We've talked plenty about passwords, especially how to create an unbreakable one, but have you ever wondered how websites keep these passwords safe from malicious folk? After all, only the worst websites actually store passwords in plain text.
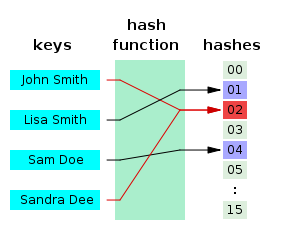
They do it using a process called hashing, which takes a series of characters and transforms it into something completely different. This is really easy to do in one direction, but trying to reverse it is next to impossible.
Confused? That's okay. It'll become clear in a few seconds.
For example, you might have a password examplepass, but websites don't literally store "examplepass" in their databases. Rather, they run it through a hash function that transform it into a different series of characters, such as 6XF$#14Az@Q, and this is what they store.
So if someone broke into the databases of Facebook or YouTube, they would have a hard time cracking your password. Even though examplepass hashes into 6XF$#14Az@Q, it doesn't work the other way around.
So, when you type your password into Facebook, the website doesn't say "The user typed examplepass. Is this their password?" because that would be horribly insecure. Instead, the website hashes your password and checks it against its database of hashed passwords.
If it matches hash with hash, then it determines that you entered the right password.
This explains why "Forgot Password" links behave as they do. Websites can't just email you your password because they don't know what it is! Instead, they reset your password with a temporary one or ask you to set a new one so that they can update the record they have for you.
If you ever get an email with your password in plain text, the sender's site is insecure and you should seriously reconsider dealing with them. Anyone keeping your password in plain text is just asking for trouble. Check out Plain Text Offenders for examples of this.
Did you know how passwords are stored? Have you ever been emailed a password? Let us know your experience below!
Image Credit: Maxx-Studio via Shutterstock.com