Let's face it, these days the likelihood that you are being monitored by someone is rising all the time. I'm not saying that everyone, everywhere faces the threat of cellphone surveillance, but there are plenty of situations where you could be at risk without realizing it.
Maybe you're an activist on the streets of New York City, with the police and FBI parked outside of your apartment building. Maybe you're a freedom fighter in the Middle East, trying to get the news out about conditions in your country. Or maybe you're a journalist working somewhere in the world where there's government corruption and you're trying to expose it.
It doesn't take much to become targeted by both amateurs and professionals alike, for eavesdropping and surveillance. A New York Times article from March revealed that police agencies in the U.S. are increasingly using cellphones to perform surveillance on suspected individuals. This isn't to say they are only using the technique on confirmed criminals - all you have to be is "suspect" to face the threat of "big brother" analyzing your every move.
Even in the face of overwhelming surveillance and even professional attempts to gather information about you through your phone, there are a few steps that you can take to protect your personal information. At the very least, the tools and tips that I'm going to introduce you to in this article will make it significantly more difficult for anyone to find out what you're doing with your phone.
Protecting Your Cellphone From Surveillance Attempts
Tracking someone with a cellphone is a popular request - jilted former boyfriends or girlfriends want to know how to track someone, suspicious wives or husbands are always asking how to do it, and the list goes on. One of my most popular articles that I've ever written just happens to be about how to trace a cellphone with Google Latitude. To this day, I still get requests from people asking me to help them track someone's cellphone.
Steve also covered the topic, explaining how to find your friends via GPS. The danger of being tracked is so real that Christian felt compelled to write an article helping people turn off "localization" on their phones. But is turning off those services enough to protect yourself?
Encrypting Your Notes
The truth is that turning off those apps and services that track your location is only the first step. I highly suggest you take Christians advice and do that as a first step. It's all too easy to track someone that has turned on their GPS and enabled some app that reports out to Latitude, Facebook or Twitter.
However, the next step is making sure that the undercover guys sitting in the van out in the street can't intercept your email, your text messages, and your phone calls. You also need to protect the data that you store on your phone. In this article, I'm going to help you encrypt and protect all of that information.
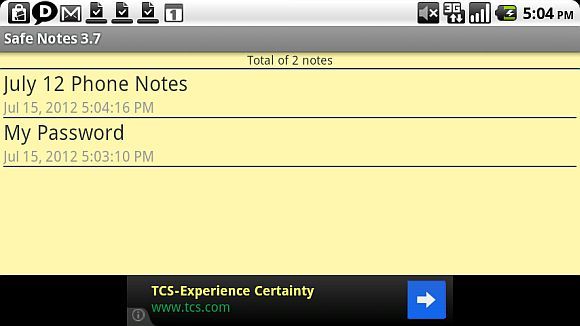
If you need to keep track of private information, like passwords or account numbers, on your mobile phone, install Safe Notes. Safe notes will store those critical notes behind a PIN number of your choosing.
Of course, just having a PIN number to access stored notes will not protect the data from someone that can gain access to your data directory on your phone, and attempts to extract the text from your note through some back-door technique. For that contingency, Safe Notes stores all of your entered notes on your phone using 128-bit encryption.
That means that any information you store within Safe Notes will truly be protected from prying eyes. Only the most sophisticated, tech-savvy hacker would even stand a chance of cracking that, and such a hacker is not going to be on the payroll of the police department. You might have to worry if the FBI is involved - but even then, you'd have to be worth the effort for the Feds to try to break the 128-bit encryption.
Encrypting Text and Email
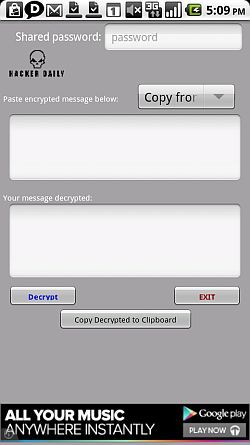
Another big concern isn't just the information you have stored on your smartphone, but the information you have streaming in and out of it in the form of text messages and email. One simple app that can help you protect those transmissions is Encrypted Messages [No Longer Available] by Hacker Daily.
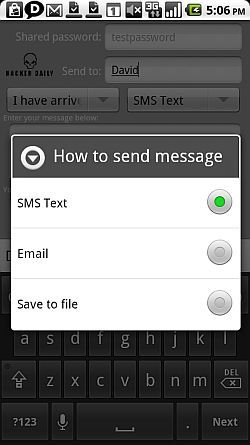
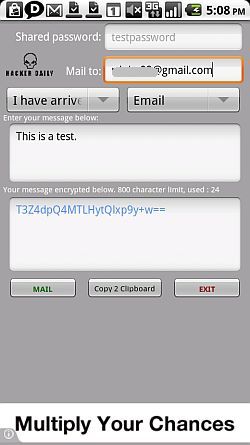
This app lets you create a text message that you want to transmit, give it a password, and then receive the message in encrypted form in the message box at the bottom of the app. The only way anyone will be able to decipher that strange mix of text and characters is if they have the Encrypted Messages app, and if they know the correct password.
