It doesn't matter where in the world you live; there are times when you're going to come across blocked sites and restricted areas of the internet. But if you come across an internet block, don't panic. You need to know how to bypass barred sites and internet restrictions.
Why Do Blocked Sites Exist?
The possible reasons for the blocks are numerous.
Firstly, lots of services use geo-blocking tools to restrict access to their content in certain countries. The issue is perhaps most commonly associated with Netflix's catalog. However, it can also apply to videos on social media (such as sports clips), news articles, and even entire services which are not available outside their country of origin (like Hulu).
Secondly, governments often block access to sites to suit their agenda. The internet restriction in China is perhaps the most famous example, with its Great Firewall being used to block various popular sites, including Twitter, Instagram, and YouTube. But we've also seen Turkey block access to social media in an attempt to quell protests in 2016 and Sri Lanka stop access to Facebook in the aftermath of the April 2019 terrorist attacks, supposedly to prevent the spread of fake news.
Thirdly, employers often block sites on their internal networks to boost productivity and cut out distractions, however frustrating that may be.
Lastly, some countries have odd laws that can restrict access to certain types of material. The UK's controversial porn ban, which required users to verify their age, and Germany's crusade against YouTube are two of the most notable cases.
How to Bypass Blocked Sites
If you run into a restricted site, what can you do? Here are the best ways to bypass blocked sites and access whatever page you want.
1. Use a VPN
The most popular way of accessing blocked internet sites is to use a high-quality paid Virtual Private Network (VPN).
VPNs have many benefits, but when dealing with a blocked site, it's the technology's ability to provide you with an IP address in another country that's the most important. The foreign IP address makes it appear as though you are based in a different location, meaning you won't trigger a site's geo-blocks and can circumnavigate restrictions.
Some services theoretically block access from VPN IP addresses. In practice, this has resulted in a massive game of cat and mouse, in which the VPN providers are generally victorious.
VPNs are incredibly easy to use: download the app onto your phone or computer, enter your login credentials, and choose the network that you want to connect to.
Note that you can use free VPNs, but many of these services have been known to log traffic data or provided subpar protection. It is generally safer to avoid free VPNs and opt for a legitimate and trusted paid service.
Need a VPN? You can score discounted plans with CyberGhost and ExpressVPN if you sign up using these links. Both are reputable, performant, and mindful of your privacy.
2. Use a Smart DNS
The clampdown on VPNs by services like Netflix and BBC iPlayer has resulted in a growth of smart DNS providers. They offer a way to bypass restricted websites.
Smart DNS services have some pros and cons when considered in contrast to VPNs.
One of the most significant advantages of using a smart DNS to get around a website block is internet speed. Unlike VPNs, which route all your web traffic through a different network, smart DNS providers only need to reroute information about your location. This process results in a faster browsing experience.
On the downside, DNS services do not offer any of the same privacy benefits as VPNs. They do not encrypt your traffic, nor do they change your IP. If authorities in your location are likely to prosecute based on the sites you visit, a smart DNS provider is not right for you.
So which DNS should you use? One of the best smart DNS providers is Getflix, so give that a go.
3. Use a Free Proxy
If you need to quickly access a blocked website on a one-time basis, a free proxy might be the way to go.
A proxy will hide your IP address, thus helping to disguise your location. It will not, however, encrypt your traffic. The lack of encryption means proxies are not as secure as VPNs; they are an excellent option to get around blocks on work and school networks, but are not suitable for browsing which requires anonymity.
Proxies are typically much slower than VPNs. You'll also find they often have issues with page formatting and images. Both of these problems preclude them from being reliable long-term solutions. You should also ensure that you're using a legitimate proxy that you can trust.
Learn more about some of the best proxies for geo-blocked content so you can enjoy more international content.
4. Use a Site's IP Address
When you think of web addresses, you probably think of the domain name (e.g. www.makeuseof.com) that you type into your browser's address bar.
In practice, the domain name is like a veneer for the IP address. It's the IP address that points to a server and directs your traffic. DNS servers are responsible for converting domain names into their associated IP addresses.
However, if you know a site's IP address, you can enter it directly into your browser, and you will still end up viewing the site.
Because many networks only block domain name URLs and not their underlying IP addresses, this trick is often a great way to circumvent internet restrictions.
The same principle applies to short URLs. It's unlikely that a small employer or school has blocked all the short URLs that point to a site. You'll often enjoy some success in bypassing school-blocked sites if you try to use them.
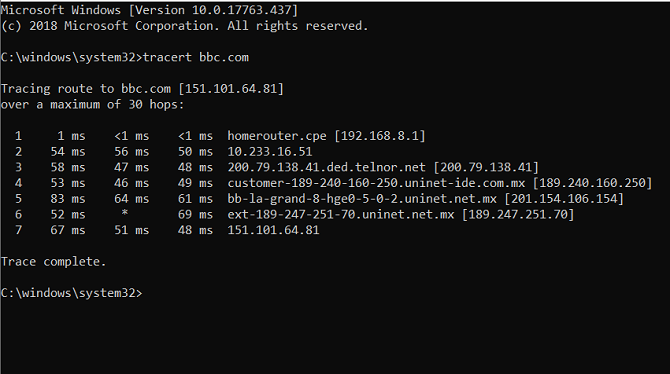
You can find the IP address of a site by opening Command Prompt as an admin, then typing "tracert" followed by the domain name; for example, "tracert bbc.com".
5. Use the Tor Browser
When you use the Tor network to browse the web, your traffic is taken on a long journey through thousands of nodes all around the world. This process makes it almost impossible for a regular website to know where the request originated, so it's unlikely to get caught in any blocking filters. Tor is free to download and is used by over two million people every day (as reported by Enterprise Apps Today).
Be aware that Tor and the dark web are not completely anonymous. Government authorities can, and do, monitor persons of interest on the network. The process is just more complex than it would be via traditional browsers and internet channels.
6. Alternate Between HTTP and HTTPS
Website URLs can come with two different kinds of access: Hypertext Transfer Protocol (HTTP) and Hypertext Transfer Protocol Secure (HTTPS). Switching a site URL from HTTPS to HTTP can make the network you're using think that it is a different site altogether, therefore granting access.
Note that HTTPS is often the preferred access type nowadays, as it securely sends data within networks using encryption. HTTP, on the other hand, does not do this, so you may be putting your data at risk if you choose to use a site using the latter protocol.
How to Bypass School Restrictions
Want to know how to bypass restricted websites at school? First, recognize that there are good reasons educational institutions block content, including for safeguarding purposes. We don't advise you typically access blocked content at school. Nonetheless, sometimes, blocks can be overzealous and ban something that you really need for research.
Some of these options may or may not be available if you want to bypass blocked websites at school. Often, you will not be able to install apps like Tor or a VPN on a school computer or network.
However, there are still some things you can do that will help you get access.
They include using the site's IP address, using Google Translate as an impromptu proxy server, and using a smartphone hotspot as an internet connection.
Just be aware that bypassing a school's restrictions could have repercussions, including expulsion from the establishment.
Learn More About How to Get Past Blocked Sites
Our preferred method for accessing blocked sites and bypassing internet restrictions on a regular basis is to use a VPN.
If you would like to learn more about using VPNs (along with some of the other methods for getting around online blocks), you should learn more about how to bypass Wi-Fi and internet restrictions.