We've been consistently clear on this website -- Apple hardware is no longer a safe haven from hackers, malware, ransomware, and other cyber-threats.
Whether you use Apple hardware such as Macs and iPhones, or software such as QuickTime, without proper precautions you are just as vulnerable as people who rely on Windows and its associated programs.
With that in mind, we take a look at some of the latest threats you need to be aware of…
QuickTime
The biggest Apple-related news story of 2016 is arguably the company's decision to end support for its Windows version of QuickTime.
QuickTime is Apple's multimedia playback software. It's been around for more than 25 years and comes preinstalled on all OS X-powered machines.
The discontinuation of the Windows version shouldn't come as a surprise. The last release -- QuickTime 7 -- hit the market 11 years ago, and Apple has been doing incremental updates ever since (by way of comparison, Macs now run version 10.4).
The story was catapulted into the headlines in early April 2016 when researchers at Trend Micro found two critical vulnerabilities. Apple, which had already announced that support for the Windows version would be discontinued, confirmed the vulnerabilities would not be patched.
Both the flaws are "heap corruption remote code execution vulnerabilities". In layman's terms, it means a hacker could remotely compromise a machine if a malicious video is played by the user.
Even the US government has got involved in the situation; the Department of Homeland Security's U.S. Computer Emergency Readiness Team (US-CERT) said the following:
"Computer systems running unsupported software are exposed to elevated cybersecurity dangers, such as increased risks of malicious attacks or electronic data loss. Exploitation of QuickTime for Windows vulnerabilities could allow remote attackers to take control of affected systems.
Potential negative consequences include loss of confidentiality, integrity, or availability of data, as well as damage to system resources or business assets. The only mitigation available is to uninstall QuickTime for Windows."
Worryingly, it's not so simple for some users -- especially those who rely on Adobe's software. Adobe After Effects (the industry-standard tool for video compositing) relies on QuickTime, and the company announced other products were also affected.
"Adobe has worked extensively on removing dependencies on QuickTime in its professional video, audio and digital imaging applications and native decoding of many .mov formats is available today.
"Unfortunately, there are some codecs which remain dependent on QuickTime being installed on Windows, most notably Apple ProRes. We know how common this format is in many workflows, and we continue to work hard to improve this situation, but have no estimated time frame for native decode currently."
It means that Creative Cloud users currently face a stark choice -- keep QuickTime installed and open yourself up to security threats, or delete it and lose the ability to edit videos.
It's a disaster.
Apple ID Scam
A user's Apple ID is the main way in which they interact with Apple's services and products. The App Store, iTunes Store, iCloud, iMessage, the Apple Online Store, and FaceTime all rely on it.
It's very important, therefore, to be vigilant against unauthorized access - a person who has your credentials would have access to your device backups, contacts, photos, and more.
Unfortunately, hackers have realized its value.
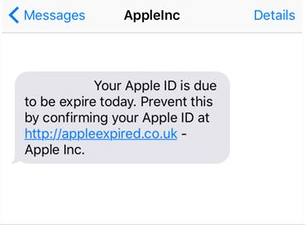
In early April, people started receiving text messages from "AppleInc". The message warned that the person's Apple ID was about to expire and that they needed to follow a link to resolve the issue.
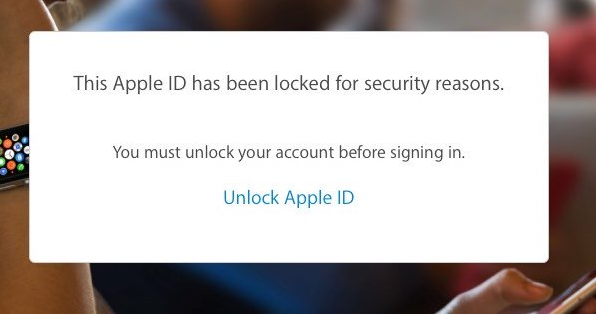
Someone who clicked the link would be redirected to a very convincing mock-up of the Apple ID homepage and be prompted to enter their Apple ID login. If they did so, they would be presented with a screen saying that the account was locked and further details were needed. Unsurprisingly, these "further details" included name, address, date of birth, phone number, and credit card details. It even offered a "security question" -- asking for your mother's maiden name, driving license number, or passport number.
Luckily, there are a few things you can do to make sure you stay safe from this particular scam:
1. Be vigilant – if a message looks suspicious, it probably is.
2. Check the URL. Official Apple services will almost always include the company's actual domain (Apple.com). The genuine Apple ID page is AppleID.Apple.com.
3. If in doubt, contact Apple directly via telephone.
Mac OS X Ransomware
In March we learned about the KeRanger ransomware. According to researchers at Palo Alto Networks, it was the first recorded use of functioning ransomware against Macs and the OS X operating system (a previous ransomware discovered in 2014 -- called FileCoder -- was unfinished).
For those who don't know, ransomware works by restricting access to a computer and demanding the affected person pays a fee to the malware's developers to remove the restriction. It is thought that hackers are making hundreds of millions of dollars per year off such scams.
