Android phones, and Linux desktops and servers all share a common ancestry. They're all based on a common kernel, and share common utilities and components. Whenever a security vulnerability is found in these areas, the contagion is massive, and hundreds of millions of computers and mobile devices will inevitably be affected.
A recently discovered vulnerability (CVE-2016-0728) in the Linux kernel is an astonishing example of this. It takes advantage of a flaw in the OS keyring, and would allow any unprivileged attacker or user to gain root access to the system in question. Here's how it works, and what you need to be wary of.
Understanding This Vulnerability
This vulnerability was discovered by Perception Point – a major Tel Aviv based information security consultancy firm. The flaw was first introduced around three years ago, with the release of the Linux Kernel version 3.8. Perception Point estimate that around two-thirds of Android devices, and an unknowable amount of Linux desktops and servers (probably in the tens of millions) are vulnerable.
As previously mentioned, this flaw is found in the OS keyring. This is the component used in Linux which allows drivers to cache security data, such as encryption keys and authentication tokens. By design, the data held in the OS keyring shouldn't be accessible to other applications.
The exploit itself takes advantage of a flaw with how memory is managed in the OS Keyring. By executing a buffer overflow, the attackers can trigger the operating system to running some arbitrary shellcode, which would be executed as root.
It's expected that the majority of Linux distributions will issue fixes by the start of next week. But if you've got a modern Intel processor (Broadwell or later), SMAP (Supervisory Mode Access Prevention) and SMEP (Supervisory Mode Execution Prevention) should be enabled, and will limit the damage this vulnerability can inflict.
Meanwhile, if you're on Android, SELinux should likewise do the trick. It's worth pointing out that Google has vehemently downplayed the risks presented by this vulnerability. In a statement, they said that all devices running Android 5.0 Lollipop and later are protected by SELinux, and the majority of older devices (running Android 4.4 KitKat and earlier) do not contain the vulnerable code that was introduced in version 3.8 of the Linux Kernel.
The Android Security Team also complained that they weren't given notice to issue a patch. Essentially, they said that the Perception Point didn't perform responsible disclosure.
Essentially, they're not saying there isn't a problem, but that it affects a much smaller proportion of Android devices as was earlier claimed by Perception Point. Despite that, they're issuing a fix, which when released, should close this gaping vulnerability once and for all.
Checking Your Privilege
One of the most fundamental principles of computer security can be succinctly summed up as: not all users should be able to do all things at all times.
If a user was perpetually logged in as root, or administrator, it would be significantly easier for a piece of malware or a remote attacker to cause significant damage. It is for this reason why most users and applications exist in a restricted mode with limited permissions. When they want to do something that could result in damage to the computer – such as install a new program or change an important configuration file – they must first elevate their privileges. This concept is universal, and can be found of virtually every operating system.
Suppose someone is logged into a Linux or Mac computer with an administrator account, and they wish to edit their hosts file to remap a hostname to a local IP address. If they just try to open it immediate with a text editor, the operating system will return with an error message saying something like "access denied".
To make it work, they'd have to elevate their privileges. They can enter superuser mode indefinitely by running "sudo su". This is helpful if they're going to be running a series of restricted actions, over an unspecified amount of time. To exit this mode and return to the normal user account, simply use the "exit" command.
To run just one command as super user, just preface that command with "sudo". Using the example of the hosts file, you can edit it with "sudo vim etc/hosts". You will then be prompted for your password. If the account doesn't have administrator privileges (i.e. is a standard user account), the command will fail to work.
On Android, they have a fundamentally different model of permissions, where applications are atomized and sandboxed, and users can make limited under-the-hood changes. Users are actively discouraged from gaining access to the root. It's for this reason why most carriers and manufacturers (with HTC among the exceptions) actively discourage users from rooting their phones, and why it's become a bit of a "dark art".
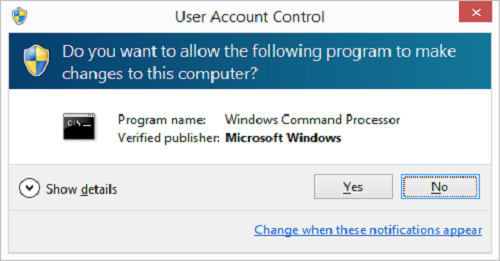
Windows too has its own system of elevated privileges. Whenever a program makes a change to the system which requires enhanced permissions, Windows will prompt the user with a UAC window (User Access Control). This shows the program that's requesting elevated permissions. If the code has been given a cryptographic signature, it'll show who signed it, allowing you to spot impostor programs. The user can then choose to give the program the permissions requested, or decline.
While this process is not without its flaws (UAC windows are regarded as rather annoying, and are generally just 'clicked away', for instance), it's one that generally works. However, it can be easily circumvented by flaws in the operating system, much like the one identified by Perception Point.
Increasing Threats to Linux Devices
In recent years, we've seen a deluge of attacks targeting Linux-based operating systems, as it cements its hold on the server market, and increases its market share on the desktop.
Recently, researcher in Russia discovered a Remote Access Trojan that was designed to help an attacker spy on users. Called Linux.Ekoms.1, the Trojan takes a screenshot every 30 seconds and saves it in a temporary folder as a JPEG disguised with a different file extension. Further analysis of the Trojan revealed that the developers were working on features that would allow it to record audio. These files would then be sent to a remote server. The attackers would also be able to issue commands through a command-and-control server.
Another rootkit for Linux – called Snakso-A – targeted 64-bit Linux webservers, and silently hijacked the webpages that were being served, in order to inject a malware-serving iFrame.
Then, of course, there are the vulnerabilities which were so severe, they became international news. I'm talking about the likes of Shellshock, the GHOST vulnerability, and Heartbleed.
These threats are generally resolved in an expedient manner by the maintainers and the developers of the Linux components they effect. However, in recent months, their ability to do so has been put under question, as a result of funding and staffing shortages, leading some to question whether Linux has been a victim of its own success.
Check for Updates
Over the next few days, the majority of Linux distributions will be issuing patches, as will Google for Android. You're advised to regularly check your package manager for updates.
Has this vulnerability made you question whether you should continue to use Linux? Tell me about it in the comments below.
Photo Credits: Crypt (Christian Ditaputratama), PasswordFile (Christiaan Colen)