At this year's Black Hat Europe security conference, two researchers from the Chinese Hong Kong University presented research that showed an exploit affecting Android apps that could potentially leave over one billion installed applications vulnerable to attack.
The exploit relies on a man-in-the-middle attack of the mobile implementation of the OAuth 2.0 authorization standard. That sounds very technical, but what does it actually mean, and is your data safe?
What Is OAuth?
OAuth is an open standard used by many websites and apps to allow you to log in to a third-party app or website by using an account from one of the many OAuth providers. Some of the most common and well known examples are Google, Facebook, and Twitter.
The Single Sign On (SSO) button allows you to grant access to your account information. When you click the Facebook button, the third-party app or website looks for an access token, granting it access to your Facebook information.
If this token isn't found you will be asked to allow the third-party access to your Facebook account. Once you have authorized this, Facebook receives a message from the third party asking for an access token.
Facebook responds with a token, granting the third-party access to the information you specified. For example, you grant access to your basic profile information, and friends list, but not your photos. The third-party receives the token and allows you to login with your Facebook credentials. Then, as long as the token doesn't expire, it will have access to the information you authorized.
This seems like a great system. You have to remember less passwords, and get to easily login and verify your information with an account you already have. The SSO buttons are even more useful on mobile where creating new passwords, where authorizing a new account can be time consuming.
What's the Problem?
The most recent OAuth framework -- OAuth 2.0 -- was released in October 2012, and was not designed for mobile apps. This has led to many app developers having to implement OAuth on their own, without guidance on how it should be done securely.
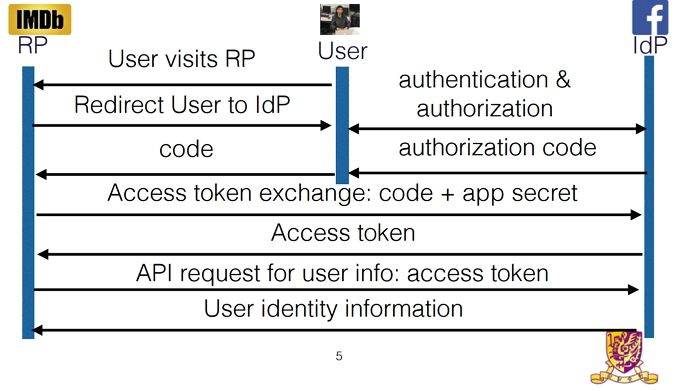
While OAuth on websites uses direct communication between the third-party and SSO provider's servers, mobile apps do not use this direct communication method. Instead, mobile apps communicate to one another through your device.
When using OAuth on a website, Facebook delivers the access token and authentication information directly to the third-party servers. This information can then be validated before logging the user in or accessing any personal data.
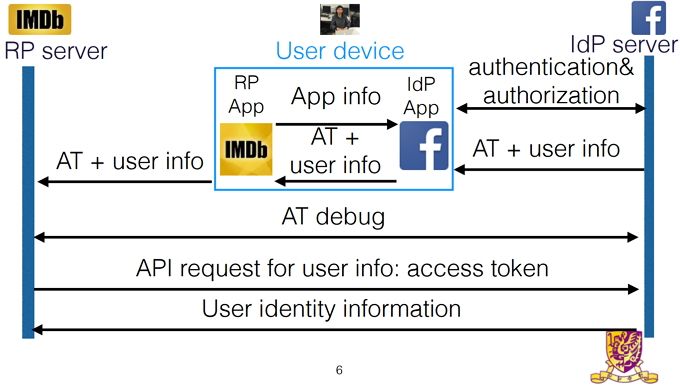
The researchers found that a large percentage of Android applications were missing this validation. Instead Facebook's servers send the access token to the Facebook app. The access token would then be delivered to the third-party app. The third-party app would then allow you to login, without verifying with Facebook's servers that the user information was legitimate.