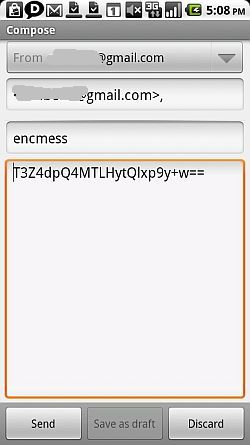
If you click on the "Mail" button, the app will actually compose the email for you using your default email app, and it'll paste your encrypted message into the body. All you have to do is hit Send.
The person receiving the encrypted message can simply paste the message into the app, type the correct shared password, and read the decrypted text in the bottom window.
It really doesn't get much simpler than that. The good thing about this kind of setup is that if the password ever gets compromised, you can both simply agree on a new password and start sending encrypted messages safely again.
Encrypting Voice
Encrypting text is all well and good, but what about all of the phone calls that you make? What is stopping someone from intercepting those transmissions in mid-air and listening in on your conversation? Realistically, not a whole lot.
As the world becomes more and more mobile, people become more and more susceptible to conversations getting intercepted. You may not think voice conversations hold a lot of private information, but think about everyone you talk with on your phone - your doctor, your lawyer, or your business associates.
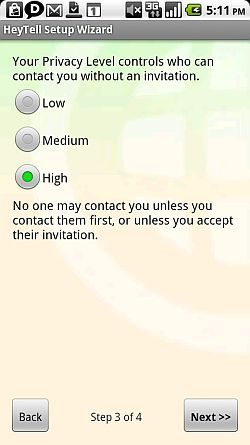
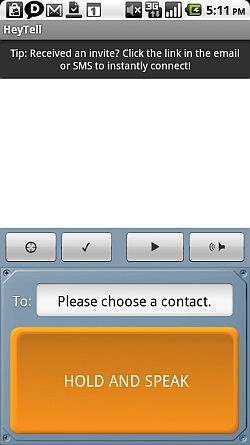
Voice is trickier to encrypt, but not many people realize that the HeyTell VoIP app actually encrypts all data and audio in transit.
Just set your privacy high so that only you can decide who you communicate with, and then start using the app. It's a very cool app that can replace phone calls to any friends or associates that are also running the application on their smartphone.
It basically turns your phone into a press-to-talk capable phone - converting your cellphone into a digital walkie-talkie with encrypted transmissions!
So, you've got your notes, your text messages, your emails, and your voice transmissions all encrypted and protected from government surveillance, so is there anything left?
Lock Up Passwords and Accounts
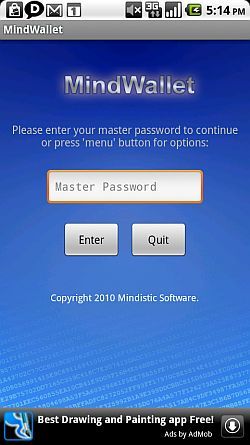
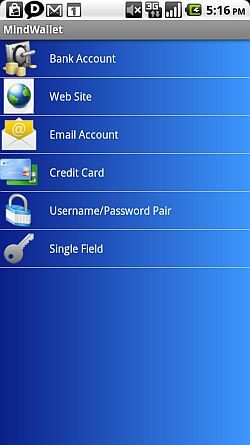
I know I mentioned that SafeNotes could be used to encrypt text like passwords, but if you really want double-security for your critical, private information, then you'll want to install MindWallet [Broken URL Removed].
MindWallet is a popular data-protection app that stores your account and password information behind military-grade encryption - a 128 bit AES algorithm.
Your Master Password doesn't get stored anywhere in plain text, not even on your phone, so it's a password that you don't want to forget. It is your key to everything. Once you log in with that Master Password, you can store everything - bank account details, critical websites, your email account details, credit card accounts, and any other username/passwords you need to remember.
The cool thing is that you aren't limited to the templates that come with MindWallet. If there's information that's very specific that you want to lock away, just create your own database entry fields and add them to your own custom "item" that you want to store inside your secure "wallet".
When it comes to surveillance, the main reason police and even journalists have been able to hack so easily into the personal details of cellphone users is because no one bothers to protect themselves. Voice and data gets transmitted without even a bit of security in most cases. By adding the sort of high-level encryption found in the apps above, you will make yourself a much smaller target that is nearly impenetrable to most surveillance attempts.
Encryption is the key. Give the apps above a try and let us know how well they worked out for you. Were they convenient enough, or did they hamper your use of communication apps? Share your thoughts and insights in the comments section below.
Image Credits: Police via Shutterstock