Prism. That's the new buzzword out there for the infringement of your privacy when it comes to cellphones. If you think Verizon is the only carrier that a government has its nose in, I'd suggest that you are a little naive. With the Prism-Verizon scandal, what allegedly has been happening is that the United States of America's National Security Agency (NSA) has been data mining.
That is, they have been going through the call records of Verizon's approximately 99 million users looking for, well, anything! The call records don't include the conversations themselves, but data such as phone numbers dialed, time and date of call, and duration of call. But if I've learned anything from Gene Hackman movies and Wired Magazine, it's that when it looks like the government has a toe over the privacy line, they've really actually driven a white van across it and camped out in your backyard a long, long time ago.
If the thought of the occasionally overzealous government official isn't enough reason to encrypt your smartphone, then all the identity thieves and scammers out there ought to be. Think of how much of your personal information a bad guy could get, if they found your phone. Names, addresses, passwords, account numbers, and goodness knows what else. For a different take on Internet monitoring, check out James Bruce's article, about how Internet monitoring laws will make criminals harder to catch.It's very timely, all of a sudden.
Today, I'm going to show you a few things you can do to make that information a bit more secure.
How to Encrypt Smartphone Data
If you don't at least have a PIN number that you have to enter to access your phone, you really need to do that right now. You can do it with either a PIN, pass phrase, swipe pattern, or even face and voice recognition. Any of these is better than none of these. You may also want to take any lock screen widgets off as well. These can reveal what town you live in, or maybe even what stocks you are following. Go ahead, set it up, I'll be here when you get back.
What can you tell for certain about me from my lock screen now? That Telus is my service provider, so I'm probably in Canada. That's it. Everything else is common information such as the date and time, and temperature. That tip alone could save you from prying questions of overly-observant shoulder surfers. "Say, I see you work in IT too!", "Is that your little girl? What's her name?" Creepy questions, when asked by creepy people.
Encryption is The Key
To really secure your information, you need to use some sort of encryption. By encrypting the data on your phone, even if someone gets past your lock screen, whatever else is on the phone is pretty much useless to them. Unless they have a lot of time and the right skill set, of course.
Whether you have an iPhone, Android, or Windows phone, you should encrypt most, if not all, the data that is on the phone. Let's take a look at how the different phones allow you to encrypt your personal information.
Android Encryption
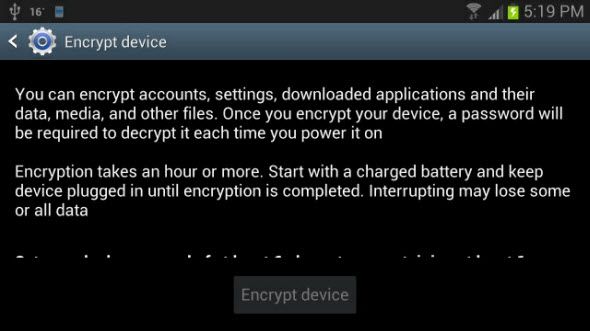
Go into the Settings screen and scroll down until you find the Security tab. Click on that and you'll see a couple encryption choices. To encrypt the entire device, click on Encrypt device. What this will do is encrypt all of your data, and you'll need to enter your password to decrypt it every time you turn your phone on. This process can take quite awhile, somewhere around an hour, depending on how much data you have to encrypt. This process requires a 6 character password with at least 1 number.
It's important that the Galaxy Nexus user manual notes that, "If you already set up a screen lock, you must use the same PIN or password. You can’t have two PINs or passwords." If my permutations math is worth a damn at all that's more than 371,993,326,789,901,217,467,999,448,150,835,200,000,000 permutations. That's a lot. Like, more than a bunch.
Okay, I used a calculator.
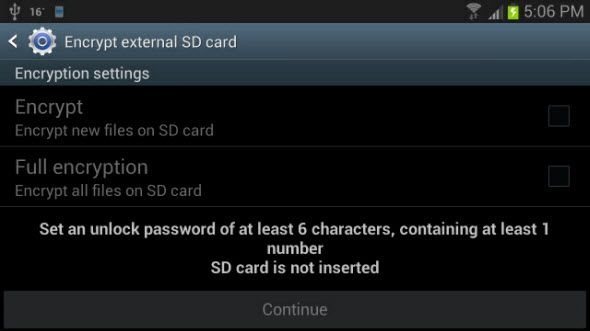
If you are using an external SD card to store sensitive data, you can choose the Encrypt external SD card option on the Security screen. There are some options when encrypting an SD card - you can either encrypt the entire card, or only new files that you are adding to the card from this point in time onward. Again, it uses a password to decrypt the files. Just like the device encryption, it's a 6 character password with at least 1 number.
