Last time, I showed you how to attempt to break free of the tight embrace that is Google. This time, I am going to cover a wide range of topics, and offer tips that I have picked up on my online travels and from speaking to knowledgeable colleagues and friends. Hopefully you will find something here that connects with you and use to make your time online more secure.
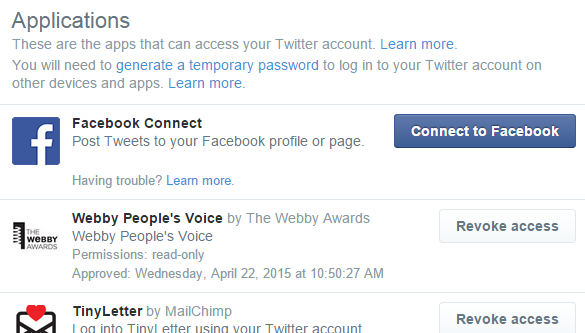
Revoke Website Privileges On Google, Twitter & Facebook
When you sign up for a website, the signup buttons for Facebook Connect and Google are always there, lurking in the lazy side of you ("do you really want to fill out this very long sign-up form? If you use the Facebook / Google button, it's only a couple of clicks!"). But by using Facebook Connect or Google, we are telling Facebook and Google a lot about ourselves - in particular our browsing history. Twitter too. Browsing habits are what marketing profiles are made of.
So start revoking those privileges. Here's the Google page, the Facebook page, and the Twitter page to do just that. Then start signing up to websites using disposable email addresses which redirect to your real address. The gold standard here is Blur. There is a free plan and a paid one, but the free one is more than sufficient for most people.
Use a Virtual Private Network (VPN)
This is something that we have covered extensively in the past, including a roundup of all the best VPN services. I personally love Tunnelbear, but many others are available for you to take a look at. Everyone who surfs the Internet should be using a VPN - in fact, GHacks asked if VPN's were the next big browser feature.
A VPN essentially switches your IP address and re-routes all of your website traffic through that VPN's servers. So it looks as if you are surfing from the country you have chosen in the VPN software. This is good for hiding your true location, and stopping anyone from looking at your login information in a public Internet café - but you shouldn't really be using public Internet cafes anyway. You never know what is installed on those computers to capture your passwords; for all you know, there could be keyloggers in there recording every keystroke.
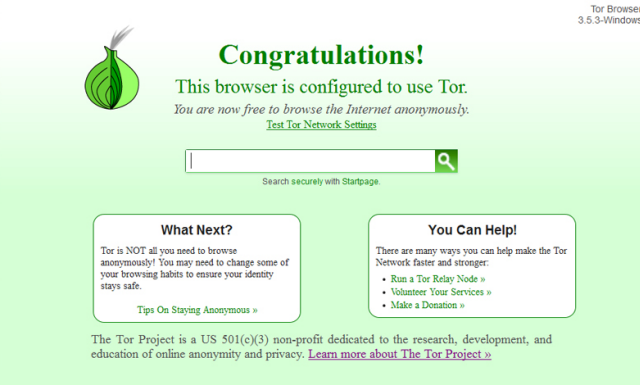
Use the Tor Browser
It's been claimed that using Tor will immediately gain you the attention of the NSA, or its British counterpart, GCHQ. But my feeling is that they are watching us anyway, so what's the difference? There were also concerns not that long ago that the Tor browser was compromised, but still, a little bit of protection is better than none. Just make sure you are downloading the right version. ALWAYS download from the official site. Not sure what TOR is? Our TOR guide explains this and more.
Always Use Security & Privacy Browser Plugins
HTTPS indicates that the site has a encrypted security certificate, which stops people from hacking into the site. As a normal web surfer, you should be trying to visit as many sites as possible which have "https" in their web address.
One way to ensure this is all done without any effort on your part is to install "HTTPS Everywhere", a browser add-on made by the Electronic Frontier Foundation. This will redirect you to the https version of a website, and you can whitelist sites which should be ignored by the add-on (some sites won't work on https).
If you use Chrome, then some other good plugins include Google Analytics Opt-Out, Password Alert, and Chrome UTM stripper. The last one removes all of the crap from a URL, which is used for tracking purposes. Next time you click on a link on social media or from an email newsletter, look at the URL - there is likely to be a "UTM" tracking code on there.
