By now you've probably heard the phrase "another day, another hack" more times that you'd want to in a lifetime, but its time to add another to the list as its emerged that a staggering 68 million Dropbox accounts have potentially been compromised.
You may remember back in 2012, there was speculation that Dropbox had been hacked. At the time Dropbox denied that anything other than a "project document with user email addresses" had been taken.
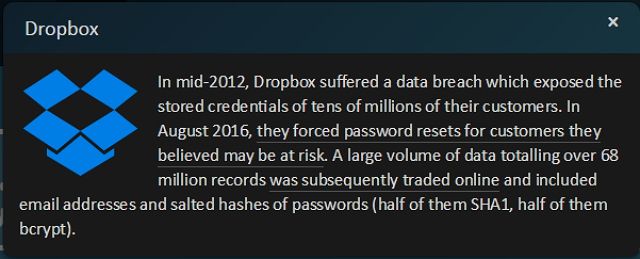
As of August 2016 it was confirmed that over 68 million user accounts on Dropbox that had been created prior to mid-2012 have apparently been leaked online with their associated passwords.
At the time of writing it still isn't clear how or why the leaked information has taken four years to appear but now that it has, Dropbox has taken the precautionary step of emailing the accounts they believe to be affected and prompting a password reset.
What We Know
In 2012, Dropbox announced that some user data had been stolen as a result of an employee reusing a password on an internal system that they had previously used on LinkedIn -- which itself was subject to a data breach in 2012.
At the time Dropbox said that the hacker had only accessed a project document containing customer email addresses. This led to a large volume of spam directed at Dropbox users and, as a result, for Dropbox to investigate and add additional security features.
All went quiet on the Dropbox leak until mid-August 2016, when Dropbox began sending out emails stating that customers who hadn't changed their passwords since mid-2012 would be prompted to on their next login. However, there was no explicit mention of a hack or leak and Dropbox didn't report the number of users they had sent this email to.
Not long after these emails were sent out, Motherboard was given approximately 5GB of data which appeared to contain the email addresses and encrypted passwords of almost 69 million Dropbox users. Back in 2012 when the hack took place, Dropbox had just reached 100 million users so this leak represents more than two thirds of their user base at the time.
Troy Hunt, founder of the website Have I Been Pwned (HIBP), confirmed the legitimacy of the hack by finding both his and his wife's credentials in the data. He then proceeded to notify the 114,136 HIBP subscribers who had been affected by the leak.
Dropbox released a statement confirming that the data contained in the leak was from the 2012 breach, and that the password resets "protect[ed] all impacted users...The reset only affect[ed] users who signed up for Dropbox prior to mid-2012 and hadn't changed their password since." They also commented that the actions they took "protected all affected accounts and [their] intelligence showed that this was in the 60+ million range."
After contacting Dropbox to verify the scope of the breach we were informed that "[they] have no evidence of any improper access to those accounts" which is some reassurance to affected users.
The Hack -- How Bad Is It?
Any data breach is bad news and potentially releasing users' email addresses and passwords onto the internet is terrible in its own right.
However, one glimmer of hope in the Dropbox hack comes from their encryption of passwords. Despite their apparently lax internal password security at the time of the hack, Dropbox had actually begun to take steps to enhance their password security by encrypting all data with bcrypt, one of the most secure hashing algorithms.
However, note that only (approximately) half of the passwords were moved to bcrypt at the time of the hack, with the other 34 million encrypted using SHA-1, a less secure encryption method. All isn't lost for those passwords either, as Dropbox had salted the SHA-1 passwords, adding a random string of text to make the passwords harder to decrypt.
This protection may prevent any nefarious types from being able to decrypt the passwords, but this shouldn't be taken for certain, and you should definitely take steps to protect yourself from the hack, and to do a check up on your own security to keep your online self safe in the future.
Change Your Dropbox Password
Although Dropbox has already performed the password resets for the affected accounts, resetting your password is a worthwhile exercise, especially if you haven't changed passwords in a while.
Dropbox Account Security
There are some security settings in Dropbox which can help you protect your account. Two-factor authentication (2FA) can be enabled in your account settings. Once you have entered your phone number, Dropbox will then send you a time-limited, unique code via SMS that you will be required to enter when you try to login.