iPhone Encryption
The process for encrypting the data on your iPhone is absurdly simple, at least in iOS 6.1. All you have to do is set a passcode to access your phone when you turn it on. The catch is that only iMessages, mail messages, and attachments stored on the iPhone and some apps available from the App Store may use the data protection. That's according to the iPhone iOS 6.1 manual. If someone attempts to figure out your passcode, after 10 failed attempts, your encryption key, and therefore your data, is erased provided you've enabled the Erase Data setting in Settings > General > Passcode Lock.
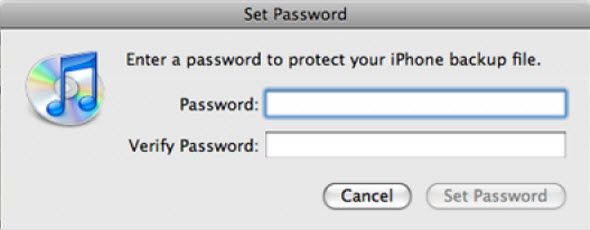
When you back up your iPhone to your computer via the iTunes application, you can encrypt all your phone data that is backed up. This is a good idea as well.
Windows Phone Encryption
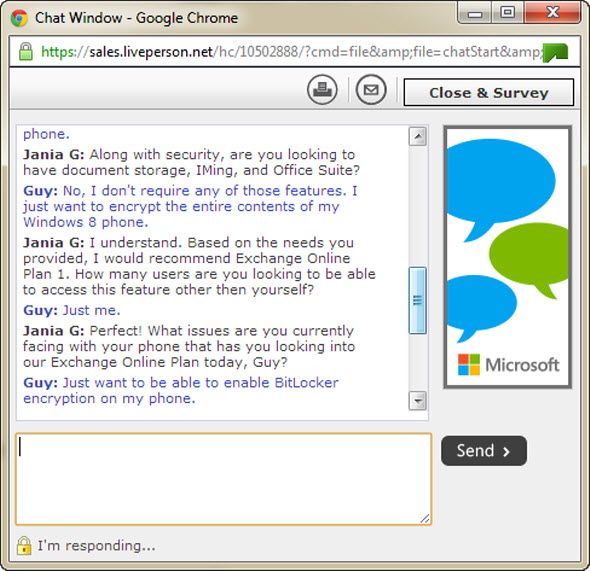
It seems that Microsoft has caused a lot of confusion for Windows 8 phone users, when it comes to encrypting their phones. According to the Windows 8 How-To page, "Other security features, such as device encryption, can be turned on by your employer via a company policy." I haven't priced out Exchange Server lately, but most non-corporate users of a Windows phone are not going to buy it. There also seems to be a lot of confusion about whether the feature can be turned on if you have an Office 365 subscription. I chatted with a Microsoft rep, and their response was that I would need the Exchange Online Plan 1, at $4.99/month.
Even then, if you look at the transcript of the conversation, I don't think they were too sure this would work either.
This is a real shame, since Microsoft is using the BitLocker technology to encrypt the phone's contents. This is a powerful tool indeed! I've covered the basics of how BitLocker works and the degree of security that it gives you. Mind you, there are some Windows Phone 8 apps that will give you some sort of encryption on different file types, although it would be nice to have this functionality native to the phone, like the Android and iPhone. Too bad Microsoft, too bad.
If you're looking for encryption software for your Windows Phone, I've already done the search.
The Take Away
Is the government going to be snooping through the files on your phone? Most likely, no. Should you encrypt the contents of your smartphone anyway? Yes, there are lots of two-legged rats willing to crawl all over your phone for any tidbit that can profit them. Which phone seems to do the best job of encrypting data? I'd have to say that the Android phone does, since it is the only one that natively can encrypt the entire contents of your phone, with the iPhone just behind it, and Windows Phone coming in a distant third. Really distant. More of a no-show, really.
Is your smartphone encrypted? Did you use a third-party application to do it, or just what the phone came with? Has it made it difficult to use your phone at all? Do you think it's necessary to encrypt your phone? Why don't we talk about it, unencrypted of course, in our completely unsecured comments below.
Image Credit: Smartphone with Lock via Shutterstock.