Malware that targets the browser is nothing new. But malware that replaces an already existing browser with one designed to track online movements, hijack search traffic, and fill each page with unwanted adverts? Yeah, that's pretty interesting.
The eFast Browser was discovered by the MalwareBytes team a few days ago, and it does all of the above, and more.
Pulling an eFast One
Perhaps the worst thing about eFast Browser is that unless you're especially observant, you might not even notice it's there, as it takes great pains to camouflage itself.
For starters, it looks and feels like the bona-fide Chrome browser, as it's built on the Chromium Browser. This is essentially the wholly open-source version of Chrome, with some proprietary components removed.
Astonishingly, the developers have even designed the logo to closely resemble the iconic Chrome "Spiral".
But behavior-wise, it's very similar to other malicious adware. It starts off by uninstalling the official version of Chrome. When you use it as a browser, eFast will track, and insert advertisements into every single webpage you visit. It'll hijack your search traffic, and try to direct you to other malicious pages.
It also associates itself with a broad smorgasbord of file formats, perhaps in order to drive users to use it more. These formats are:
- gif
- htm
- html
- jpeg
- jpg
- png
- shtml
- webp
- xht
- xhtml
It also associates itself with the following URL associations:
- ftp
- http
- https
- irc
- mailto
- mms
- news
- nntp
- sms
- smsto
- tel
- urn
- webcal
The motivations behind the eFast browser are, of course, purely financial.
Malware developers are overwhelmingly motivated by financial reasons, and this is no exception. In fact, it stands to earn the makers a decent amount of cash, as their adverts are displayed on every single website you visit. The vast potential for illicit money-making is what drives malware developers to target the browser.
The Attraction of The Browser
The browser has always painted an enticing target for malware developers, simply because of how we use it, and how often we use it. For many, their computing experience is based wholly in the browser.
At the very least, the vast majority of us use our web browsers for social networking, entertainment, and shopping. Beyond that, many more use it as for office productivity, with products like Google Drive having thoroughly supplanted Microsoft Office, and Gmail having all but replaced Outlook and Exchange.
Because the browser holds such an esteemed position, it presents an enticing opportunity for malware developers. At their most benign, they can simply insert unwanted adverts and hijack search traffic, but at their worst, they can steal passwords, credentials, and banking information.
Google, to their credit, have realized the threats posed to their own browser and have done their best to make it as secure as possible.
Each Chrome tab is tightly sandboxed, and Google have taken great pains to make it extremely hard for drive-by-downloads to take place. In May this year, Google took the decision to ban non-Web Store extensions. If you want to publish your own Chrome extension, it has to go through Google, and their rigorous code analysis.
As InfoSecTaylorSwift so saliently pointed out, Chrome is now so secure, the only way to attack the browser is to replace it.
Who's Behind It?
By now, we know the eFast Browser comes with some pretty horrendous behavior, and we know that it's being installed surreptitiously on people's computers. But who actually made it?
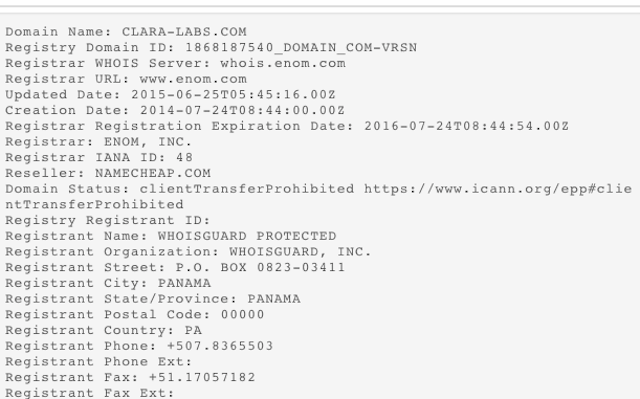
A good starting point is to look at its digital certificate. This has been signed by "CLARALABSOFTWARE", with "clara-labs.com" listed as the associated domain name.
