There's great news for anyone affected by the CrypBoss, HydraCrypt, and UmbreCrypt ransomware. Fabian Wosar, a researcher at Emsisoft, has managed to reverse-engineer them, and in the process has released a program that is able to decrypt files that would otherwise be lost.
These three malware programs are very similar. Here's what you need to know about them, and how you can get your files back.
Meeting The CrypBoss Family
Malware creation has always been a billion dollar cottage industry. Ill-intentioned software developers write novel malware programs, and auction them to organized criminals in the dingiest reaches of the dark web.
These criminals then distribute them far and wide, in the process infecting thousands of machines, and making an ungodly amount of money.
It seems that's what's happened here.
Both HydraCrypt and UmbreCrypt are lightly-modified variants of another malware program called CrypBoss. In addition to having a shared ancestry, they're also distributed through the Angler Exploit Kit, which uses the method of drive-by downloads to infect victims. Dann Albright has written extensively about exploit kits in the past.
There's been a lot of research into the CrypBoss family by some of the biggest names in computer security research. The source code to CrypBoss was leaked last year on PasteBin, and was almost immediately devoured by the security community. Late last week, McAfee published one of the best analyses of HydraCrypt, which explained how it works at its lowest levels.
The Differences Between HydraCrypt and UmbreCrypt
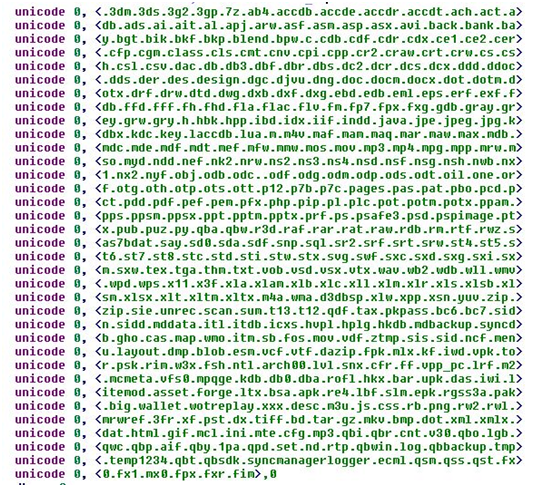
In terms of their essential functionality, HydraCrypt and UmbreCrypt both do the same thing. When they first infect a system, they start encrypting files based upon their file extension, using a strong form of asymmetric encryption.
They also have other non-core behaviors that are pretty common within ransomware software.
For example, both allow the attacker to upload and execute additional software to the infected machine. Both delete the shadow copies of the encrypted files, making it impossible to restore them.
Perhaps the biggest difference between the two programs is the way in which they "ransom" the files back.
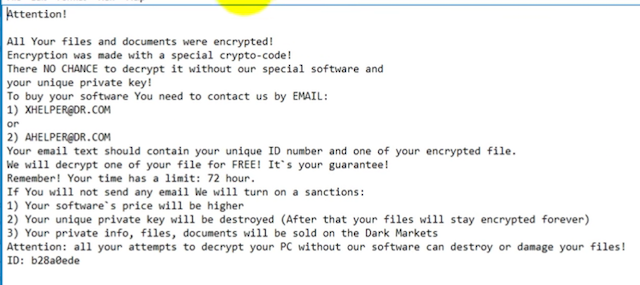
UmbreCrypt is very matter-of-fact. It tells the victims that they've been infected, and there's no chance they'll get their files back without co-operating. For the victim to start the decryption process, they need to send an email to one of two addresses. These are hosted on "engineer.com" and "consultant.com" respectively.
Shortly after, someone from UmbreCrypt will respond with payment information. The ransomware notice doesn't tell the victim how much they're going to pay, although it does tell the victim that the fee will be multiplied if they don't pay within 72 hours.
Hilariously, the instructions provided by UmbreCrypt tell the victim not to email them with "threats and rudeness". They even provide a sample email format for victims to use.
HydraCrypt differs slightly in the way that their ransom note is far more threatening.
