It is difficult to put an accurate figure on the impact of malvertising. At their peak between 2014-2016, malvertising campaigns lead security research firms to report millions of malicious advertisements across the web.
Whether the rate of malvertising incidents has risen or not, one thing is clear. Malvertising can do a lot of damage to an unsuspecting user. With the low entry level to malvertising, the threat remains active.
This guide which will help you understand what malvertising is, why it's so popular, where it's hiding, and what you can do about it.
What Is Malvertising?
"Malvertising" is a portmanteau of "malicious advertising." In short, malvertising is the practice of using online ads to infect computers with various types of malware.
A malvertising attack (also known as a drive-by malware attack) can work in a variety of methods. However, there are two common techniques:
- Pre-click: A malvertising campaign that uses a special script that automatically downloads as soon as the ad loads. The user doesn't have to click anything; visiting the page containing the ad is enough. This allows an attacker to place malvertising in a landing page, or set up a malvertisement redirect chain to bounce users through several malicious pages.
- Post-click: As it sounds; the user downloads the malware after clicking the malicious ad. Attackers still use malvertising redirects to keep users moving through numerous pages.
Malvertising can carry all kinds of malware types. It can be anything from adware to ransomware, to a piece of code that changes settings on your router. Exploit kits are a common malvertising payload. If successful, an exploit kit can open your system up to other malware types. Botnets, banking Trojans, and cryptojackers are also on the malvertising menu.
How Big a Threat Is Malvertising?
Judging the scale of malvertising can be hard. It is silent, and doesn't come with the other common red-flags we train ourselves to spot. Vadim Kotov, Senior Security Researcher at Bromium, echoes this:
"The continued rise of malvertising is also of note, as it became so rapid and high-impact, largely due to its attacks on high-profile websites. Drilling down further, this year alone, there were malvertising attacks on more than a quarter of the Alexa 1,000. This class of attacks is fascinating as it represents a perfect symbiotic relationship between two discrete technologies that end up producing such detrimental effects."
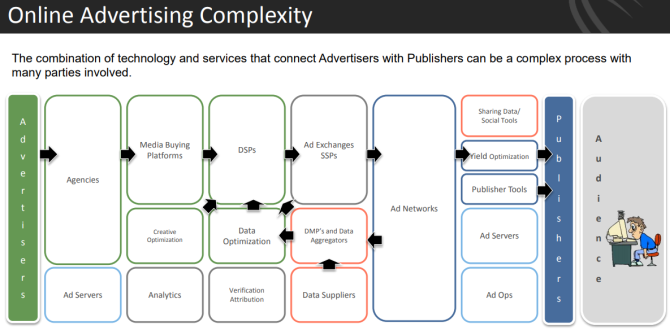
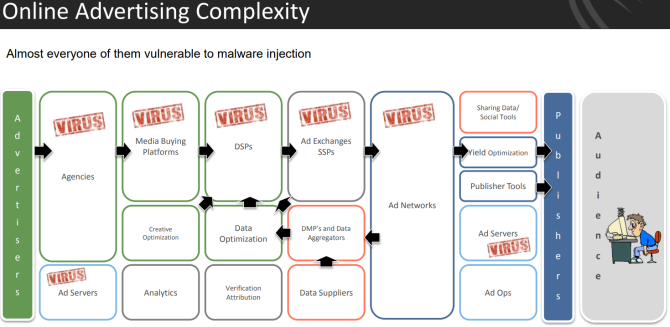
The main reason is that advertising is everywhere. Third-party-ad networks sell adverts to big sites like eBay, The Weather Channel, Rotten Tomatoes, and MakeUseOf.
Those sites display the ads in good faith. But if a malvertiser figures out how to insert a malicious ad into a legitimate ad network, there's a chance it will appear on high-ranking websites before its caught.
Ad Networks Used as Malware Distribution Networks
The networks serving advertisements throughout the internet are largely automated, with only peripheral human involvement. This means attackers can take a chance. If successful, their infected ad will sneak through the security systems of an internet advertisement network. Even highly trusted ad networks, like Google's DoubleClick, have distributed malicious ads.
The automation means a majority of websites are unaware of precisely what will be displayed on their site, removing themselves from the selection process---and further distancing themselves from potentially malicious content.
One tactic for malvertisers to get their ads into trusted networks is by buying ad space for benign ads first. Once a reputation as a legitimate advertiser is established, the malware-laden ads begin. Because they're under less scrutiny than new advertisers, they have a brief opportunity to slip these malvertisements onto websites.
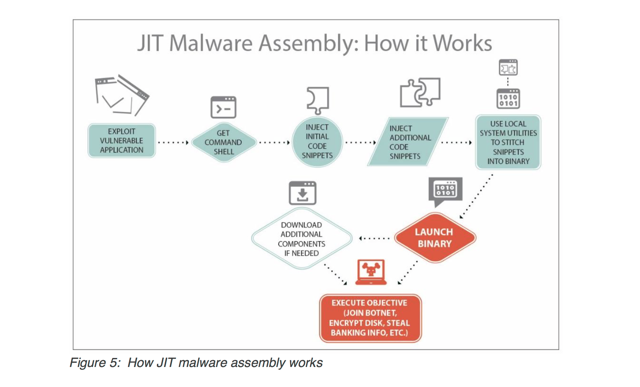
Just-In-Time Malware Assembly
A newer method of getting malvertisements published is just-in-time malware assembly. This includes innocent-looking components of code in the ads that are downloaded separately to a victim's computer. They're then assembled and compiled into the malware payload.
