You've signed up to a VPN, and you're happy with the privacy it brings to your online activities. Maybe you use for safety on public Wi-Fi, or to beat region-blocking restrictions on your favorite streaming sites.
But what if we told you that the VPN (at least in its current form) is in danger of dying out? You might be doubtful, so here are seven problems with VPNs that need fixing, sooner rather than later.
1. The NSA Can Break VPN Encryption
Let's start with the uncomfortable truth: the NSA has the technology to break your VPN's encryption.
The overwhelming majority of 1024-bit encryption uses the Diffie-Hellman cryptographic key exchange. However, it turns out this method uses a limited number of prime numbers, and this flaw has been exploited to decrypt encryption.
In 2015, researchers Alex Halderman and Nadia Heninger wrote:
"Breaking a single, common 1024-bit prime would allow NSA to passively decrypt connections to two-thirds of VPNs and a quarter of all SSH servers globally. Breaking a second 1024-bit prime would allow passive eavesdropping on connections to nearly 20% of the top million HTTPS websites. In other words, a one-time investment in massive computation would make it possible to eavesdrop on trillions of encrypted connections."
Snowden got there first, however, revealing the NSA's ability to snoop encrypted connections prior to this research being published.
So, your VPN isn't as secure as you thought. That alone is enough to seriously reconsider the subscription.
2. Your ISP Can Block VPN Connections
Trying to make a connection to a server holding media blocked in your jurisdiction via Kodi? Or simply want to keep your viewing private? VPNs can be used to bypass ISP restrictions accessing these servers. But those same restrictions can be expanded to include VPN servers.
Are you affected by this?
It's difficult to say. Several users across the internet have posted about this problem, on Reddit, and on Kodi forums. But you can easily check if you have been affected by this. Simply try streaming a movie or TV show via your VPN. If it doesn't work, and all other unencrypted internet connectivity is fine, then there's a good chance the VPN is being blocked.
And don't forget, if you're in the U.S., ISPs now have the ability to snoop on your activities and sell data about you. If you thought a VPN could help here, it looks like time is running out.
3. Free VPNs Are Ruining Reputations
We've looked elsewhere at a number of free VPNs that are worth trying. However, these are the exception. Long term use of these services is not recommended. A subscription service will deliver far better results.
It's great to get free stuff, but this disregard for privacy -- where your activities online are being passed to advertising networks -- goes against everything VPNs stand for. Worse still, free VPNs drag down the entire VPN industry.
Don't be too sad about this. Many free VPN services are run by the same companies operating "superior" subscription services. Given how they feel about free customers, and the impact this is having on the industry, these companies are essentially overseeing their own downfall.
In short, free VPNs need to fail, or else operate with complete transparency.
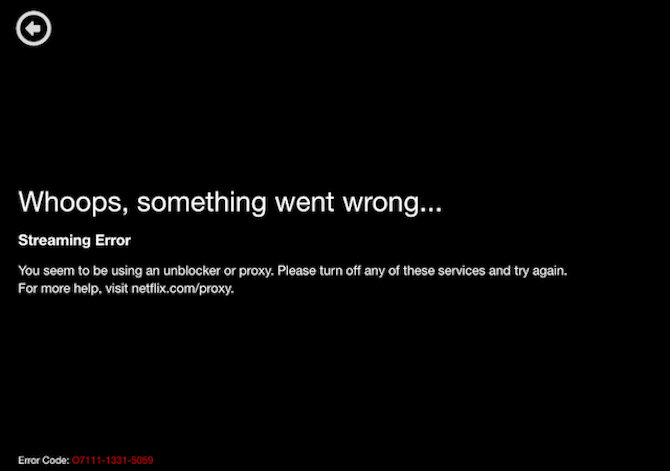
4. Geo-Blocking Targets Known VPN Server Addresses
Geo-blocking used to be easily circumvented by VPNs. These days, not so much.
Say you want to watch Netflix, but your account is U.S.-based. You're on holiday in the U.K., and region blocking means you can't access the same list of movies and TV shows as you would at home. Employing a VPN can circumvent this block, fooling the Netflix servers into thinking you're in your home country. All you need to do is use a U.S.-based VPN, and the show is yours to watch. Some VPN services are sold on their ability to bypass region blocking.