Abandon WhatsApp & Use Telegram Instead
My wife and I use WhatsApp exclusively to communicate via mobile phone, and we are not alone. As of last month, the company reported an increase of monthly active users from 700 million in January 2015 to 800 million in April 2015. I love using the app, but one thing really bugs me though - WhatsApp has more holes than a golf course, with no SSL encryption. Plus it is owned by Facebook, which makes me wary about its long-term privacy prospects. Facebook changes their privacy settings like I have hot dinners.
Instead, I have been hearing great things about Telegram, which offers free apps for iOS, Android, and Windows Phone, as well as versions for the PC, Mac OS X, Linux, and can also be accessed via your browser. As far as I can see, it is a clone of WhatsApp but with loads of privacy settings added in. This includes encrypting your messages, destroying them with a timer, and the servers are spread worldwide, so the service can't be completely shut down from one location (here's looking at you FBI!). Similar apps include Signal and Wickr.
Make Your Searches In Incognito Mode
If you do need to use Google for any reason (perhaps your work uses Google Apps), then you will find that in order to stay logged into your Google email, you need to stay logged in across the entire Google network. Log out of one Google service, such as YouTube, and it logs you out of everything. It doesn't take long for this to get really irritating. And if you stay logged in over the entire Google network, then everything gets logged - searches, YouTube videos watched, news stories read, locations visited, when you picked your nose, the whole lot.
So to keep yourself logged into email, and keep your searches private at the same time, use Incognito for all searches (or Private Browsing, if you use Firefox). Also use a VPN app to switch your IP address to some far-off distant exotic land. Australia sounds nice. You just have to change your name to Bruce.
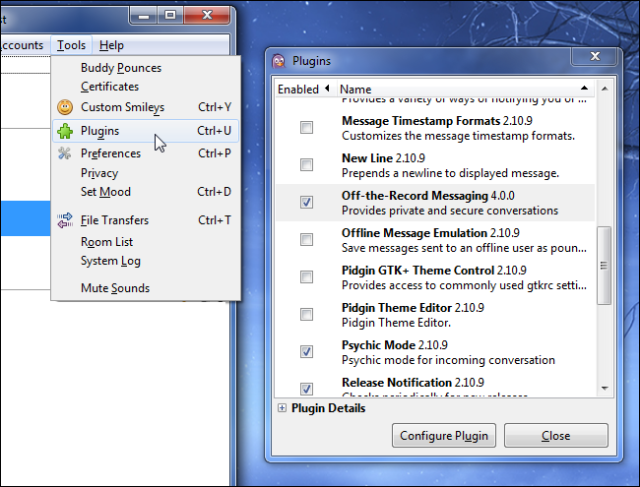
Encrypt Your Instant Messaging With "On The Record" (OTR)
Instant Messaging (IM) is something I am not too fond of, as it can distract me when I am "in the zone", while writing. But I still need it to communicate with clients and colleagues, so recently I have been trying out "Off The Record" (OTR). This is a plugin for Pidgin and Adium, which encrypts your chat messages, and stops "man in the middle" attacks, where the messages are intercepted while on the way to the other side.
When starting a conversation, you can make OTR optional, or alternatively you can insist on it being switched on. Keep in mind that many people get nervous with things like encryption, and so refusal may be likely. So you need to figure out how important it is to have that chat with the person.
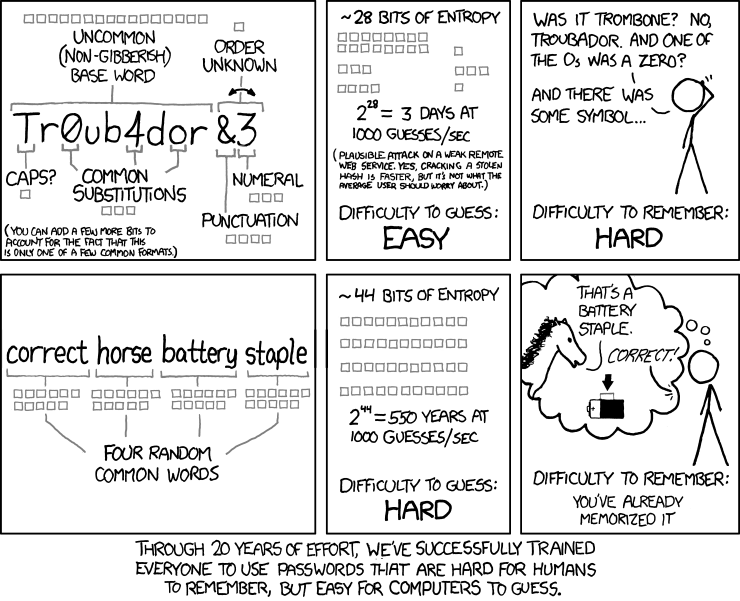
Use Passphrases, Not Passwords
We've all been conditioned to use passwords to protect our accounts, but it seems that passphrases are much better. Edward Snowden explains the concept in an interview with John Oliver.