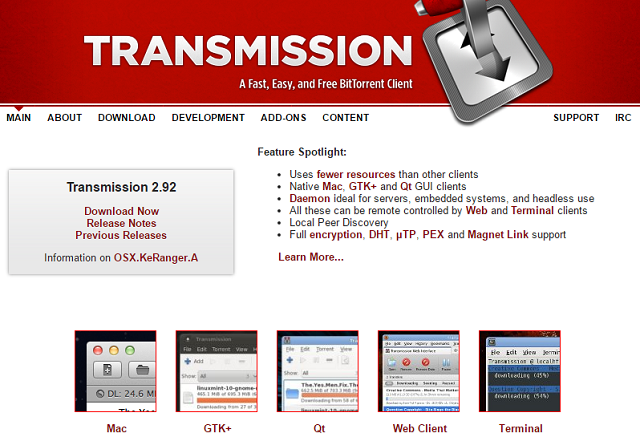
The KeRanger ransomware spread from an infected installer for the popular BitTorrent client, Transmission. Due to the open-source nature of the software, experts believe the official website was compromised and the installation files were replaced by re-compiled malicious versions, though it has not been proven.
It worked by connecting with its command and control servers over the Tor network, after which it began encrypting documents and data files on the system. Once finished, it demanded $400 to unencrypt the files.
There are a couple concerning aspects of this particular virus. Firstly, it was signed with a valid Mac app development certificate, thus allowing it to easily bypass Apple's Gatekeeper protection system. Secondly, it has been shown that the malware is still under development; later signs suggest it will soon start attempting to encrypt Time Machine backup files, therefore preventing users from doing a clean install and recovering their lost data.
Transmission has now released a virus-free version of its software, while Apple announced they had revoked a digital certificate from a legitimate Apple developer which allowed the virus to bypass Gatekeeper.
Bricked iPhones
This problem is entirely of Apple's own making, and could have far-reaching consequences. Put simply, manually setting the date of your iPhone or iPad to January 1st, 1970 will brick your device. (WARNING -- do not do this, just trust us!).
Researcher Zach Straley discovered the flaw in February and announced it via a video on his YouTube channel.
The reason it happens is not entirely understood, but it's thought the problem can be traced to the dates on which encryption security certificates are issued.
While it might seem like a hilarious way to prank your friends, the issue is actually much more serious. The reason is two-fold. Firstly, iDevices automatically connect to wireless networks they have seen before -- so if you join "Hotspot" in an airport, your phone will automatically connect to any network called "Hotspot" in the future without asking you. Secondly, iDevices check various "network time protocol" (NTP) servers around the world to sync their internal date and time clocks.
Therefore, if a hacker spoofs one of these NTP servers on their own commonly-named Wi-Fi network, they could easily override your device's clock. Amazingly, security researchers Patrick Kelley and Matt Harrigan found they could brick endless devices with only $120 of equipment.
Apple has patched the flaw in iOS 9.3.1. If you're not running it, you need to update immediately -- if you don't, you are vulnerable.
Apple DRM Flaws
DRM -- or "Digital Rights Management" -- is used to restrict the sharing of proprietary hardware and copyrighted works.
Apple's DRM is called FairPlay and is used by the iPhone, iPod, iPad, Apple TV, iTunes, iTunes Store and the App Store. Unfortunately, it has been exploited by the AceDeceiver malware.
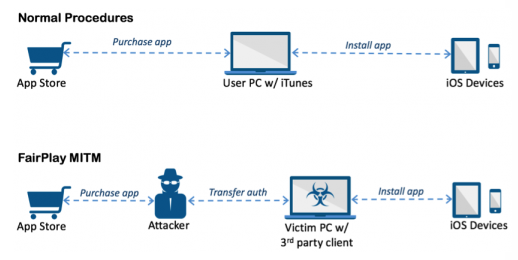
It utilizes a technique called "FairPlay Man-In-The-Middle (MITM)". This is the same technique that has been used in the past to install distrusted pirated iOS apps, but this is the first time it's been used for malware.
The people behind the attack purchase an app for their phone on their computers, then intercept and save the authorization code it generates. Specially-designed software then simulates the iTunes client behavior and tricks iOS devices into thinking the app was purchased by victim -- ultimately allowing the hacker to install malicious apps without the user's knowledge.
Between July 2015 and February 2016, three apps in the App Store were found to be vulnerable -- each bypassed Apple's code review at least seven times. The apps have since been removed, but that doesn't solve the problem; the apps only need to have been available once for the hacker to get a code and spread the malware.
At present, the attack is only affecting victims in China. However, it is thought FairPlay MITM will become an increasingly common attack vector for non-jailbroken iDevices in the months and years ahead.
What Threats Have You Encountered?
If you're an Apple user, it's really important that you understand the threats you face. The days of safety-in-obscurity are long gone, and Apple's hardware and software are demonstrably just as vulnerable as any other company's products.
If you have a Mac, make sure you have a good anti-virus installed. If you own an iPhone, be extremely vigilant about what games and apps you download -- especially if they are not published by mainstream developers. Failure to take precautions is certain to end in disaster at some point.
Have you fallen victim to any Apple-based malware? Perhaps you're caught in the middle of the Adobe-vs-QuickTime situation? Or are you still naïve enough to believe you'll be safe regardless?
As ever, we'd love to hear from you. You can leave us your thoughts and opinions in the comments section below.