Malware is usually very specific in what it does to your PC, whether that's displaying ads, taking over your browser homepage and search bar, or nagging you to pay for some fake anti-virus. Hijacking however is potentially far more devastating, giving the hacker backdoor remote access to your entire PC.
This is the holy grail for how hackers hack, so it's important to understand how it can occur and what you can do to protect yourself.
Social Engineering
This is the most common attack method, and we've given a full account of one such process before, involving a scam technical support call that goes something like this:
- "Hi, I'm from the security team at Microsoft and we've detected a virus warning from your Windows PC"
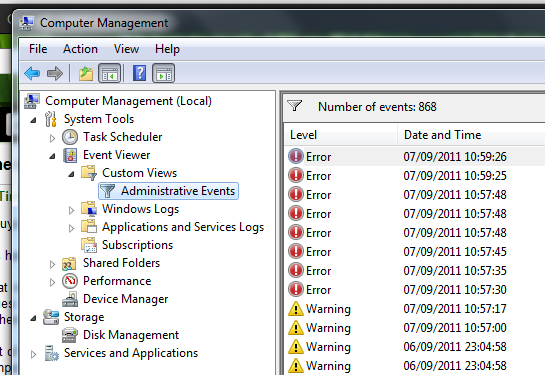
- They instruct you to open the event viewer, where there are lots of warning messages awaiting you, proving there must be something wrong!
- They offer to fix it for you, you just need to go to this remote support site and download the remote control software.
- They gain control of your PC, and proceed to do meaningless fixes, like opening file property dialogs.
- The login details are passed onto a criminal network who now have full access to your PC anytime they wish, and a tidy commission is paid to the guy who made the call.
The fake technical support scam isn't the only way this can occur of course - if you leave your computer in the hands of someone you can't completely trust, there's always a chance backdoor software could be installed. Although there's no cases recorded, a Best Buy employee was found stealing raunchy pictures from a user's PC - so there's nothing to stop rogue repair technicians installing trojan software either.
While rogue technicians are certainly rare - the fake technical support scam is all too prevalent, and I've personally had to deal with the aftermath on family machines where they've fallen for it. The key to protecting yourself and your family is education - explain to less technically capable friends and family that these support calls are fake and they should simply hang up.
For single user computers, it's also quite likely they're using the administrator account by default. The safest thing to do would be to set up a restricted user account for them to use on a daily basis, and ask them to never use the administrator account without talking to you first.
Also, note that while Microsoft will never call you personally, they do sometimes contact home users - but only via their ISP so that they can confirm they are an existing customer, and charges will never be made. This happened recently in 2010, when Microsoft set about cleaning 6.5 million computers of the botnet they were a part of.
Browser Vulnerabilities - Flash & Java
Modern browsers are themselves rather secure. Chrome and more recently others run website tabs in their own sandboxed environment, where no changes can be made to the local filesystem. However, plugins such as Java operate outside of this sandbox, so these remain a concern.
If these plugins are enabled and not blocked by the browser, malicious Java or Flash code can be run as soon as you visit an infected site, or even loaded through the untrusted ad-network of a trusted site.
Thankfully, most of these problems are mitigated by simply :
- running the latest version of a browser.
- keeping up to date.
- enabling "click to play" (so code doesn't run automatically).
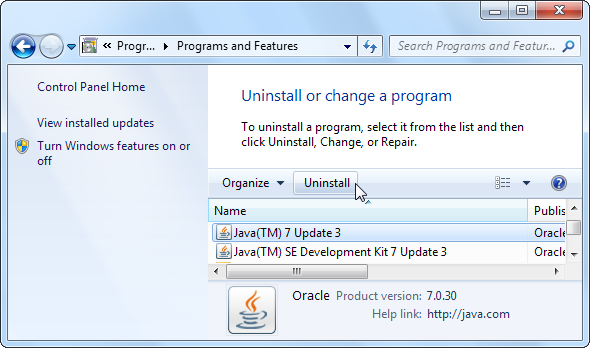
- uninstalling the Java plugin completely.
Really, no decent website uses Java anymore (note: Java and Javascript are completely different), and the average home user does not run Java applications.
Chris has explained the problem of browser plugin security before, so I'll point you there for ways of either disabling or checking your particular browser and setup.
Port Scanning
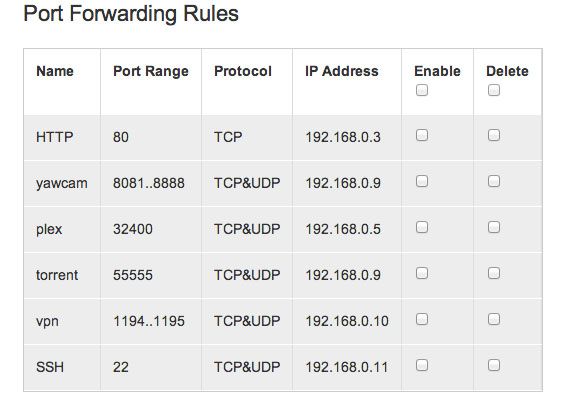
I'm listing this last as it's the least likely to affect home computers that are connected via a router. If you've read our explanation of what port forwarding is, you'll understand that any application that needs to receive information over the network is required to open a port. Sometimes these are predetermined - such as a web server on port 80 - and other times they're just random. By default, unused ports are closed, so that's where the difficulties around port forwarding arise.
If you want to run a web server from your home PC, you'll need to configure the router specifically to take incoming traffic for port 80 and forward it to your PC. Some applications and devices use uPnP, which handles this configuration of opening ports as and when required. If you have an Xbox 360 for instance and regularly play online, it's using this to configure ports dynamically.
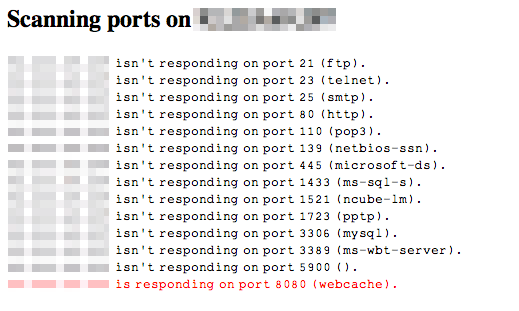
Port mapping involves a hacker scanning your router from the outside and systematically talking to every single port number, looking for open services. Once the services are found, the hacker is able to check certain characteristics that identify the version of software being run ("software footprints"). The version is then cross-checked against a database of known vulnerabilities, and if a match is found they can proceed with the exploit. Although this sounds laborious, in practice it's a single tool to scan, cross-check and deliver the exploit.
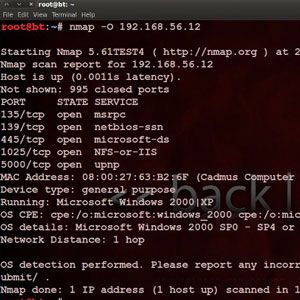
Unless you're doing things like setting up your own network servers and performing manual port forwarding, it's unlikely you're vulnerable to simple port scanning. However, if you're curious about what ports are open on your home network, there's a quick Internet-based tool available here, though you're limited to the standard ports and 500 others. If you run Linux, check out the nmap tool for a more full test.
The exception to being protected by a router is when you're connected to public Wifi. You're placed on the same network as everyone else, and any one of them could be running a port scanner looking for vulnerable services.
Finally, Matt wrote a great PDF guide - HackerProof, Your Guide to PC Security - which should be considered essential reading on the topic.
Have you ever had your computer hijacked, and if so, what happened? Do you know how they got in?