They say that unless the victim doesn't pay up in 72 hours, they'll issue a sanction. This can be an increase in ransom, or the destruction of the private key, thereby making it impossible to decrypt the files.
They also threaten to release the private information, files and documents of non-payers on the Dark web. This makes it a bit of a rarity amongst ransomware, as it has a consequence that is far worse than not getting your files back.
How To Get Your Files Back
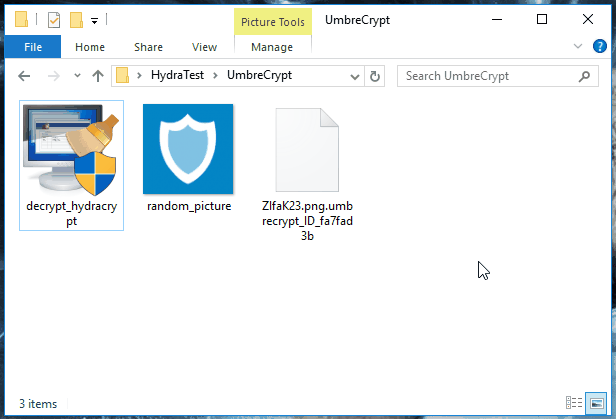
Like we mentioned earlier, Emisoft's Fabian Wosar has been able to break the encryption used, and has released a tool to get your files back, called DecryptHydraCrypt.
For it to work, you need to have two files on hand. These should be any encrypted file, plus an unencrypted copy of that file. If you've got a document on your hard-drive that you backed up to Google Drive or your email account, use this.
Alternatively, if you don't have this, just look for an encrypted PNG file, and use any other random PNG file that you either create yourself, or download from the Internet.
Then, drag and drop them into the decryption app. It'll then kick into action, and start trying to determine the private key.
You should be warned that this won't be instantaneous. The decryptor will be doing some pretty complicated math to work out your decryption key, and this process could potentially take several days, depending on your CPU.
Once it's worked out the decryption key, it'll open up a window and allow you to select the folders whose contents you want to decrypt. This works recursively, so if you've got a folder in a folder, you'll only need to select the root folder.
It's worth noting that HydraCrypt and UmbreCrypt have a flaw, wherein the final 15 bytes of each encrypted file are damaged irretrievably.
This shouldn't trouble you too much, as these bytes are usually used for padding or non-essential metadata. Fluff, basically. But if you can't open your decrypted files, try opening them with a file restore tool.
No Luck?
There's a chance that this won't work for you. That could be for an number of reasons. The most likely is that you're trying to run it on a ransomware program that isn't HydraCrypt, CrypBoss, or UmbraCrypt.
Another possibility is that the makers of the malware modified it to use a different encryption algorithm.
At this point, you've got a couple of options.
The quickest and most promising bet is to pay the ransom. This varies quite a bit, but generally hovers around the $300 mark, and will see your files restored in a few hours.
It should go without saying that you're dealing with organized criminals, so there's no guarantees they'll actually decrypt the files, and if you're not happy, you've got no chance of getting a refund.
You should also consider the the argument that paying these ransoms perpetuates the spread of ransomware, and continues to make it financially lucrative for the developers to write ransomware programs.
The second option is to wait in the hope that somebody will release a decryption tool for the malware that you've been stricken with. This happened with CryptoLocker, when the private keys were leaked from a command-and-control server. Here, the decryption program was the result of leaked source code.
There's no guarantee for this though. Quite often, there's no technological solution to getting your files back without paying a ransom.
Prevention is Better Than A Cure
Of course, the most effective way of dealing with ransomware programs is to ensure you're not infected in the first place. By taking some simple precautions, like running a fully updated antivirus, and not downloading files from suspect places, you can mitigate your chances of getting infected.
Were you affected by HydraCrypt or UmbreCrypt? Have you managed to get your files back? Let me know in the comments below.
Image Credits: Using a laptop, finger on touchpad and keyboard (Scyther5 via ShutterStock), Bitcoin on Keyboard (AztekPhoto via ShutterStock)