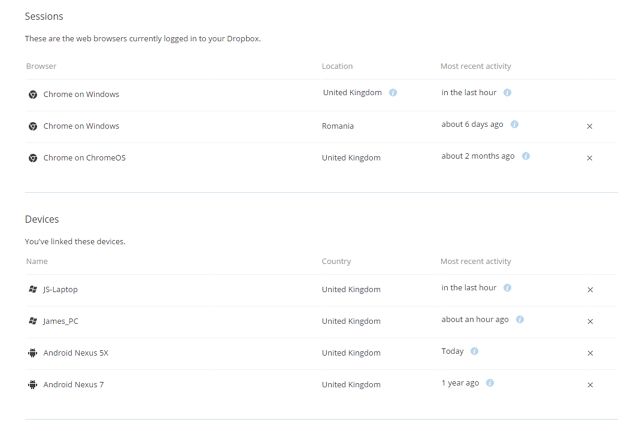
You can also see which devices have been authorised to access your account, either through the Dropbox mobile or desktop app. Sessions will display which browsers are logged into your Dropbox account.
If you don't recognize any of the sessions or devices you can click the x on the right hand side to delete them and remove access from your account. If you want to be thorough, even if you don't notice anything suspicious you can remove all the sessions and devices and simply log back into the apps on the devices you use.
Enable 2FA Everywhere
Most major sites have support for two-factor authentication and it is one of the best ways to protect yourself in the event of a hack. Without access to you or your phone, the hacker will not be able to login to your account.
If you aren't sure if a website you use supports two-factor authentication, you can check using Two Factor Auth, which maintains a database of all supported sites.
Change Any Reused Passwords
One of the main reasons that password leaks are such bad news is that many people will often recycle passwords between sites.
Dropbox even acknowledges this problem, stating "while Dropbox accounts are protected, affected users who may have reused their password on other sites should take steps to protect themselves on those sites."
After enabling 2FA, the best preventive action you can take is making sure you use a unique, strong password on every site. That includes going through and making sure that you didn't reuse your Dropbox password on any other accounts.
Use a Password Manager
One of the main reasons that we reuse passwords is because it can often be too overwhelming to remember them all. Luckily, password managers have come to the scene to help you manage your long password list.
While each password manager differs slightly, they all will store your passwords, with some offering additional features like secure password generation and the ability to change your passwords automatically.
Lastpass Security Challenge
LastPass is one of the leading password managers and has a Security Challenge tool. If you import your data into LastPass, it will analyse all your passwords, and rate them on their strength and alert you if the account was involved in a leak, or if you have used the same password on other sites. You can then change any weak or affected passwords from the Scorecard page.
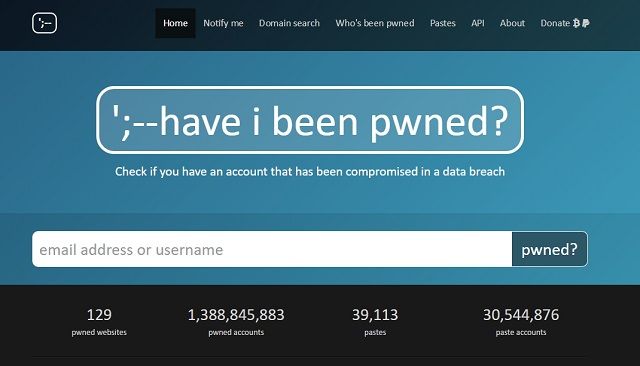
HaveIBeenPwnd
We mentioned that Troy Hunt, founder of Have I Been Pwnd was one of the first to confirm the Dropbox leak by verifying his and his wife's details in the data. He then sent emails to all affected subscribers of HIBP.
It costs nothing to subscribe, and all you need to do is enter your email address and if Hunt ever gets data that your account has been featured in a leak, then the HIBP service will send you an email alerting you. There is no downside to this service, and is one of the best ways to stay on top of any new leaks.
Dropbox Isn't the First...And It Won't Be the Last
Hacks, data breaches, and password leaks have become part of the course of digital life in 2016. There have been high profile hacks of sites like LinkedIn and the infamous Ashley Madison along with countless more.
The best advice is to make sure you take proactive steps to secure your accounts and digital identity, so that when the inevitable happens and another site is hacked and passwords exposed, you have the best protection available.
Image Credit: Raxpixel.com via Shutterstock, welcomia via Shutterstock.com