You recently received an unexpected iOS update. Go on, have a look. By now, you should have updated your iPhone to iOS 9.3.5 to patch three zero-day vulnerabilities being actively exploited to allow attackers chance to intercept and steal confidential information from a massive range of apps.
The spyware, dubbed Pegasus, was discovered by mobile security research company Lookout with assistance from the University of Toronto's Citizen Lab. They believe the spyware has been circulating for some time, though has primarily been used to infect high-value targets in possession of sensitive information.
Pegasus Soaring Free
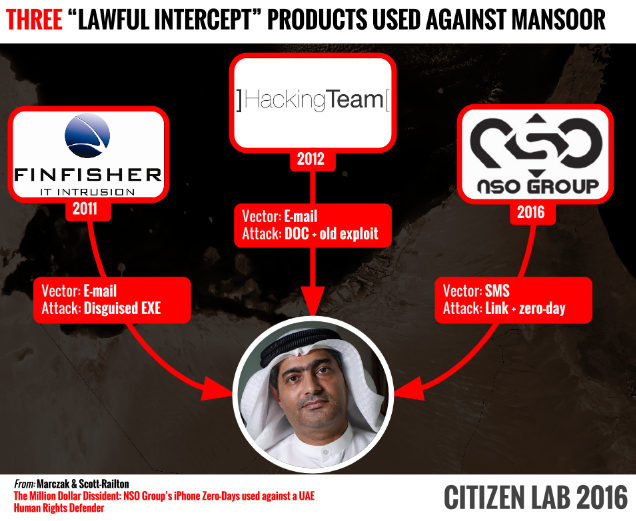
Pegasus was discovered when prominent human rights defender, Ahmed Mansoor, received a suspicious SMS promising "new secrets" about detainees being tortured in United Arab Emirates jails if he clicked on the link provided. Instead, Mansoor forwarded the message to Citizen Lab for analysis.
They discovered a particularly advanced piece of spyware specifically equipped to remain as obfuscated as possible, complete with self-destruct instructions. Citizen Lab and Lookout released a statement describing the potential hack as bearing the hallmarks of the shadowy-but-prominent NSO Group, purported to have been founded by veterans of the Israeli Intelligence Corps 8200 Unit.
We recognised the links as belonging to an exploit infrastructure connected to NSO Group, an Israel-based 'cyber war' company that sells Pegasus, a government-exclusive 'lawful intercept' spyware product.
Once infected, Mansoor's phone would have become a digital spy in his pocket, capable of employing his iPhone's camera and microphone to snoop on activity in the vicinity of the device, recording his WhatsApp and Viber calls, logging messages sent in mobile chat apps, and tracking his movements.
This is believed to be first "instance of an iPhone remote jailbreak used in the wild as part of a targeted attack campaign," making its discovery both rare and important. The collection of the three zero-day vulnerabilities has been collectively termed Trident and consists of:
- CVE-2016-4657 -- Visiting a maliciously crafted website may lead to arbitrary code execution.
- CVE-2016-4655 -- An application may be able to disclose kernel memory.
- CVE-2016-4656 -- An application may be able to execute arbitrary code with kernel privileges.
Pegasus' Mythical Powers
We are only aware of the existence of the so-called Pegasus spyware because Mansoor forwarded his infected SMS to the security researchers in Toronto. They managed to unpack and isolate the spyware before the link sent to Mansoor became inactive. So what does it do?
Generally speaking, most of what you'd expect a piece of modern, advanced spyware to do. It specifically targets mobile phones, stealing browser history, email, SMS, and messaging data (including data for apps such as iMessage and WhatsApp), as well as contact lists, calendar records, location histories, and much more.
The iPhone has a well-deserved reputation for security. As the iPhone platform is tightly controlled by Apple, technically sophisticated exploits are often required to enable the remote installation and operation of iPhone monitoring tools. These exploits are rare and expensive.
The security researchers were impressed with the Pegasus spyware ability to remain obfuscated for extended periods of time, with Lookout's Vice President of Security Research, Mike Murray, stating to Motherboard:
The NSO Group software and the way it's configured and run, it's all about not being detected, [it's] designed for stealth and to be invisible.
Underlining its use against high-value targets, the spyware is designed to record its surrounding and take pictures, but only when the screen is turned off. Pegasus also has certain self-destruct mechanisms that can be triggered under certain circumstances.
