Another month, another online security flaw. This time, the vulnerability is one that affects your browser, and it isn't limited to any one browser, nor any single operating system. Are you affected by the FREAK security bug? How can you find out, and what can you do to protect yourself?
What is the FREAK Security Vulnerability?
Discovered through cooperation between researchers from IMDEA, INRIA and Microsoft Research, FREAK (Factoring RSA Export Keys) exploits a weakness in the SSL/TLS security protocols. The export cipher weakness – apparently put in place at the behest of the surveillance-happy NSA – can now be easily exploited, thereby enabling anyone with a reasonably powerful computer to crack public keys. Worse still, when combined with a man-in-the-middle attack (as with the problem with Lenovo bundling Superfish malware on its laptops), the vulnerability can be used to hack websites and their visitors' browsers.
Put simply, this is a bit of a problem, not only for users, but for website owners too. Problem sites include online stores and, ironically given the origins of the flaw, US government websites.
Ars Technica's Dan Goodin called this vulnerability "potentially catastrophic" while Washington Post's Craig Timberg states:
"The problem illuminates the danger of unintended security consequences at a time when top U.S. officials, frustrated by increasingly strong forms of encryption on smartphones, have called for technology companies to provide 'doors' into systems to protect the ability of law enforcement and intelligence agencies to conduct surveillance."
Who is Affected?
A list of affected websites, accurate as of March 6th, includes businessinsider.com, groupon.com, zdnet.com, talktalk.co.uk, motorola.com, Santander.com.br, and many others. It is particularly ironic that some of those sites affected are those reporting the vulnerability. This accounts for 9.5% of the host servers for Alexa's top 1 million websites, with 26.3% of servers worldwide still vulnerable to this problem.
But as you should have gathered by now, it isn't only websites that are affected by the FREAK bug. Users are too.
Working out who is affected is simple. If you're using Windows, you're affected, but before you non-Windows users attempt to stifle your snorts of derision, read this: browsers on other platforms are also affected.
Are YOU Affected by FREAK?
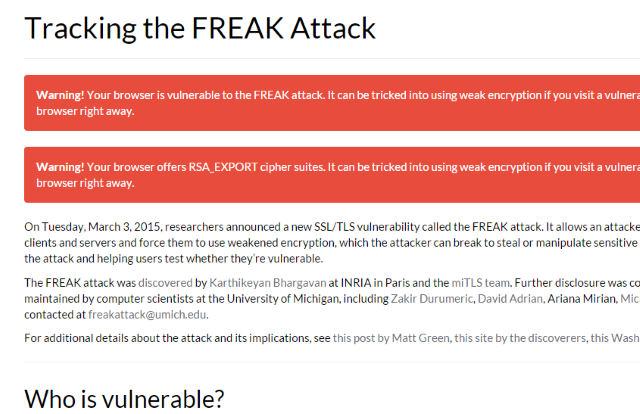
To find out if the FREAK security bug affects you directly, head to freakattack.com/clienttest.html (no user information is required) and read what it tells you about your browser. If you're affected you'll spot a couple of warnings highlighted in red, as illustrated, and a list of the cipher suites that can be hacked using the vulnerability.
Vulnerable Browsers
Six browsers are affected, across five platforms, Mac OS X, Blackberry and Linux included.
- Internet Explorer users should observe the Microsoft Security Advisory before proceeding. Until a fix is rolled out, it is simpler to avoid using IE, as the workaround is potentially destructive to some tasks.
- For Chrome on Mac OS, a patch is available now, so you can update OS X the usual way to deal with this.
- Safari users (on OS X and iOS) will need to wait, making this a good opportunity to switch to Chrome or Firefox.
- Worryingly the stock Android browser and Chrome for Android are affected by this, with no sign of any updates as yet. Despite this, you shouldn't be using the stock browser as it is susceptible to various other problems.
- Blackberry users – of which we know there are still many, if the reaction to my week with a Blackberry Z10 is anything to go by – are also affected.
- Opera users on Mac OS X and Linux are susceptible to the FREAK vulnerability, with no indication at the time of writing of any impending fixes.
As you should have noticed, there is one clear winner here: Mozilla Firefox. If a version is available for your operating system, we recommend that you switch. That said, Chrome for Windows appears to be safe as well.
Take Action Now: Kill the FREAK Bug
If there is to be any silver lining to all of this, it's that the main online stores have remained unaffected, and that Mozilla Firefox owners – long portrayed as a dying breed in the face of Google Chrome – can feel vindicated for sticking with the more secure option.
Some behavioural change is required. Drop Internet Explorer if you're on Windows, and switch to Firefox on any platform where it can be used (after all, it's arguably more flexible than Google Chrome). As ever, you should maintain an active firewall, whether built into your operating system or provided by a trusted third party company.
Finally, make sure you accept and install all operating system updates over the coming weeks in order to kill the FREAK security bug.
Leave your questions in the comments.
Featured Image Credit: Woman holding laptop via Shutterstock
Image Credit: HTTPS and Lock Symbol via Shutterstock, Alexander Supertramp / Shutterstock.com,