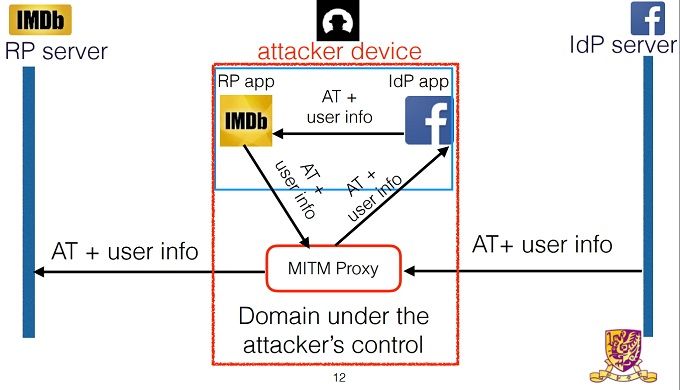
The attacker could login as themselves, triggering the OAuth token request. Once Facebook has authorized the token, they could insert themselves in between Facebook's servers and the Facebook app. The attacker could then change the user id on the token to the victim's. The username is usually publicly available information too, so there are very few barriers for the attacker. Once the user ID has been changed -- but the authorization still granted -- the third-party app will login under the victim's account.
This type of exploit is known as a man-in-the-middle (MitM) attack. This is where the attacker is able to intercept and alter data, while the two parties believe they are communicating directly with each other.
How Does This Affect You?
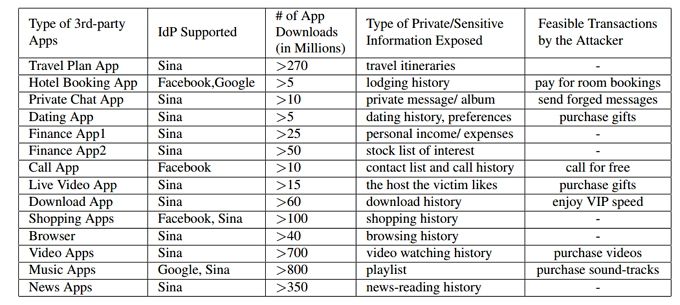
If an attacker is able to fool an app into believing that he is you, then the hacker gains access to all the information that you store in that service. The researchers created the table shown below which lists some of the information you may expose on different types of apps.
Some types of information are less damaging than others. You are less likely to be worried about exposing your news reading history than all your travel plans, or the ability send and receive private messages in your name. It's a sobering reminder of the types of information we regularly entrust to third-parties -- and the consequences of its misuse.
Should You Worry?
The researchers found that 41.21% of the 600 most popular apps that support SSO on the Google Play Store were vulnerable to the MitM attack. This could potentially leave billions of users around the world exposed to this type of attack. The team conducted their research on Android but they believe that it can be replicated on iOS. This would potentially leave millions of apps on the two largest mobile operating systems vulnerable to this attack.
At the time of writing, there have been no official statements from the internet Engineering Task Force (IETF) who developed the OAuth 2.0 Specifications. The researchers have declined to name the affected apps, so you should exercise caution when using SSO on mobile apps.
There is a silver lining. The researchers have already alerted Google and Facebook, and other SSO providers of the exploit. On top of that, they are working alongside the affected third-party developers to fix the problem.
What Can You Do Now?
While a fix might be on its way, there are a lot of affected apps to be updated. This is likely to take some time, so it might be worth not using SSO for the meantime. Instead, when you register for a new account, make sure you create a strong password you won't forget. Either that or use a password manager to do the heavy lifting for you.
It's good practice to conduct your own security checkup from time to time. Google will even reward you in cloud storage for performing their checkup. This is an ideal time to check out what apps you have given permission to on your SSO accounts. This is especially important on a site like Facebook, which stores a tremendous amount of very personal information.
Do you think it's time to move away from Single Sign On? What do you think is the best login method? Have you been affected by this exploit? Let us know in the comments below!
Image Credits: Marc Bruxelle/Shutterstock