This payload can then run or download additional components to complete the assembly. This is especially difficult to detect.
Malvertising Threat on Mobile
Malvertising is a particular threat to mobile users. How many times have you accidentally tapped an advert on a website while scrolling through? Or clicked an advert in a game as you try to speed through cooldown timers or lockout screens?
A malicious ad doesn't differentiate between a "proper" click and an accidental click. Smartphone design doesn't help, either. The screen is great for scrolling, but precise clicking is a different proposition.
Another smartphone issue is a lack of security programs. Many users simply don't consider their smartphone security in the same manner as a desktop or laptop.
Where Does Malvertising Come From?
Common sense tells us to avoid the sketchier side of the internet. Think about the sites you'd normally consider to host malware or be privy to a malvertising campaign:
- Pornographic sites
- Sites offering other NSFW/NSFL content
- Sites offering free software/cracks/keygens/warez
- Sites offering Flash games
- Illegal streaming sites
- Torrent sites
- Sites using "unreliable" TLDs, hosted in "questionable" countries
- Sites offering coupons, savings, and questionnaires
- Online dating sites
- Betting sites
Unfortunately, you can find malvertising absolutely anywhere. Because of how third-party ad networks operate, infected ads can be spread to a wide variety of otherwise very trustworthy sites at high speed. While there are sites that are more likely than others to infect you with malware, you can be hit at any time with one of these ads.
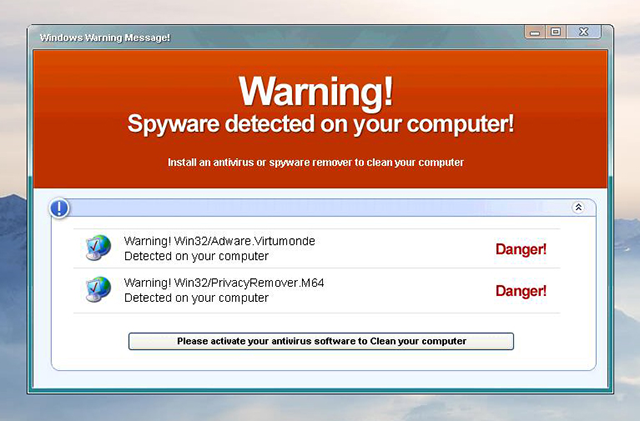
Malvertising is a stealthy delivery method, too. However, RiskIQ's research showed that in 2015, the most common form of malvertising was through fake software updates, especially for Adobe's Flash plugin. They can also be spread through fake virus and malware warnings, though the prevalence of that particular method has decreased.
Note: The alert above looks legit, doesn't it? Learn more about how to spot fake virus and malware warnings so you're never caught off guard or tricked.
Tracking Malvertising Campaigns
Back in March 2015, Malwarebytes announced it had tracked a particular campaign as it dynamically traversed various internet outlets, culminating in malicious advertisements seen on:
- MSN.com: 1.3 billion monthly visits
- NYTimes.com: 313.1 million
- BBC.co.uk: 290.6 million
- AOL.com: 218.6 million
- my.xfinity.com: 102.8 million
- NFL.com: 60.7 million
- realtor.com: 51.1 million
- theweathernetwork.com: 43 million
- thehill.com: 31.4 million
- newsweek.com: 9.9 million
The injected malicious ads were designed to deliver the Angler exploit kit. This is known to search for and exploit vulnerabilities in HTML, Silverlight, Flash, JavaScript, Java, and plenty more. Once the Angler EK is installed, it installs a variant of commonly seen ransomware TeslaCrypt or AlphaCrypt. With the potential to infect literally billions of users, the malvertising stakes are constantly rising.
How to Protect Yourself Against Malvertising
It looks like a mammoth task. The malvertisements are seemingly everywhere, but there are a few precautionary steps you can take:
- Disable Flash and Silverlight. Both are frequent targets for attackers, both frequently contain security vulnerabilities.
- Use script management add-ons. As most ads and scripts are automatically implemented, you can use a script blocking browser extension to control your web content.
- Use and update your antivirus. This will catch more issues than it misses.
- Consider upgrading. Malwarebytes Premium is a worthwhile investment alongside a free antivirus suite. I use Windows Defender and Malwarebytes Premium for a more secure system.
Until there is a monumental shift in how the internet is funded, ads will continue to be served as part of our day-to-day browsing. Massive ad-networks aren't going to disappear unless there is a viable alternative, inclusive of those existing advertising behemoths. They certainly won't want to relinquish their profits.
And while each of the major ad-networks will be actively addressing the malvertising menace, there is still a major emphasis on self-protection.
Want a browser that features auto-script blocking and cares about your privacy? Check out Brave, a browser that takes your privacy seriously.