What motivates people to hack computers?
If you guessed "money", you're spot on. But how on earth do you monetize a compromised server? It turns out that criminals are a smart bunch, and have came up with a number of unusual ways to make their misdeeds pay. Here are three.
Mine Bitcoin
Cryptocurrencies are big business. One of the biggest is BitCoin, which has a market cap (at the time of writing) of almost $3.6 billion dollars. Unlike a traditional currency, which is printed by a central bank, anyone can "mine" BitCoin. All you need is a computer, and a freely available piece of software, and you can start mining.
You can use any computer, from a low-power Raspberry Pi (although, this isn't recommended), all the way to a high-powered virtual private server (VPS). And what's more, the server doesn't even need to be your own. This is something Portuguese software developer Pedro Rio discovered last January, when he was the victim of a Bitcoin-driven hack attack.
When Pedro registered a new VPS, he immediately took efforts to 'harden' it. Despite being a programer by trade, he knew this wasn't his area of expertise. Writing on his blog, he says "I’m not really a system administrator nor do I have much experience on the matter".
He configured his server to be as difficult as possible to compromise, and to send out email alerts at the first scent of any suspicious behavior. On January 17th, he received an email alert informing him his CPU had been running at 90% usage for the past two hours. Pedro logged on, and started to investigate.
"I logged in my VPS and used the top command to find that a single process was using all CPU. ... with a bit of googling I traced it to bitcoin mining."
Someone had managed to compromise his system and install a Bitcoin miner. Had Pedro not been so vigilant, it would have continued to consume his system resources, silently printing money for his attacker. Pedro has since rebuilt his system from scratch, and learned his lesson.
Some people aren't so lucky.
Joe Moreno's monthly Amazon EC2 bill is usually no more than $6. But last April, he got a nasty surprise when he discovered his monthly bill was over $5,000. Someone had gotten into his account and launched high-powered server instances across the world. In Tokyo, Sydney, Sao Paulo and Singapore, powerful servers were quietly mining Bitcoin, and Joe was footing the bill.
The attackers had compromised his account through credentials he mistakenly uploaded to Github. A repository he created a few years earlier had contained his Amazon EC2 API keys, which was all the hacker needed to spawn and gain control of newly created server.
Fortunately for Joe, Amazon were gracious enough to forgive his massive debt, and today Joe is a lot more careful with where he leaves his credentials.
Launch Online Attacks
The criminal penalties for computer offenses can be quite steep, with offenders often being put away for decades. Albert Gonzales, for example, was sentenced to 20 years in jail for the the theft of 170 million credit card numbers from clothes retailer TJ Maxx. With that in mind, it makes sense that any prospective hacker would want to cover his tracks, and how better than through your server.
Of course, servers are just like any other computer. You can launch virtually any attack from a compromised VPS, although it's quite common for them to be used in DDoS attacks.
Distributed Denial of Service Attacks (DDoS) are when a large pool of zombified systems are assembled and used to attack a single target. Usually, they send vast quantities of data to try and overwhelm the target, with the aim of preventing any legitimate usage of it.
Compromised servers come in all shapes and sizes, as Sucuri found out in 2014 when they were victim of a DDoS attack. The attack involved a botnet of almost 2000 web servers, m as many as 5,000 HTTP requests per seconds. Their investigation found servers running both Windows and Linux were used, and they ran a diverse range of software packages. In short, there's no "standard issue" zombie server.
As you can imagine, DDoS attacks are incredibly lucrative, with people spending thousands to disrupt a target over a long period of time. A 2012 blog post from FSecure discovered a burgeoning marketplace in compromised servers, with one retailer charging $2 per hour for a DDoS attack. Surreally, some retailers even have video adverts.
Reselling
It was not an unusual hack. First, Andrew Morris's SSH credentials were brute-forced. Once the hacker had gained control of his system, they then installed a backdoor program that would allow them to remotely-access his system at their very whim.
But what they didn't realize was that Andrew was watching. The hacker had actually found what's known as a 'honeypot' - a system left intentionally secure to attract hackers, so a researcher can observe their behavior.
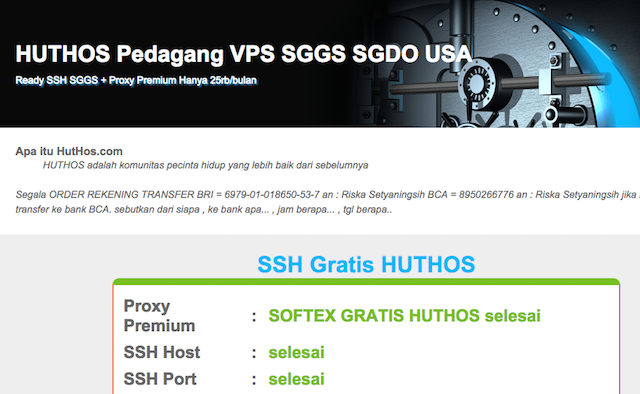
It was through this honeypot that Andrew discovered Huthos - an East-Asian provider of VPS services which he alleges is reselling stolen servers.
Although not totally conclusive, the evidence is pretty damning. Not only is the malware distributed from their website, and uses resources stored on their web server, but it also references their (since deleted) Facebook account. The malware also sets the timezone of the compromised system to that of Jakarta, where Huthos are based.
Apparently people can be this dumb.
If you're tempted, A stolen VPS can be yours for as little as 59,500 Indonesian Rupiah, payable via bank transfer. That's just short of $5, or how much it costs to provision a Digital Ocean droplet.
Lessons Learned
Far from merely being 'for the lulz', there's an impressively lucrative cottage industry around stealing VPS servers. So, what can you do? Well, firstly, consider asking yourself whether you actually need a server. Quite often, managed services, especially for hosting simple websites and blogs are more than enough. If you're a developer, consider using a managed PaaS service like Heroku or Google App Engine.
If you absolutely need to run your own server, take care to harden it, and to set up stringent security checks and alerts.
Ever had a server hacked? What did the attackers do, and what did it cost you? I want to hear about it. Drop me a comment below, and we'll chat.
Photo Credits: tap with money Via Shutterstock, hacker Via Shutterstock, server room Via Shutterstock, Bitcoin (Zach Copley), Server room (Torkild Retvedt), TJ Maxx (Mike Mozart)