Encrypting files and emails is essential if you don't want your secrets and private information to be seen by people who have no business looking at them. Fortunately, GNOME comes with Seahorse—an easy-to-use tool that makes encryption simple.
Why Use Encryption With Ubuntu?
Everyone has secrets. This might be the journal you want to keep hidden from your siblings, or it might be state secrets—that would be compromised if you left your laptop on public transport.
The files you want to encrypt might not be quite so dramatic. Most people keep scanned copies of important documents on their computers: driving licenses, birth certificates, passports, and insurance certificates. These are items you may need to have on hand in a hurry but are also documents that are attractive to criminals and can lead to identity theft.
You might also use your PC to generate invoices for clients or have other confidential data, with a legal obligation to keep it secure from attack. You might also need to securely send or receive files over email, or publish them in encrypted form on the open internet.
In these cases, you'll need an encryption solution that is fast, easy to use, and hard to break.
Seahorse is a GUI for GNU Privacy Guard (GPG), that uses PGP to encrypt data.
How Does PGP Work?
PGP stands for Pretty Good Privacy and is one of the most common encryption types. It works by generating a set of two keys. Anyone with access to a published public key and an appropriate encryption program can encrypt messages, but they can only be decrypted by an individual with a private key.
You might want to publish your public key on your website, social media profile, or in your email signature, in case anyone wants to send you a completely private message or file that can't be decrypted by would-be snoopers.
Create PGP Keys With Seahorse
On Ubuntu, Seahorse is called Passwords and Keys. You can find it if you click on the system menu, and start to type either Seahorse or Passwords. Unlock your keyring by clicking the green Unlock button, and enter your user password when prompted.
If you haven't yet used Seahorse, you'll see a message stating that This collection seems to be empty.
As encryption relies on encryption keys, the first thing you need to do is create some. Click the green Add new items button. Alternatively, you can click the + icon in the top left of the app.
Seahorse can handle multiple types of keys including Secure Shell (SSH) keys, individual passwords, additional keyrings, and more.
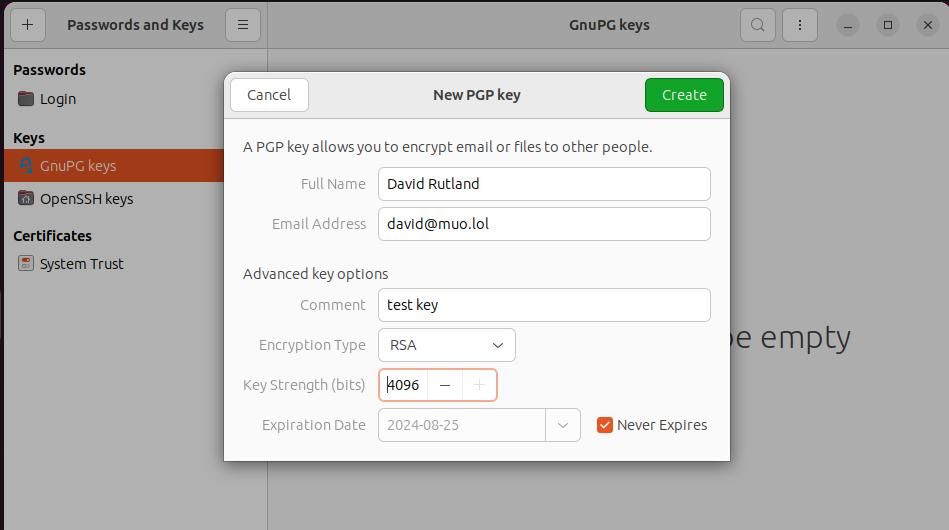
For now, you should click on the GPG key. The window that appears bears the title New PGP Key. This isn't an error or a typo, as GNU Privacy Guard is a tool that you can use to encrypt information, and which implements OpenPGP.
You'll need to enter your name and email address. You can add a comment to the key, and specify the encryption type, as well as the key length, and whether the key will expire.
RSA (Rivest–Shamir–Adleman) is a solid choice, and a 2048-bit key should withstand most cracking attempts for the next few decades. If you believe this isn't enough, feel free to raise the value to 4096-bit instead.
When you're happy with your choices, press Create, then when prompted, twice enter a passphrase for your new key.
Seahorse uses random data when generating a key, and the more you interact with Ubuntu during key generation, the more random data will be generated. Feel free to wiggle your mouse, bash the keyboard, and take the opportunity to clean your touchscreen while the process is underway.
Depending on your PC's horsepower and the key length you chose, key generation can take anywhere from a couple of seconds to a few minutes.
Once the key has been generated, it will appear in the GnuPG Keys section of the app.
