When new instances of the widely distributed Locky ransomware began to dry up around the end of May 2016, security researchers were certain we had not seen the last of the file-encrypting malware variant.
Lo and behold, they were right.
Since June 19th security experts have observed millions of malicious email messages sent with an attachment containing a new variant of the Locky ransomware. The evolution appears to have made the malware vastly more dangerous, and are accompanied by an altered distribution tactic, spreading the infection further than previously seen.
It isn't just the Locky ransomware worrying security researchers. There have already been other variants of Locky, and it appears distribution networks are ramping up "production" across the globe, with no particular targets in mind.
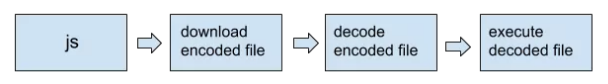
JavaScript Ransomware
2016 has seen a slight shift in malware distribution. Internet users may only just be beginning to understand the extreme menace ransomware poses, but it has already begun to evolve, in order to remain under the radar for as long as possible.
And while malware utilizing well-known JavaScript frameworks are not uncommon, security professionals were overwhelmed with a deluge of malware in the first quarter of 2016 leading Eldon Sprickerhoff to state:
"Malware evolution seems to be as rapid and cutthroat as any jungle environment, where survival and propagation go hand in hand. Authors have frequently co-opted functionality from different malware strains into the next generation of code — regularly sampling the efficacy and profitability of each generation."
The advent of ransomware coded in JavaScript presents a new challenge for users to attempt to avoid. Previously, if you accidentally downloaded, or were sent a malicious file, Windows would scan the file extension and decide whether or not this particular type of file poses a danger to your system.
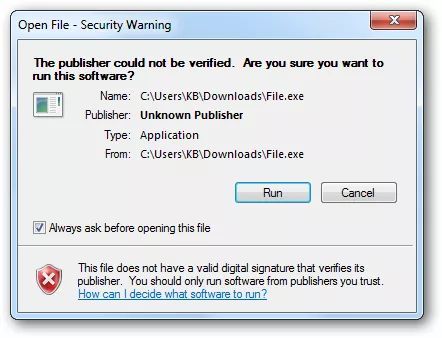
For example, when you attempt to run an unknown .exe file, you'll encounter this warning:
There is no such default warning with JavaScript -- the .js file extension -- files, which has led to a massive number of users clicking without thinking, then being held for ransom.
Botnets and Spam Email
The vast majority of ransomware is sent via malicious emails, which in turn are sent in huge volumes through massive networks of infected computers, commonly referred to as a "botnet."
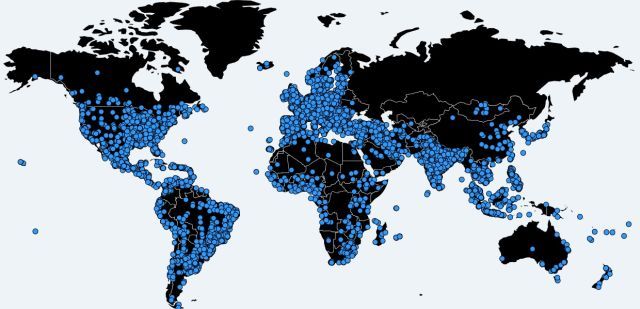
The huge rise in Locky ransomware has been linked directly to the Necrus botnet, which saw an average of 50,000 IP addresses infected every 24 hours for several months. During observation (by Anubis Networks), infection rates remained steady, until March 28th when there was a huge surge, reaching 650,000 infections over a 24-hour period. Then, back to business as normal, albeit with a slowly dropping infection rate.
On June 1st, Necrus went quiet. Speculation as to why the botnet went quiet is slim, though much centered around the arrest of around 50 Russian hackers. However, the botnet resumed business later in the month (around the 19th June), sending the new Locky variant to millions of potential victims. You can see the current spread of the Necrus botnet in the above image - note how it avoids Russia?
