Oh dear. Not this again. 68 million Tumblr accounts have been splashed onto the dark web, and are being sold for the paltry price of 0.452 bitcoins. At the time of writing, that's about $240.
At first glance, you can draw a parallel between this data leak and the LinkedIn leak of two weeks ago. Firstly, both datasets are really old; the LinkedIn breach dates from 2012, and the Tumblr one is from 2013. Both datasets are huge, and they were both listed on the Dark web by the same person -- Peace_Of_Mind.
But that's where the similarities end, because while LinkedIn didn't secure its passwords properly, Tumblr's were protected with (relatively) strong SHA-1 encryption. This means that there's little chance of an attacker breaking into their Tumblr accounts, or recycling the login combinations on other services, like Facebook, PayPal, or Twitter.
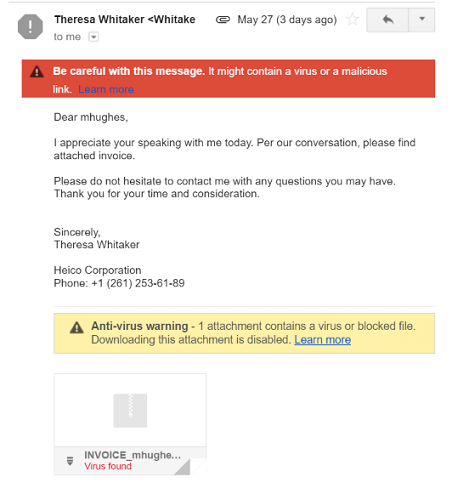
There's a downside though. An attacker who purchases the dump now has a list of 68 million active, verified email accounts. This means that any user caught up in it is at a greater risk of phishing and email-based attacks.
So, what does phishing look like in 2016, and what steps can you take to protect yourself?
Phishing Isn't Passé
If you hadn't encountered the report from Vice's Motherboard, you could be forgiven for thinking that phishing is a dusty relic of the 1990s and early 2000's, harking back to Internet's novel infancy, and nobody really knew how things works. Surely, you argue, nobody falls for phishing emails any more.
The statistics would care to disagree. Firstly, phishing emails are still being sent in improbably large numbers. According to the Kaspersky-owned SecureList, phishing and spam emails accounted for 54.2% of all emails sent in the third quarter of 2015. This was a slight drop from the previous quarter, but is still a remarkable amount of messages.
The largest source of phishing emails is the United States, followed closely by Vietnam, China, and Russia. Interestingly, the country with the most users affected by phishing is Brazil, which is followed by Japan, China, and Vietnam. Neither the United States -- nor any other developed, Western country, for that matter -- is in the top-ten.
But while the rate of overall malicious and spam emails has dropped slightly, the number of phishing emails has soared. According to Symantec [Broken URL Removed], the proportion of phishing emails rose in January 2015 from one in 1,517 emails, to one in 1,004.
Anti-Spam Is Getting Smarter, but so Are Phishing Emails
Back in the 1990s and 2000s, anti-spam software was unsophisticated and barely fit for purpose. Many programs did little besides look for keywords -- like 'viagra' -- and trash any email that contained them. Spammers and phishers got around them by intentionally misspelling the words that were on the keyword list. So, 'viagra' became 'v1agra', which then became 'v1agr4', and then 'v1a8r4'. You get the idea.
Some got even more creative, and started hiding the words among images and specially-colored tables.
The end result was that users were being literally flooded with spam and phishing attacks. But that changed towards the tail end of the 2000s, when anti-spam finally got smart. Faster computers meant that online email services -- like Gmail and Outlook -- could do complicated calculations in real time, which determined whether an email would be sent to the user's inbox, or to the spam folder.
Rather than just looking for keywords, spam filters started looking at things like the origin of the email message, and the behavior of other users to emails of a similar nature.
The spammers haven't given up. In fact, according to Securelist, they're getting even smarter, and it's becoming even harder to spot a phishing email.