Pegasus takes advantage of how integrated mobile devices are in our lives and the combination of features only available on mobile -- always connected (WiFi, 3G/4G), voice communications, camera, email, messaging, GPS, passwords, and contact lists. As a result of its functional modularity, the breadth of communications and user data it monitors, and the tailored methods it instruments into other applications to exfiltrate data from them, to date, Pegasus is the most sophisticated privately-developed attack Lookout has encountered on a mobile endpoint.
"Lawful Intercept"
NSO Group, the developers of Pegasus, have licensed the spyware to Panama and Mexico, according to data gathered by activist group Privacy International. The Panamanian government reportedly paid $8 million for Pegasus, as reported locally. We can also definitively add the United Arab Emirates to that list, as they've been directly implicated in this exposé.
"Lawful intercept" technology is nothing new and many countries have rigorous legislation in place to ensure these technologies are not abused. Unfortunately, we know that this isn't always the case. Even the single case of Ahmed Mansoor highlights the issues surrounding such powerful spyware, this being the third "lawful intercept" tool used to gather information that would presumably be used against him.
What Does It Mean for Me?
If you've updated your iPhone already, you'll be fine. The most interaction the majority of the iPhone-owning population will have with Pegasus is spotting the critical update issued by Apple and installing it. As the Errata Security blog says:
I suppose it is new to those outside the cybersec community, but for those of us insiders, it's not particularly newsworthy. It's just more government malware going after activists. It's just one more set of [zero-days].
In this case, there is a slight difference. Whereas the majority of zero-day vulnerabilities are usually discovered by security researchers or by the company themselves, this is one that is being actively exploited to steal private and likely highly sensitive information that could place people in very immediate danger.
As well as this, the context of Pegasus development makes its discovery and usage a bit more interesting than usual: a potentially dangerous spyware tool developed in a democratic country, Israel, being sold to those with repressive regimes, such as the UAE. While the tool is developed legitimately as a "lawful intercept" tool, this case exemplifies how the spyware is used in the wild. The NSO Group operate within the law and, in their own words, only want "to help make the world a safer place, by providing authorized governments with technology that helps them combat terror and crime."
Be that as it may, it is still being used against a dissident, defending human rights in a country known to take a rather dim view of such actions, rather refuting their official stance that their "product may only be used for the prevention and investigation of crime." Of course, Mansoor's actions within the UAE do largely add up to criminal activity (within their jurisdiction).
Bugs Found in OS X and Safari
Apple has quietly pushed out critical patches for its desktop platform, OS X, and its main browser, Safari, after it emerged that the Trident zero-day vulnerability would also affect those services. It is somewhat unsurprising given the amount of code shared between those platforms, so when a vulnerability is found in one, it is highly likely to affect the other.
You can find patches for El Capitan and Yosemite here and a patch for Safari can be found here. These patches can be downloaded and installed via the standard update mechanisms, and we would highly recommend you do that.
Secure... Until Next Time
Your Apple device is secure if you have updated. If you're still unsure, download the Lookout Security App and scan your system. If it finds something, you'll need to install a patch. Those users who do not wish to patch (for instance, if you're already jailbroken) may consider this tutorial. (Disclaimer: I haven't done this and this is not linked to or approved or endorsed by MakeUseOf in any way.)
Zero-day vulnerabilities are discovered all the time and patched without a nod to the security researchers or people they might affect. However, iPhone users should really take heart -- Android users are open to any old hacker with an inkling of self-belief and the wherewithal to watch some YouTube videos.
iPhones are still only being exploited by nation-state actors. It remains the most secure phone available to the majority of consumers, despite the numerous zero-day vulnerabilities appearing in the news. Zero-day exploits will always be probed and exposed. Apple offers a maximum of $200,000 in their bug bounty program, and last year software broker Zerodium offered $1 million for exploits granting attackers access to an iPhone. You see the problem.
You and your data will be fine. But this will not be the last instance of spyware targeting activists or journalists.
Have you updated your iPhone? Do you think nation-state actors should be more responsible with their "weaponized" malware and spyware sales? Let us know your thoughts below!
Image Credit: Lawful Intercepts Used Against Mansoor via Citizen Lab