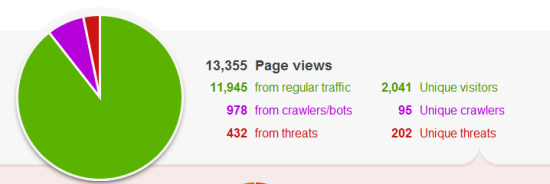
Botnets around the world have turned their attention from sending out spam emails to systematically hacking into Wordpress installs; it's a lucrative business given that Wordpress powers 40% of all blogs. Especially considering that even we fell victim to this, it's about time we did a comprehensive post on exactly how to protect your self-hosted Wordpress install.
Note: this advice only applies to self hosted Wordpress installs. If you use Wordpress.com, you generally don't need to care about security, because they handle it all for you. What's the difference between Wordpress.com and Wordpress.org?
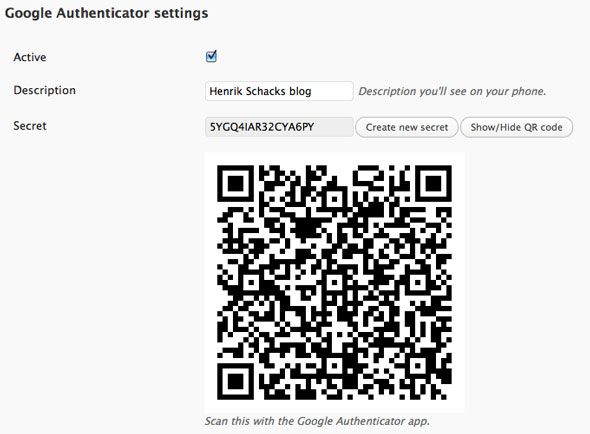
Install Google two-step authenticator
If you already have two-step authentication enabled for your Gmail account or other services, you can use the same authenticator app with this plugin for Wordpress.
Thankfully, you can restrict two-step authentication to only be used on upper level accounts so you needn't annoy all your users.
Login Lockdown
An old plugin, but still working as intended; Login Lockdown checks the IP of login attempts and blocks an IP range for an hour if it fails 3 times within 5 minutes. Simple, effective.
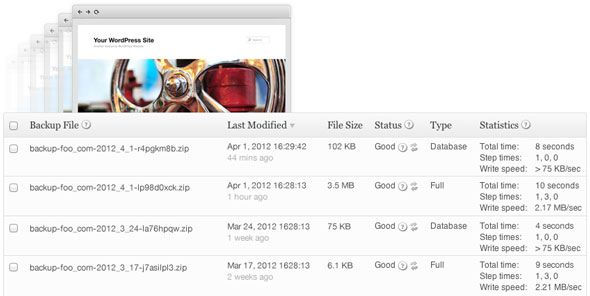
Take Regular Backups
Hackers won't just change one file, but will place their own control panel hidden somewhere and other hidden backdoors - so that even if you fix the original hack, they come right back in and do it all again. Take daily or weekly backups so you can easily restore back to a point where there was no trace of the hacker - and be sure to patch whatever it was they did to get in. Personally, I just invested in a $150 Backup Buddy developer license - it's the easiest and most comprehensive backup solution I've found yet.
Prevent Indexing of Folders
Check the root of your Wordpress installation for the .htaccess file (notice the period at the beginning - you may need to show invisible files to view this), and ensure it has the following line. If not, add it - but make a backup first as this file is pretty crucial.
Options All -Indexes
Stay Updated
Don't make the same mistake as we did: always upgrade Wordpress as soon as an update is available. Sometimes the updates contain minor bug fixes and not security fixes, but get into the habit and you won't have a problem. If you have more than one Wordpress install and can't keep track of them all, check out ManageWp.com, a premium dashboard for all your blogs that includes security scanning.
Not just core Wordpress files, but plugins too: one of the largest Wordpress hacks of the past involved a vulnerability in a common thumbnail generator script called timthumb.php, and there are still themes out there which use the old version. Although plugins were quickly updated, keeping themes up to date is harder, of course - Wordpress won't tell you if your theme is vulnerable, and for that you'll some kind of security scanning plugin - scroll down to the Security Plugins section below for some suggestions.
Never Download Random Themes
Unless you know what you're doing with PHP code, it's very easy to fall into the trap of download a lovely random theme from somewhere, only to find it's got some nasty code in there - most commonly backlinks that you can't remove, but worse can be found. Stick to premium and well-known theme designers (such as Smashing Magazine or WPShower), or for free themes only use the Wordpress theme directory.
Delete Unused Plugins and Themes
The less executable code you have on your server, the better - remove the chance of having old, vulnerable code by deleting themes and plugins you're not using anymore. Disabling them will simply stop their functionality loading with Wordpress, but the code itself may still be executable by a hacker.
