Ex Intel CEO, Andy Grove once said, "Only the paranoid survive". When it comes to being online, he's absolutely right. Everything you do online nowadays should be approached with a healthy amount of cynicism.
Installing a free anti-virus program and forgetting about security simply doesn't cut the mustard. So in this article, we're going to look at some of the simple steps you can take to secure your entire online life.
Use Two-Factor Everywhere (Especially With Email)
Two-factor authentication is a quick and simple way of securing many of the tools that you use online. It basically uses something you know, like your password, and something you have, like your phone, to generate a code before you are able to log in.
Your email address is the skeleton key to all of your online services. If an attacker gets in to your emails, it's all over as attackers can quickly generate password reset links to get in to all of your other accounts.
By enabling two-factor on your email account, you add the extra layer of security to prevent attackers from getting in. So unless they have your phone and your user account details, they're very unlikely to get in.
All of the main email providers like Gmail, Outlook and Yahoo! will allow you to use two-factor. If you're a Gmail user, there are also some extra security measures you can take.
There are many other services that off two-factor, not just email. So enabling it for as many of the services that you use as possible will bolster you security. At first it may be frustrating to get to grips with, but you soon get used to it.
Encrypt Your Device
Encryption will ensure that if your device goes missing, the data stored on it is safe and secure. Windows, Mac, Linux, Android and iOS all offer free encryption options, so there really isn't any excuse for not encrypting.
For Windows and Mac, it's BitLocker and FileVault, respectively. For Linux, you simply need to check the box "encrypt home partition" during the installation process.
When it comes to mobile devices, iOS is encrypted by default, as are many modern Android devices. However, if you have an Android device that isn't encrypted by default, it can be easily turned on.
Protect Your Lock Screen
These days, many smartphones and tablets come with fingerprint recognition for unlocking your device. It's obviously more secure than having nothing at all, but a PIN on your lock screen is better than using fingerprint recognition. "Why?" I hear you yell.
It's simple really. The fifth amendment has a safeguard in place to prevent self-incrimination. If a government body were to ask you to unlock your device, you could forget your PIN, but you can't change your fingerprint.
So with a court order, you could be forced to unlock your device. With a PIN, its not so simple. Not to mention, having a protected lock screen can stop the opportunist from getting at your phone.
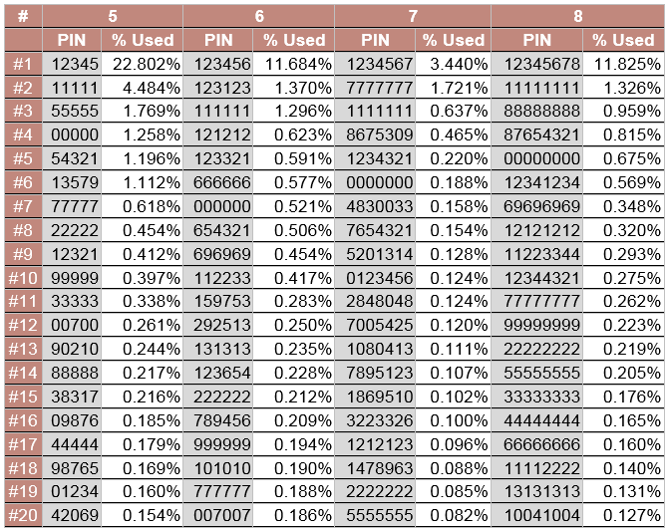
When setting a PIN, be sure to use something that isn't obvious. Data Genetics did a recent survey on PIN codes, and the table above shows the 20 most common of the 7 million sampled.
Most of the PIN codes in the table above follow some kind of pattern. Us humans love patterns, so if you stick to a PIN that doesn't have an obvious pattern, then it's less likely to be guessed.
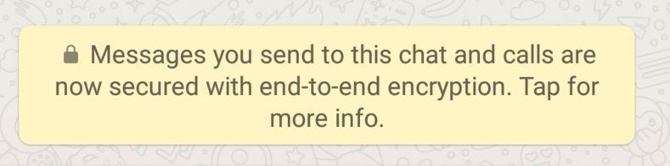
Encrypt Your Text Messages
Services like Whatsapp now encrypt by default. This is great because it stops anyone from spying on your private conversations. However, it doesn't support standard text messaging and the recipient needs to be using Whatsapp as well.
There are alternatives to Whatsapp that allow for end-to-end encryption, such as Telegram and Signal. All these tools also allow you to make encrypted calls, so can be a lot more secure than traditional calls or text messages.
Edward Snowden himself actually recommends Signal.
The vast majority of people nowadays do have Whatsapp on their phone, as it's more secure and has more functionality than a simple text message. So even though it's a requirement for your friends to have the app as well, it's not really an issue any more.
If you don't have Whatsapp on your device, I urge you to start using it ASAP. It's free, after all.