Now, however, Netflix (and other streaming providers) are wise to this. It's becoming increasingly difficult to make a connection. Take, for example, the BBC. If you're trying to view content on the UK version of BBC iPlayer from an overseas location, you'll be blocked with a polite message. But even using a U.K.-based VPN server will illicit the same response.
This is because streaming services are increasingly using a blacklist of VPN servers. Such lists are collated by checking VPN providers and logging the server IP addresses. With these IP addresses blocked, no one can access the Netflix, BBC iPlayer, etc. unless they're doing so without a VPN, and from the correct geographic location.
Another win for the streaming services, and yet another strike against VPNs.
5. Logless VPNs Are a Myth
VPNs jostle for attention by promising whatever they can -- or whatever they can get away with. One of those promises ("no logging") always catches the eye. After all, why pay for anonymity if the logs can give you away?
The truth is, however, that logless VPNs are never 100 percent free of logs. VPN companies use third-party servers. Those servers are leased, and they have logs recording all sorts of data. While the VPN you subscribe to may not be maintaining logs, you can be certain that whoever owns the server certainly is.
What this means is that somewhere there is a log of your activity. It may be innocuous, and you may have done little of interest. But given everything else you've learned so far, this is yet another reason to seriously reconsider your continued use of virtual private networks. As we've explained previously, server logs are vital for server management:
"Without logs, a VPN provider would be unable to handle DNS requests, prevent abuse, troubleshoot connections, or limit VPN accounts based on the subscription type you've chosen, such as putting a cap on the amount of data you can use."
And then there's this:
It's worth looking at the VPN service's website to find out what information they admit to collecting. Just remember your online activity isn't as private or anonymous as you've been lead to believe.
6. Data Mining Your Personal Information
Reputable sites probably won't do this, and you'd probably never know, but in the age of low-cost VPNs, these services have to make money elsewhere to maximize their revenue. One way is to sell your personal data onto advertisers and direct marketing companies... spammers, basically.
We've already seen that this is a problem with free VPNs, so it's not behavior that you would expect from a paid solution. However, it is certainly not unheard of. Not only is it a breach of trust, this practice also takes a massive liberty with your data.
By sharing information about you, that subscription VPN makes extra money. You get extra spam, and adverts targeted to you at some of the sites you visit. That isn't what you signed up for: you subscribe to your VPN for enhanced privacy, not the opportunity to "enjoy" personalized adverts and part with more cash, right?
7. Are VPNs Completely Anonymous?
Short answer: No.
As explained earlier, we've known for several years that the U.S. government's NSA has the ability to break the most common forms of encryption. In short, your VPN isn't as anonymous as you think it is.
But this goes beyond what the NSA can do.
One of the biggest problems for VPN privacy are IP leaks and DNS leaks. Then there's the trust issue, which we've touched on already: is your VPN really keeping your data private? But there's possibly a worse problem, one which is regularly overlooked. Your VPN connection is only secure and private between your computer, and the VPN server. Beyond that, you're identifiable, not just by the account you login with. Data transmitted between the destination site, and your VPN server, if not already encrypted, can be read.
And we've already seen how security agencies deal with encryption.
Perhaps more concerning is the fact that VPN providers can see your destination. It might not be obvious who is going where, but the sites your read and only services you access are recorded, logless or not.
What Can VPN Companies Do About This?
The future for VPN services is grim. We're really only touching on the faults above, but the real problem isn't just dealing with these (potentially insurmountable) problems. As challenges go, this is big: VPN companies need to embrace new technologies.
Several are already available, such as protocol obfuscation, which is theoretically more secure than the SSL/TLS/HTTPS system already in use. There's also the possibility of building a VPN into your computer's operating system, and developing authentication for connections. The universal push towards HTTPS should also help.
Perhaps the biggest privacy step for VPN providers, however, is to develop a new approach to TOR. (What is TOR?)
Currently, the most secure and private way to connect to the internet is to use a VPN and TOR together. Although slow, it's expected that fast internet speeds will overcome this limit in the foreseeable future. TOR is becoming increasingly popular, so it makes sense to wrap both privacy methods into one. This approach can protect you from VPN hacking, which is not common, but still a possibility.
Failure to adopt most (or all) of these things will see VPNs all but extinct in just a few years. And who knows what will happen to privacy after that?