Remove Tell-tale Meta In Your Header
By default, Wordpress broadcast its version to the world in the code of your header file - an easy way for hackers to identify older installs. Add the following lines to your theme's functions.php file to remove the Wordpress version, Windows Live Writer info and a line that helps remote clients find your XML-RPC file.
remove_action( 'wp_head', 'wp_generator' ) ;
remove_action( 'wp_head', 'wlwmanifest_link' ) ;
remove_action( 'wp_head', 'rsd_link' ) ;
Remove The "admin" Account
Most brute-force attacks on Wordpress involve repeatedly trying the admin account - the default for all Wordpress installs - and a dictionary of common passwords. If you either login with admin or have the admin account listed in your user table, you're vulnerable to this.
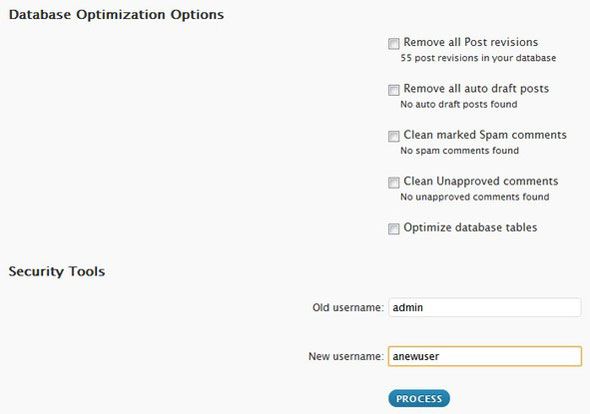
Two ways to fix it: either use wp-optimize plugin - a great plugin that amongst other things, allows you to disable post revisions and perform database optimization - to rename admin account. Or simply create another account with admin privileges, log in as the new user, then delete the "admin" account assign all the posts to your new user.
Secure Passwords
Even if you have disabled the admin account, it may be possible to identify the username of your administrator account - at which point you're vulnerable to a brute force attack again. Enforce a strong password policy of 16 or more random characters consisting of upper and lower case, punctuation and numbers.
Or just use the reallyLongSentenceThatsEasyToRememberMethod.
Disable File Editing Within Wordpress
For those who don't like to login through FTP, Wordpress includes an easy editor in the admin dashboard for theme and plugin PHP files - but that makes your install vulnerable if someone gains access. In fact, this is how someone managed to inject a malware redirection into our header. Add the following line to the bottom of your wp-config.php (in the root folder) to disable all file editing features - and use SFTP to login to your server instead.
define( 'DISALLOW_FILE_EDIT', true );
Hide Login Errors
An incorrect password or wrong username can be identified by the errors given when logging in, which could be used to identify accounts for brute-forcing. This isn't good, obviously, so kill the errors with this addition to your theme's functions.php file
function no_errors_please(){
return 'Nope';
}
add_filter( 'login_errors', 'no_errors_please' );
Activate Cloudflare
As well as speeding up your site, CloudFlare mitigates many known botnets and scanners from even getting to your blog in the first place. Read all about CloudFlare here. Installation is one click if you're hosted at MediaTemple, otherwise you'll need access to the domain control panel to change the nameservers.
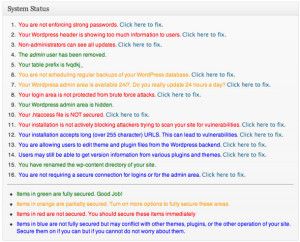
Security Plugins
- Better WP Security implements many of these fixes for you and is the most comprehensive free solution there is.
- WordFence is a premium package that actively scans your files for malware links, redirects, known vulnerabilities etc - and fixes them. Price starts at $18/year for 1 site.
- Login security solution both limits login attempts and enforces secure passwords.
- BulletProof security is a comprehensive but complex plugin that deals with some of the more technical aspects like XSS injection and .htaccess problems. A Pro verison of the plugin is also available which automates much of the process.
I think you'll agree this is quite a comprehensive list of steps to harden Wordpress, but I'm not suggesting you implement all of them. If I had to do all these to every site I ever set up, I'd still be setting them up now. Running any kind of system introduces a risk, and it's ultimately up to you to find the balance between the level of security you want and the effort you want to put in securing it - nothing is ever going to 100% secure. The low hanging fruit here are:
- Keeping Wordpress up to date
- Disabling the admin account
- Adding two-step authentication
- Installing a security plugin
Doing those alone should put you above 99% of all the other blogs out there, which is enough to make potential hackers move on to easier targets.
Do you think I missed anything? Tell me in the comments.