If you're concerned about online and electronic privacy, encryption is the best thing to set your mind at ease. By using strong encryption protocols, you can make sure that your data is safe from prying eyes, and that only the people who you decide should see your information have access to it.
One of the most common methods for encryption is called PGP. This article will guide you through what PGP is, what it's good for, and how to use it.
What Is PGP?
PGP stands for "Pretty Good Privacy." PGP is most often used for sending encrypted messages between two people. It works by encrypting a message using a public key that's tied to a specific user; when that user receives the message, they use a private key that's known only to them to decrypt it.
Unsure what a public key or a private key is? Check out these basic encryption terms before reading on. It'll help make encryption terminology much easier to understand.
This system ensures that it's easy to send encrypted communications because the only thing needed to encrypt a message is a public key and the proper PGP program. But it's also quite safe, as messages can only be decrypted with privately known keys that are password-protected.
In addition to encryption, PGP also allows for digital signatures. By signing your encrypted message with your private key, you provide a way for the recipient to see if the message content has been changed. If even a single letter in the message is changed before it's decrypted, the signature will be invalidated, alerting the recipient to foul play.
What's the Difference Between PGP, OpenPGP, and GnuPG?
Throughout this article, I'll be discussing both PGP and Gnu Privacy Guard (GnuPG, or GPG).
GPG is an open-source implementation of PGP, and works on the same principles. Unless you're going to be buying a PGP-enabled product from Symantec, the company that currently owns the PGP copyright and company, you'll likely be using GPG.
Here's a quick history of PGP, OpenPGP, and GPG.
PGP: Developed by Phil Zimmerman in 1991, PGP is one of the most enduring digital encryption methods and the most popular email encryption tool. Now owned by Symantec but licensed by thousands of companies.
OpenPGP: Up until 1992, cryptography featured on the US Munitions List as an Auxiliary Military Equipment. Which meant exporting Zimmerman's PGP tool to international countries was a serious crime. In fact, Zimmerman was investigated for breaching the Arms Export Control Act, such was the power of the PGP encryption tool at the time.
Due to those restrictions, the OpenPGP Working Group was formed with help from the Internet Engineering Task Force (IEFT). The creation of an open-source PGP version eliminated the issues regarding the export of cryptography while ensuring anyone could make use of the encryption tool.
GnuPG: GnuPG (GPG) is an implementation of the OpenPGP standard and is considered a strong alternative to Symantec's PGP.
Importantly, encryption algorithms are interchangeable between these options. They are designed to work together to allow users the option to use one or the other without losing access to important data.
PGP Keys Explained Quickly
The mathematical mechanics of PGP are extremely complicated. However, the video below will give you a general idea of how the system works.
PGP encryption uses a combination of symmetric key encryption (a single-use key) and public key encryption (keys unique to the recipient).
How Secure Is PGP?
It's impossible to say that any particular encryption method is 100 percent secure. That said, PGP is generally regarded as being extremely safe. The two-key system, digital signatures, and the fact that PGP is open-source and has been heavily vetted by the public all contribute to its reputation as one of the best encryption protocols.
World-renowned security expert Bruce Schneier once called PGP, "the closest you're likely to get to military-grade encryption," and PGP.net says that there are "no practical weaknesses."
So, is PGP secure? Well, Edward Snowden used PGP to send files to Glenn Greenwald when he broke the story that kicked off a lot of interest in encryption. And if it's good enough for Snowden, it's good enough for most---if not all---of the other people who need to encrypt things.
PGP Encryption Algorithms
Different types of encryption algorithms can be used with PGP, though the RSA algorithm is quite common. If you've never heard of RSA encryption, rest assured that it's really, really strong. RSA features on our list of common encryption algorithms, which provides more detail.
According to DigiCert, it would take a standard desktop computer many quadrillions of years to crack a 2048-bit RSA SSL certificate.
That means that if you'd started trying to crack that certificate at the time of the Big Bang, you wouldn't finish before the end of the universe. 2048-bit RSA is commonly used as a standard algorithm for PGP.
Gnu Privacy Guard uses the AES algorithm by default. AES is one of the strongest publicly available encryption algorithms. For reference, if the US government specifies something as top secret, it carries AES-256 encryption. And if it is good enough for the national security agencies and government, it is good enough for you.
While crypt-analysts and crypto-enthusiasts could argue all day over the best algorithm to use, GnuPG says that "GnuPG's algorithms are so well-designed for what they do that there is no single 'best.' There's just a lot of personal, subjective choice."
Getting Started with PGP and GPG for Email in 4 Steps
You know a bit more about how PGP works. Now you can put it into practice.
1. Download GPG Tools for Your System
As mentioned, PGP is a licensed encryption tool that Symantec owns. You can use the GnuPG as a free and open-source alternative.
GPG is a command line-only application. If that isn't your cup of tea, you can use a GPG tool with a visual interface instead.
- Windows: Head over to Gpg4win and download the tools.
- macOS: Download the tools from GPG Tools.
