Updated by James Frew on 11/06/2017
No matter your level of experience with computers, you probably have some idea about Wi-Fi security. You'll know that your Wi-Fi network comes with a lengthy password with punctuation and numbers thrown into the mix. You may even have stumbled across the setting to hide your network's name from other people. You've used these tools to your advantage -- confident in the knowledge that your network is on lockdown. Or so you think. Just how secure are some of the common methods?
Hiding your Network SSID
A common misconception is that hiding your Wi-Fi network's name is an effective means of obscuring and securing it from attackers. However, any commonly available Wi-Fi scanning tool will still show your network. The only difference is that instead of your chosen SSID, the network will be shown as hidden. All other details about the network are still broadcast and readily available for anyone that wants them. All this really does is make it harder for your family, friends, or customers to identify and connect to your network.
Instead of using the default Wi-Fi connection settings on their computer, laptop, or mobile device, they will be forced to manually input the network. Not only is this an inconvenience, but can lead to more issues than it solves. Some devices don't play nicely with hidden networks, and it can cause connectivity problems. As the network is no more secure with the SSID hidden, our advice is to not bother hiding your SSID -- the only person it'll cause problems for is yourself.
WEP Passwords
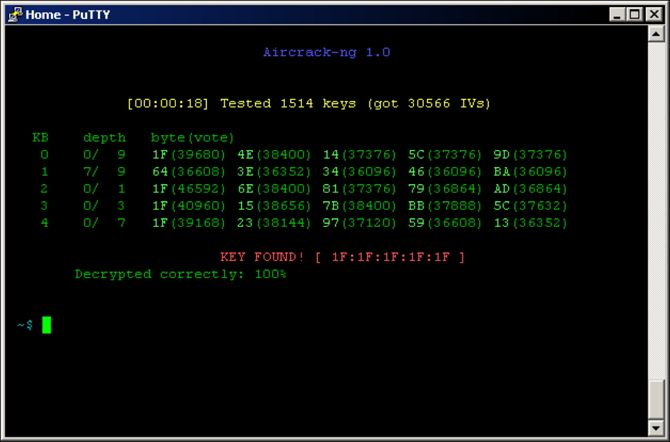
When setting up and security your Wi-Fi network, you have a couple of options. Wired Equivalent Privacy (WEP) is the oldest standard, and is generally accepted to be almost as secure as having no password at all. It was superseded by the much improved (but still flawed) WPA2 in 2006. Even in 2011, it was almost laughably simple to break into WEP networks. In the years since, the tools to crack WEP have become more user friendly, allowing even novice hackers to compromise the network.
While it was once the case that some older devices were incompatible with WPA2, nearly all modern devices have accepted the newer standard. Although most routers still offer WEP as an option, there is never a good reason to use it. If an older device still relies on WEP, then upgrade it rather than allowing that one device to compromise your network. Stay away from public Wi-Fi networks that use WEP too -- they are easy targets for hackers. Public Wi-Fi networks are often easily compromised and used to listen in on your web traffic. This results in the hacker obtaining your passwords, payment information, and even bank login details. Give WEP secured public networks a wide-berth, even if you are using a VPN.
WPA & WPS
You might think that your 25 character WPA2-PSK password is the best security available. That may be true, but it doesn't mean you are fully protected. In an attempt to simplify the connection process, many routers use WPS technology. Wi-Fi Protected Setup (WPS) comes in the form of a one-touch button, or as a simple eight digit number printed on your router. The eight digit number bypasses the need for a complex alphanumeric password. Replacing a long, complex password with a short numeric one sounds like the exact opposite of good security advice. The manufacturers are aware of this, so to prevent brute force hacking, there is a 60 second cooldown after three failed attempts. To randomly attack an eight digit password like this would take 6.3 years. You’d probably notice if someone was parked outside for that long.
Unfortunately, they did make a slight oversight -- they split the passkey number in 2 sets of 4 digits. After cracking the first four digits, the router sends a helpful confirmation that set was correct. The hacker can then save those four for reference. This means that instead of eight digits, you only need to crack four numbers twice. The 6.3 year calculation time is now reduced to just less than a day.
To make matters worse, some manufacturers don't even implement the cooldown period between failed attempts. This means that with the right tool, even your WPA2 network can be cracked in just a few hours. Since WPS is a requirement for all Wi-Fi routers, and enabled by default, your router is almost certainly at risk. To protect yourself, head into your router's settings and disable WPS completely. Be sure to rerun your tests after disabling this -- some routers have a separate internal WPS pin that cannot be disabled.
How Secure Is Your Wi-Fi?
The unfortunate reality is that no matter how many precautions you take, the chances of your Wi-Fi network being completely secure are exceedingly low. Given enough motivation and time, even the most secure networks will eventually give in to a hacker's efforts. The most effective method of preventing wireless attacks is to disable Wi-Fi altogether. However, with so many wireless devices dotted about our homes, this might not be practical.
Instead, if you are using a router provided by your ISP, switch it to modem mode, and use another router for the Wi-Fi network. As always, make sure that all your devices are up to date, and your router is running the latest firmware. If you want to take things one step further, you could replace the default firmware with an alternative like Tomato or DD-WRT.
How many of these vulnerabilities did you know? Have you taken steps to secure yourself? Is there anything you think we missed? Let us know in the comments below!