Search in Private
Many people know that Google is a privacy black hole, yet it's still the site that most people turn to when they have a question about pretty much anything.
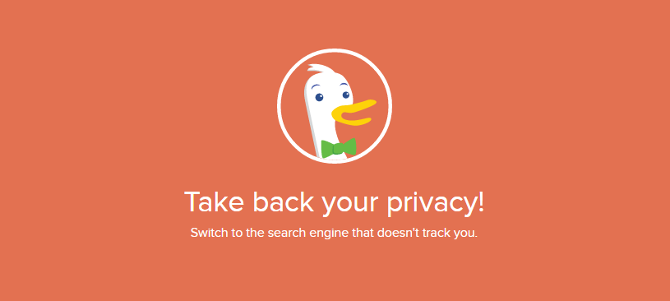
But there are alternative search engines out there that don't store information about you. So you get the answers to your questions, and your privacy remains in tact. The biggest of these privacy aware search engines is DuckDuckGo.
The DuckDuckGo privacy policy is very simple. The first line reads: "DuckDuckGo does not collect or share personal information." So you can search on DuckDuckGo safe in the knowledge that your personal data is not being harvested.
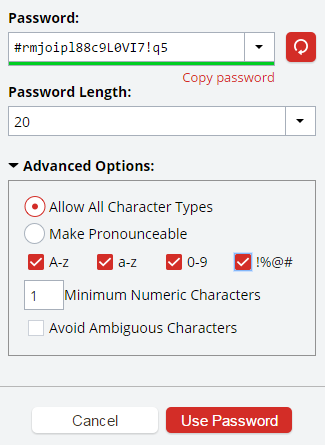
Get a Password Manager
Having the most secure password in the world doesn't mean anything if it's the same for every site you use. If one of your accounts gets compromised, then all of your accounts are effectively compromised along with it.
The solution is a password manager, like LastPass. A password manager will allow you to generate random passwords and will automatically log you in to sites you have stored.
This means that you only need to remember to main password for your manager, and it will do all the hard word for you. Just don't forget to enable two-factor authentication on your password manager!
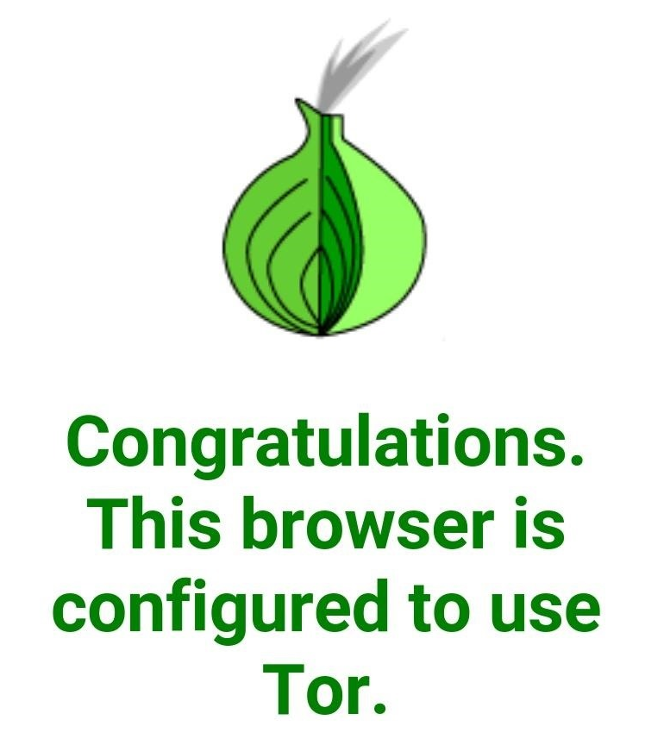
Use Tor (Not Incognito)
Incognito mode, or private browsing if you don't use Chrome, allows you to surf the web anonymously, and no one can see what you have been up to. It's great, right? Wrong!
If you're using incognito mode on your machine, your internet service provider, network administrators and the makers of your browser can still see what you have been looking at online.
It's a common misconception that incognito mode is private. It isn't, it just doesn't save any history to the local machine. If you want a way to browse the internet more privately, take a look at Tor.
On the desktop, it's as simple as downloading and installing the Tor Browser (which is based on Firefox, so should be familiar to most).
If you're on a mobile device, you can still use Tor to browse the internet. There are apps like Orbot for Android and VPN Browser for iOS.
Tor isn't 100% secure. Nothing is. But if you want truly private browsing, Tor is the closest that most people will get.
This Is How You Stay Secure
It's important to remember that it is impossible to remain 100% secure whilst online. Attackers will always find a way in, given enough time.
These tips will make a would-be attacker's life very difficult, but that doesn't mean you should ever let your guard down. Remember, only the paranoid survive!
Do you have any other tips for staying secure online? If so, feel free to share them below.
Image Credit: LeoWolfert via Shutterstock.com