Your computer may one day fail to boot, and you'll find that your drives have died. If this happens, the encrypted files you've stored elsewhere will be as inaccessible to you as to anyone else.
For peace of mind, you should back up your key to a safe location such as a USB thumb drive. Right-click on your key, then select Export. Choose your export location from the file picker.
If you ever do need to import your key, click the + icon, and select Import from file.
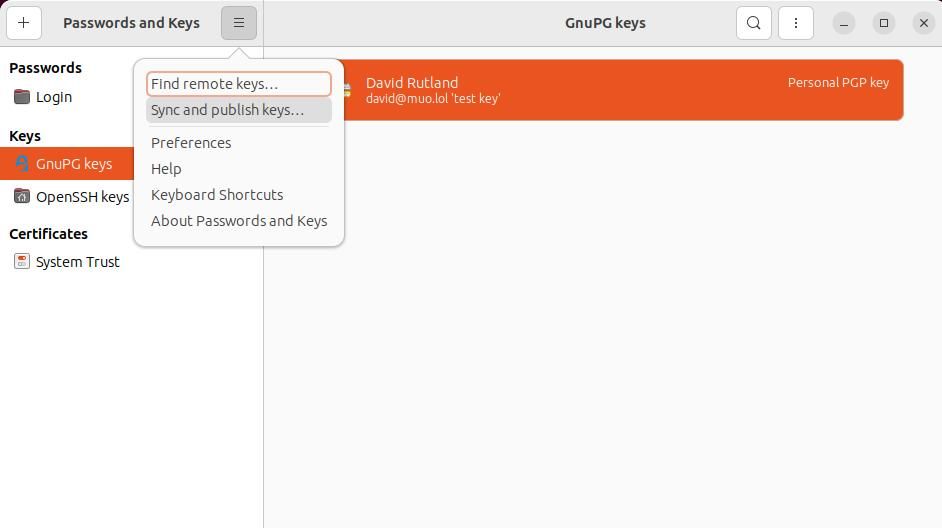
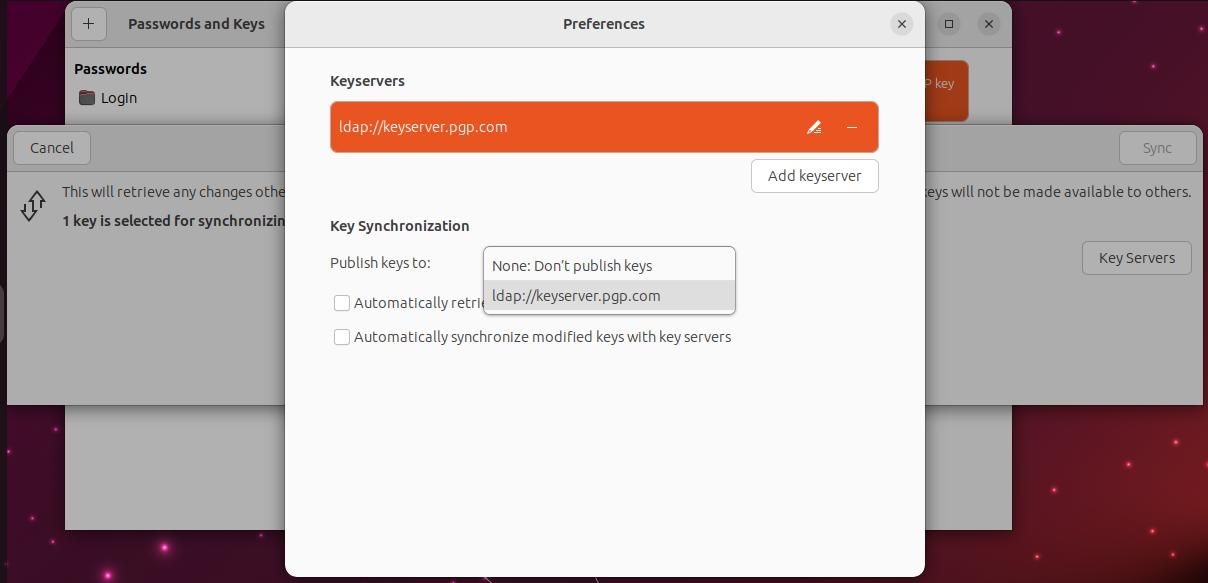
You can also store your keys on remote key servers. To do this, click on the hamburger menu icon, click Sync and publish keys, then Key Servers.
By default, Seahorse uses two keyservers, choose either one of these, then select your preferred key from the drop-down in Key synchronization.
Close the window, then press the green Sync button.
To find and use keys you've previously synced, click on the hamburger menu icon again, and search for your name or email address.