- Linux: You can download GPA. Some Linux distros, such as Ubuntu, have a GPG version installed already, such as SeaHorse or Passwords and Keys.
You'll also need to make sure that you have the proper tools for your email client.
For example, Apple Mail has built-in support for PGP. The Gpg4win installer contains an option for encryption within Outlook. Enigmail allows you to encrypt email in Thunderbird, while tools like Mailvelope and Flowcrypt let you use your PGP keys for webmail.
2. Generate Your Public and Private Keys
Depending on the software you use, you'll use different methods to generate new keys.
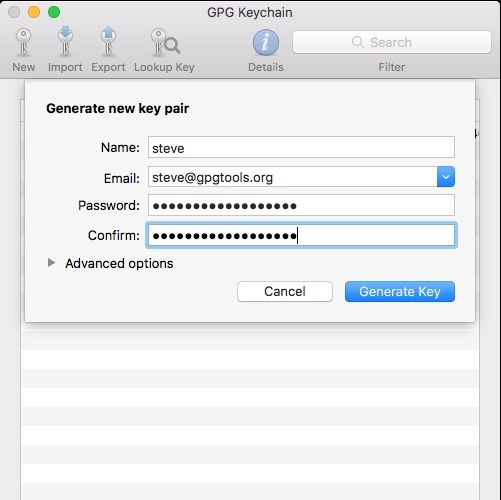
In GPG Suite on macOS, you just have to click on New. You enter some details, like your name and the key type. You'll also have to decide whether or not to upload your public key to a key server.
In general, this is a good idea, as it will allow others to find your public key and send you encrypted messages, even if you haven't communicated previously. However, if you're just getting started with PGP, you may want to hold off on uploading, as you can't change your name or email address once you upload it.
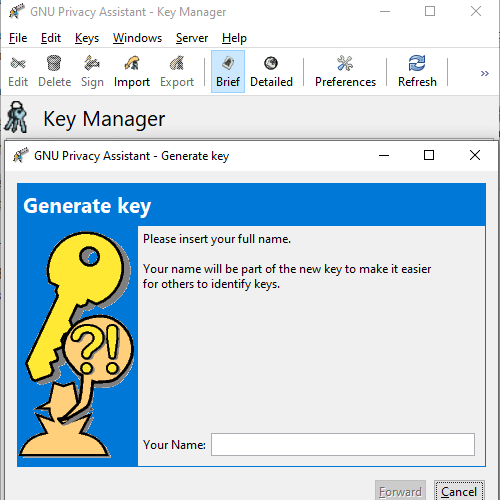
The key generation process is similar in other tools, too. The example below is from the Gpg4win Privacy Assistant Key Manager. It guides you through the key creation process.
3. Enable PGP In Your Email Client
Again, the process to enable PGP encryption in your email client will vary. The best way to find out what you need to do exactly is to search through the email client help files. Alternatively, complete an internet search for "[email client name] enable PGP."
For example, the macOS GPG Suite installs the PGP add-on for Apple Mail and adds the necessary information and icons automatically. Whereas, you'll have to import your encryption keys into Microsoft Outlook manually.
If you want to find out more about importing and creating keys, you can sign-up for our free email security course, which covers this and much more in greater detail.
4. Get Public Keys for Your Contacts
You're now ready to send PGP-signed emails! However, there is one more important step. For someone to decrypt an email that you send them, you need their public key. The easiest way is to swap keys personally, be that via email, instant message, or otherwise.
You can post your public key to your website or Twitter bio if you want, as there is no risk posting your public key. Just ensure that it is your public key and not your private key---that's the bit that must remain secure at all times.
There are several public keyservers you can search for public keys belonging to your friends, family, colleagues, or otherwise.
On macOS, GPG Keychain Access, part of GPG Tools, allows you to search for keys from directly within the app. There are also keyserver search tools online, too, such as the PGP Global Directory or the MIT PGP Public Key Server. Once you find a key for your contact, you should download it and import it into your app using the specific procedures required.
PGP File Encryption
Although plenty of open-source, free email encryption tools use PGP, the number of file-encryption options is much smaller.
Still, some implementations do allow users to encrypt files using PGP. For example, Windows users can use Gpg4win's Kleopatra to encrypt a file or folder using the same encryption keys as your email account. Windows users can also check out Cryptophane, an open-source tool for signing and encrypting with PGP.
Mac and Linux users will likely want to use Seahorse. Alternatively, you can use GPG via the command line. Here's how you encrypt files using GPG using the Linux command line.
However, if you want individual file or folder encryption on your local system, Windows users should check out how to encrypt using VeraCrypt.
PGP Makes Encryption Easy for Everyone
You don't have to understand the complicated cryptomaths behind PGP to know that it's a great encryption system. And you don't have to be a computer genius to take advantage of it to encrypt your emails and files, significantly increasing your online and electronic safety. By downloading just a few tools, you can start encrypting sensitive information today.
Don't forget to check out our article on the most secure email providers, many of which come with integrated encryption tools. They make encryption even easier!