You might think that @_Fn56@3Cxp0#_Z@ is a pretty secure password, but this XKCD cartoon shows us why a passphrase is much better.
Passphrase generators abound online. Four words is more than enough, but of course you can have more if you have thought of a killer phrase. You can also use dice to work out your passphrases but that seems a bit too over-the-top (even I have my limits).
Put a Sticker Over Your Laptop Webcam (Or Close The Protective Cover On Your PC Webcam)
Webcams are great for talking to grandma, and showing her the new puppy. But webcams also have their dark side too, because you can spied upon without your knowledge - even if the webcam light is off. Think I'm nuts? Read this about a webcam hacker then tell me I'm nuts. And this one.
So unless you fancy being spied upon 24/7, you need to keep the webcam covered up when you're not using it. Many PC webcams have built-in covers to go across the lens. USE IT! If it doesn't have one, throw it away and buy one that does. I use Logitech which has never let me down. If you use a laptop, get some stickers, cut them into squares big enough to cover your webcam, then use them to cover the cam when you are not using it. Or if all else fails, use a band-aid.
Remove All Photos Of Yourself Online - Then Stick To Comic Avatars & Drawings
Facial recognition is on the rise and it's only going to get worse. The FBI expects to have over 50 million facial images in its database this year, and no doubt law enforcement and intelligence agencies in other countries have the same. Indeed, in London, you can't walk down any street without being filmed by several cameras. Also, unsurprisingly, Facebook has its own version for "automating photo tagging" (how thoughtful of them), and Microsoft thinks they can guess your age by scanning your photo (data brokers will love THAT one).
And if that wasn't spooky enough, a smartphone app called NameTag will enable someone to take your picture, and then use that picture to instantly find your social media accounts. It's apparently if you want to date the person, but wouldn't dangerous stalkers use it too?
All of these chilling developments has led to the rise of an anti-facial recognition movement. Fighting developments such as facial recognition is important because what if a machine decides that you are the spitting image of a wanted terrorist? Try explaining that you're not Al-Qaeda's newly promoted number 2 while you sit in a jail cell for an indefinite period.
To avoid being indexed in online facial recognition databases, do three things - go to your Facebook security and disallow automatic tagging of your face. Secondly, search online and remove every known photo of you. Lastly, replace those photos with an avatar of yourself or a pencil drawing. I like Face Your Manga, which is the service I used to create my avatar. As for on the street? Wear a hoodie and a good pair of shades. And look down as you walk.
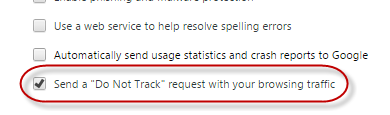
Turn On "Do Not Track" In Your Browser
In all of the major browsers, there is an option to switch on "Do Not Track" with your browsing traffic. But in all truthfulness, this is totally dependent on sites honoring your request. It has frequently been compared to the Do Not Call Registry, which is supposed to stop telemarketers from calling you. Your desire not to be called is clearly there, but the telemarketer can still call if they want to. Do Not Track is pretty much the same. Nice in principle, but in reality, it's perhaps a little idealistic. But on the other hand, how will it hurt having it enabled?
This site has a nice description of what "Do Not Track" is, as well as telling you how to switch it on for your browser, and a list of the sites that actually do honor the request. Sadly, it is an extremely small list.
Encrypt Your Email With PGP & GNU Privacy Guard
I've left the hardest one till last, because after a couple of weeks, I STILL haven't been able to get this to work. But if your neighbor happens to have a ten year old child, maybe you could ask them to do it for you (unfortunately, I have elderly neighbors who think that typewriters are the latest cool thing).
PGP stands for Pretty Good Privacy and can be used to encrypt your emails into gibberish, for the person at the other end to decrypt. You both need private and public keys for this to work.
If you use Thunderbird, use Enigmail. If you use Outlook, you could try Outlook Privacy Plugin [Broken URL Removed], But if you are using Windows, you should install GPG4win, for Mac GPGTools, and for Linux, check out this good article. But encryption can also be achieved in webmail.
So what else can you recommend that will strengthen a person's security and privacy online? Leave your ideas and suggestions in the comments below.
Image Credits: looking at the laptop Via Shutterstock, Bandaid On a Webcam - Shutterstock, Password Strength - XKCD