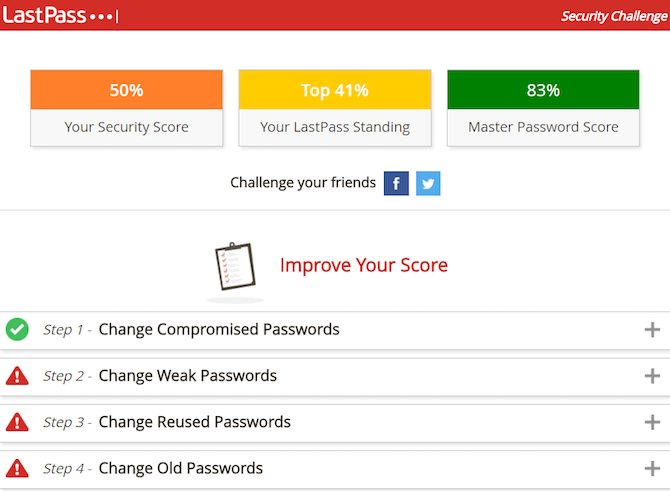
The LastPass Security Challenge is the perfect exercise to get this done. You'll need to use LastPass, the fantastic password manager, as an extension on your favorite browser. Go to Menu > More Options > Security Challenge to begin.
There are four basic steps to the challenge. You first change any compromised passwords. Then you change your weak passwords. Then you change your reused passwords. And finally you change your old passwords. It seems like a lot, but doing it through the LastPass extension, it took me about five minutes to finish the whole thing.
Download -- LastPass extension for Chrome, Firefox, Safari, or Opera
3. Two Factor Auth (Web): As Essential as Passwords in the 21st Century
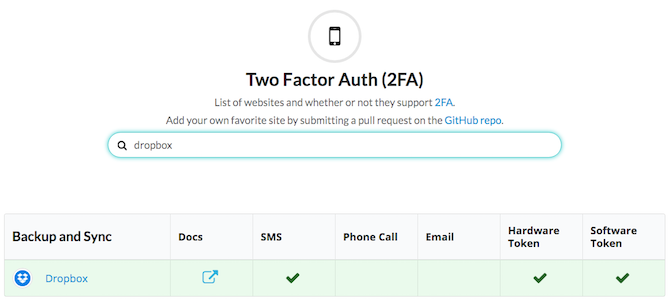
Everyone has told you this but you still haven't done it, have you? Two factor authentication (2FA) is the safest online security lock right now. Yet, most people don't use it. It's time to change that. And Two Factor Auth is the website to do it from.
The site lists all the websites that support 2FA. You can browse them by category, or use the search bar. It displays each site's method for the secondary password token -- through SMS, email, phone calls, or other apps. Click the site's name to be taken directly to enable 2FA.
Yes, even two-factor authentication can be hacked, but that doesn't mean it's useless. It's a major stumbling block for hackers. If you secure yourself with the LastPass Security Challenge and then enable 2FA, you'll be unimaginably more secure.
4. VirusTotal (Web, Chrome, Firefox, internet Explorer): Scan Any File Before You Download
The easiest entry point you can give hackers is to download a malicious file to your computer. Once it's on your hard drive, several barriers of protection have already been broken. An oldie but a goodie, VirusTotal's job is to stop that.
Before you download any file on the internet, run it through VirusTotal. You can upload files to it (up to 128 MB), share a direct URL, or even search through VirusTotal. The site will will thoroughly scan your link or file and make sure it is completely safe before you download it. No wonder it's one of the best antivirus tools for browsers.
The site works flawlessly, but you should obviously install the VirusTotal extension since it's a lot easier than visiting the site. Importantly, there's a VirusTotal extension for internet Explorer too, which most other such services don't support.
Download -- VirusTotal Extension for Firefox, Chrome, or IE (Free)
5. Stay Safe Online (Web): Learn All About Online Best Practices
A big part of online safety is staying updated about new threats. The more aware you are, the better protected you are. The Stay Safe Online organization is one of the parties involved in NCSAM. Here, you can learn everything you need to about online safety practices, whether you're an individual or a business. Plus, it also has resources to enable you to reach out to others and help them.
From kids and the inherent risks of sexting to free security check-ups and tools to consider your business's risks, you'll get it all here. Stay Safe Online is regularly updated with new major vulnerabilities and online scams to watch out for.
This is one site you'll want to check to stay on top of security news.
How Safe Are You?
It's surprising how many people ignore these basics of securing yourself online. When you're vigilant about double-locking your doors at night, why won't you double-lock your email with two-factor authentication? It boggles the mind.
How well did you score on this test? Have you already taken all five of the first steps to online safety?