Their choice of name almost certainly wasn't an accident. Not only does it closely resemble other tech companies (like UK ISP Claranet), it also sounds like what a legitimate tech company would call themselves.
I then queried their Whois record. This is a publicly-accessible record of who owns the site, and contains their contact information. However, it's possible to "opt-out" of Whois by using a third-party obfuscation service, like WhoisGuard. Unsurprisingly, this is what they've done here.
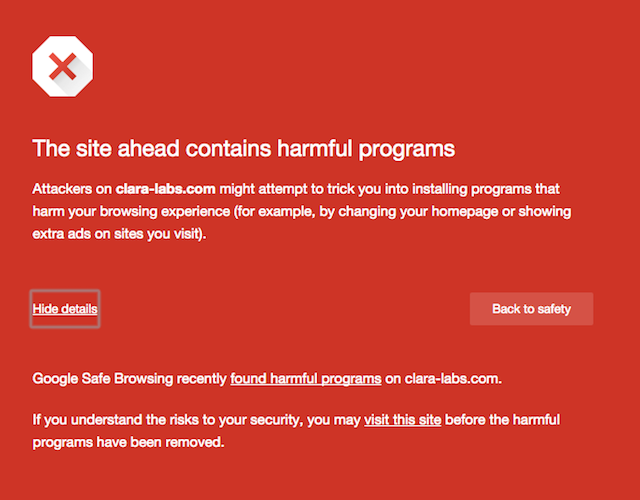
So, I decided to visit the Clara Labs homepage (we're not going to link to it directly), to see if I could find any identifiable information. It's worth pointing out that when you visit it with Chrome, Google warns you not to continue further, and states it's a known distributor of malware.
When I visited, the site was under a lot of strain, thanks to the traffic generated by the immense media interest that it's seen over the past few days.
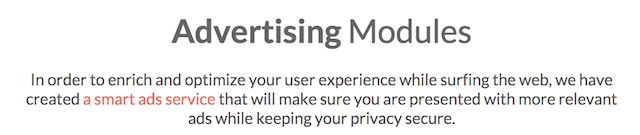
When it finally loaded, I was a little bit underwhelmed. Most of the content was the type of tedious web copy that's guaranteed make your eyes glaze over. It mostly blathered on about "enriching the user experience" through their "smart ads platform", almost as though people should be grateful.
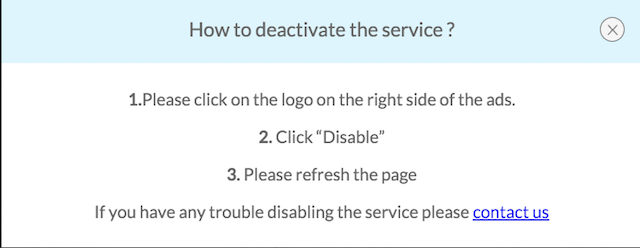
More interestingly, it come with simple instructions on how to disable the built-in adverts:
Although, if you're in the position where you've got it installed, you'd be much better off uninstalling it entirely.
There wasn't much contact information on the site. There wasn't anything that said who was running it, or what jurisdiction they were based in. There was no contact number, or postal address. There was an email address, however. I've got in touch and asked for a comment.
I'll update this post if they reply, but I'm not getting my hopes up.
Getting Rid of eFast Browser
Do you think you've been infected? Well, there's a simple test. Type “chrome://chrome” into the address bar. If you see something that says "About eFast", then you've definitely been infected.
If it's not there, but you're still seeing strange behavior, your problem might come from another source. Download an anti-malware program, and do some investigation. We also have some generic advice on how to deal with hijacked browsers, and specifically how to un-hijack Chrome.
If you're infected with eFast, you'd be wise to download MalwareBytes (which we first covered in 2009). The developers of this were the ones who discovered eFast, and their anti-virus has the correct definitions to remove it.
Were you infected by eFast? Know anyone who was? Tell me about it in the comments below.
Image Credits:Red Devil's hands by Alex Malikov via Shutterstock