The spam emails always contain an attachment, purporting to be an important document or archive sent from a trusted (but spoofed) account. Once the document is downloaded and accessed, it will automatically run an infected macro or other malicious script, and the encryption process begins.
Whether Locky, Dridex, CryptoLocker, or one of the myriad ransomware variants, spam email is still the choice delivery network for ransomware, plainly illustrating just how successful this method of delivery is.
New Challengers Appear: Bart and RAA
JavaScript malware isn't the only menace users will have to contend with in the coming months -- although I do have another JavaScript tool to tell you about!
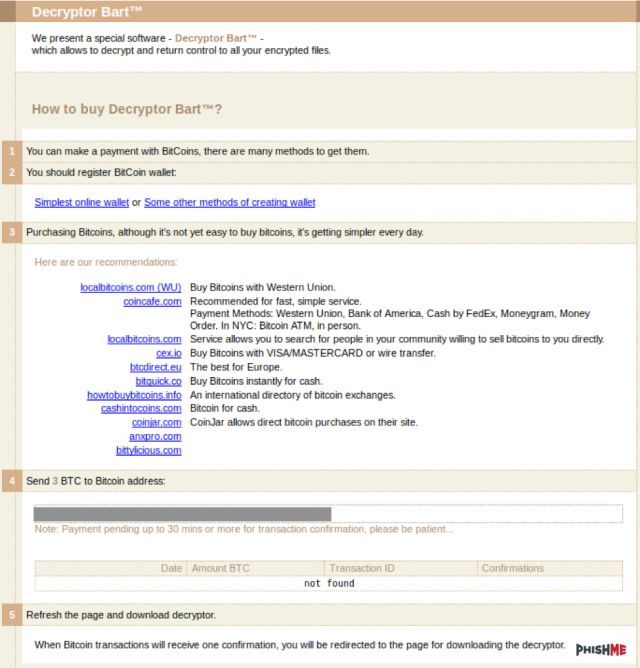
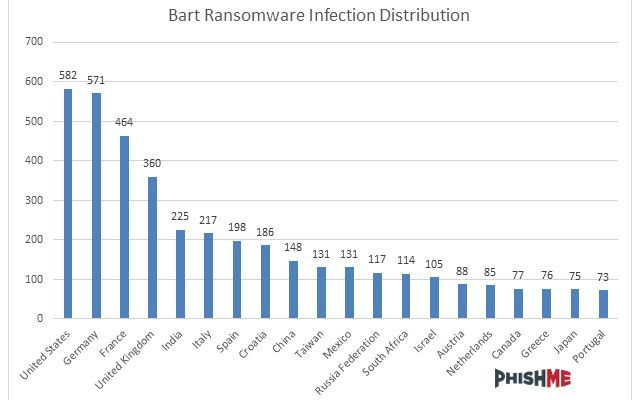
First up, the Bart infection leverages some pretty standard ransomware techniques, using a similar payment interface to Locky, and targeting a mainstream list of file extensions for encryption. However, there are a couple of key operational differences. While most ransomware need to dial home to a command and control server for the encryption green light, Bart has no such mechanism.
Instead, Brendan Griffin and Ronnie Tokazowski of Phishme believe Bart relies on a "distinct victim identifier to indicate to the threat actor what decryption key should be used to create the decryption application purported to be available to those victims who pay the ransom," meaning even if the infected is rapidly disconnected from the Internet (before receiving the traditional command and control go-ahead), the ransomware will still encrypt the files.
There are two more things that sets Bart aside: its decryption asking price, and its specific choice of targets. It currently stands at 3BTC (bitcoin), which at the time of writing equates to just under $2000! As for a choice of targets, it is actually more who Bart doesn't target. If Bart determines an installed user language of Russian, Ukrainian, or Belorussian, it will not deploy.
Second up, we have RAA, another ransomware variant developed entirely in JavaScript. What makes RAA interesting is its use of common JavaScript libraries. RAA is distributed through a malicious email network, as we see with most ransomware, and usually comes disguised as a Word document. When the file is executed, it generates a fake Word document which appears to be entirely corrupted. Instead, RAA scans the available drives to check for read and write access and, if successful, the Crypto-JS library to begin encrypting the user's files.