Encrypt Your Files With Seahorse on Ubuntu
If you're running Ubuntu version 22.04 or later, you'll need to manually install the Nautilus Seahorse extension before you can encrypt files from your desktop. Open a terminal and enter:
sudo apt install seahorse-nautilus
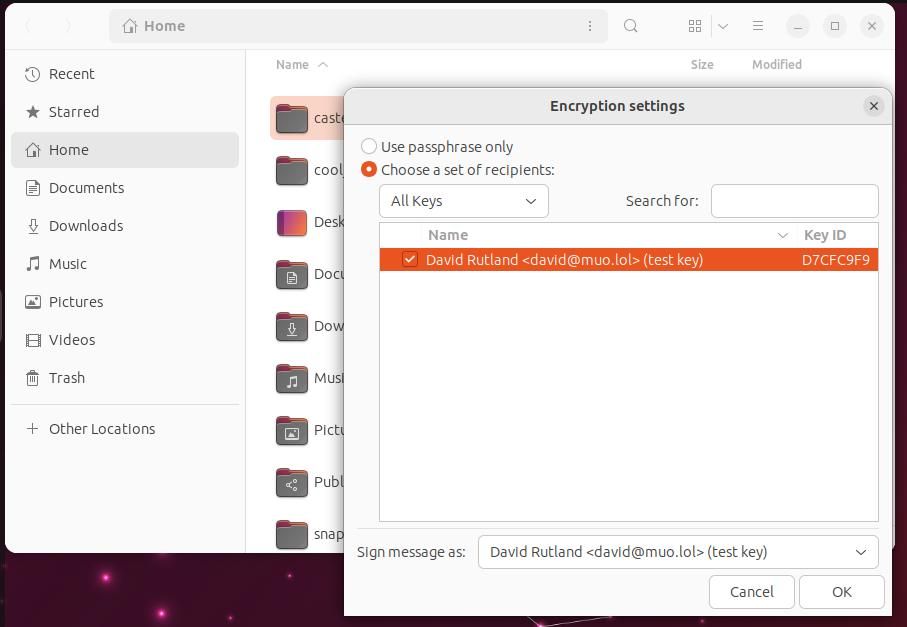
Once you've installed the extension, close your terminal window, and locate your file or folder in the Nautilus file manager. Right-click, then select Encrypt. In the next window, select your key, then press OK.
If you've chosen to encrypt a directory, you'll be asked whether you want to encrypt each file separately or compress the entire directory before encryption. Make your choice, select your preferred compression algorithm, then press OK.
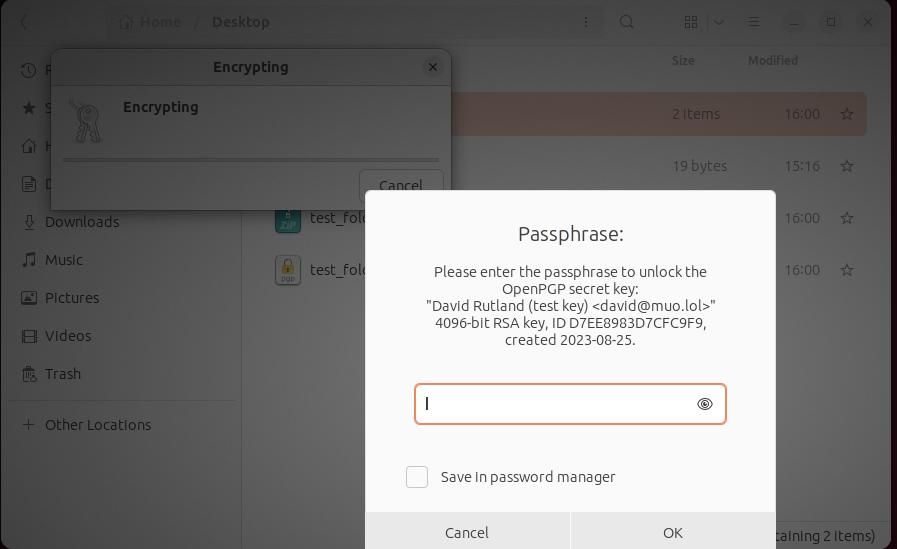
You'll be asked to enter the passphrase you created in Seahorse. Once you've done that, click OK. Your encrypted file will appear with a PGP extension in the same folder.
Encrypting Files Is Easy With Seahorse on Ubuntu
Encrypting your sensitive files is important whether you intend to send them over the internet or keep them to yourself.
By using Seahorse on Ubuntu to manage your keys and encryption, you can be sure that the only person who will ever set eyes on your private data is you.