One of the things Securelist noted in its report is that spammers often take a seasonal approach to spam and phishing. During the summer, it noted that the number of phishing emails with a travel theme soared.
"In July, fraudsters tried to trick users by sending fake notifications on behalf of hotels. The message thanked the recipients for staying in their hotel and asked them to view the attached bill. The attached archive actually contained Trojan-Downloader.Win32.Upatre.dhwi, which in turn downloaded and ran Trojan- Banker.Win32.Dyre (viewed as 98. ***. **. 39/cv17.rar) by clicking the links written in the body of the downloader."
One tactic used to bypass anti-spam programs is to put everything in a PDF file, which the user would then open. This is effective because it's remarkably difficult to programmatically 'read' a PDF file.
When anti-spam filters wised up to this trick, the spammers started using mediabox objects in attached PDF files, elements in PDF documents that are opened by a mouse-click. They can be used to redirect the user to phishing websites.
This game of cat-and-mouse shows no sign of ending, with a clear winner. In fact, the war might be intensifying.
Legitimate Services Customize Their Emails, but so Do Attackers
In order to protect their users from phishing emails, online services -- especially online banking services -- have taken to customizing their emails with a small 'token' that is unique to the user. One of the banks I use includes the final three digits of my account number on all electronic correspondence. Another puts the first three characters of my postcode at the top of all emails.
This is something you should always look for.
Interestingly, attackers have also started personalizing their emails to be more effective. One thing I've noticed is that some phishing emails have started taking the first part of an email address (everything before the '@'), and putting it in the salutation. My work email is 'mhughes@makeuseof.com', so these emails will start with 'Dear mhughes'.
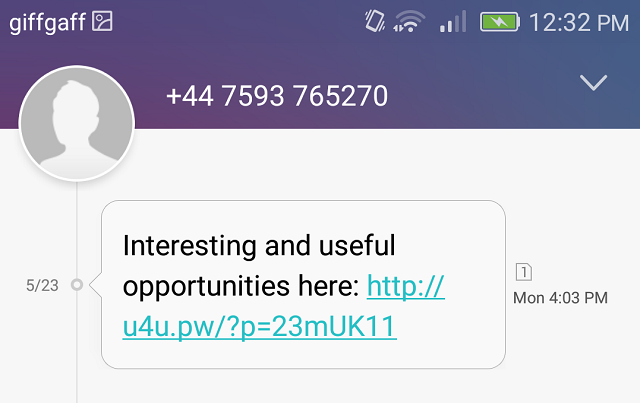
Text Messaging -- The Next Frontier of Phishing
Increasingly, the online services we use are being linked with our mobile devices. Some services ask for your phone number in order to set up two-factor authentication. Others ask for it in order to share information with you.
Sites don't protect mobile numbers in the way that they do passwords. The reason for that is when you hash-and-salt a password, it becomes impossible to read. In order for sites to send messages or call a number, they have to keep it unprotected.
This fact, coupled with extremely cheap (completely legitimate) text messaging services like Twilio, Nexmo, and Plivo, (which people are less suspicious of), means that attackers are increasingly leaning on SMS as an attack vector.
This type of attack has a name: smishing, while voice phishing is called vishing.
Get Suspicious
If you don't know whether you're in the Tumblr dump, you can find out by heading to Troy Hunt's Have I Been Pwned.
If you are, it's a good idea to reset your passwords, and to set up two-factor authentication on all your accounts. But more importantly, you should crank your suspicion-meter to eleven. I have no doubt that affected users will see an increase in spam and phishing emails in the coming weeks. They'll look convincing. To stay safe, Tumblr users need to start treating any inbound emails with a healthy dose of skepticism.
Have you been caught up in the leak? Gotten any suspicious emails? Let me know in the comments below.
Photo Credits: HTML Table Bitmap (Niels Heidenreich)