To add insult to injury, RAA also bundles well-known password stealing program Pony, just to make sure you're really, really screwed.
Controlling JavaScript Malware
Luckily, despite the obvious threat posed by JavaScript-based malware, we can mitigate the potential danger with some basic security controls in both our email accounts and our Office suites. I use Microsoft Office, so these tips will focus on those programs, but you should apply the same security principles to your whichever applications you use.
Disable Macros
First, you can disable macros from automatically running. A macro may contain code designed to automatically download and execute malware, without you realizing. I'll show you how to do this in Microsoft Word 2016, but the process is relatively similar for all other Office programs.
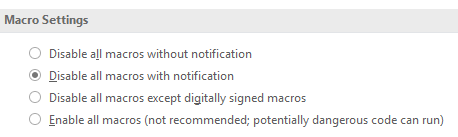
Head to File > Options > Trust Centre > Trust Centre Settings. Under Macro Settings you have four options. I choose to Disable all macros with notification, so I can choose to run it if I am sure of the source. However, Microsoft advise selecting Disable all macros except digitally signed macros, in direct relation to the spread of the Locky ransomware.
Show Extensions, Use Different Program
This isn't entirely foolproof, but the combination of the two changes will perhaps save you from double-clicking the wrong file.
First, you need to enable file extensions within Windows, which are hidden by default.
In Windows 10, open an Explorer window, and head to the View tab. Check File name extensions.
In Windows 7, 8, or 8.1, head to Control Panel > Appearance and Personalization > Folder Options. Under the View tab, scroll down the Advanced settings until you spot Hide extensions for known file types.
If you accidentally download a malicious file disguised as something else, you should be able to spot the file extension before execution.
The second part of this involves changing the default program used to open JavaScript files. You see, when you engage with JavaScript within your browser, there are a number of barriers and frameworks in place to attempt to stop any malicious happenings from ravaging your system. Once you're outside the sanctity of the browser and into the Windows shell, bad things can happen when that file executes.
Head to a .js file. If you don’t know where or how, enter *.js into the Windows Explorer search bar. Your window should populate with files akin to this:
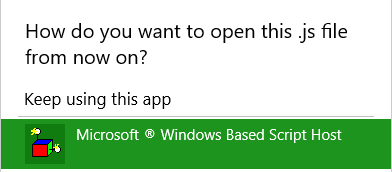
Right-click a file and select Properties. At the moment our JavaScript file opens with Microsoft Windows Based Script Host. Scroll down until you find Notepad and press OK.
Double-Check
Microsoft Outlook doesn’t let you receive files of certain type. This includes both .exe and .js, and is to stop you inadvertently introducing malware to your computer. However, that doesn’t mean they cannot and will not slip through both other means. There are three extremely easy ways ransomware can be repackaged:
- Using file compression: the malicious code can be archived, and is sent with a different file extension that doesn’t trigger Outlook's integrated attachment blocking.
- Rename the file: we frequently encounter malicious code disguised as another file type. As most of the world uses some form of office suite, document formats are extremely popular.
- Using a shared server: this option is a little less likely, but malicious mail can be sent from a private FTP or secure SharePoint server if compromised. As the server would be whitelisted within Outlook, the attachment wouldn't be picked up as malicious.
See here for a full list of which extensions Outlook blocks by default.
Constant Vigilance
I'm not going to lie. There is an omnipresent threat of malware when you're online -- but you don’t have to succumb to the pressure. Consider the sites you're visiting, the accounts you're signing up to, and the emails you're receiving. And even though we know it is difficult for antivirus software to maintain pace with the dazzling array of malware variants churned out, downloading and updating an antivirus suite should absolutely form part of your system defense.
Have you been hit by ransomware? Did you get your files back? Which ransomware was it? Let us know what happened to you!
Image Credits: Necrus botnet infection map via malwaretech.com, Bart decryption interface and Current infections by country both via phishme.com