You can never be too conscious about email security. After all, scams are still commonplace and there are so many ways that email accounts can be exploited. Vulnerabilities are everywhere.
And while you may feel safe right now, just know this: everyone is always one mistake away from being hacked. Security is a game of probabilities and the end goal is to reduce the number of potential mistakes you can make.
So if you use Gmail, here are some important tips that you should put into practice as soon as possible. They'll inevitably save you a lot of headaches and grief down the road.
1. Encrypt Your Emails
Whenever you want improved security, encryption is always the first thing you should consider. Encryption makes it so that even if your connection is eavesdropped, the eavesdropper won't be able to make sense of the data.
On the web, regular connections take place over HTTP while encrypted connections take place over HTTPS. Not all websites offer HTTPS connections, but fortunately Gmail does -- and Google considers encryption to be so important that HTTPS is forced on.
In addition, Google recently announced that they'll be implementing a Gmail warning that alerts users whenever an email arrives via an unencrypted connection. Such emails could easily be hijacked and/or altered.
Pro Tip: Learn more about encrypted connections with our explanation of HTTPS and why it's so important.
However, HTTPS is more of a baseline for proper email security so you should take extra steps take to really protect your information. For example, instead of just encrypting the connection, you might also want to encrypt the actual email messages.
Mailvelope is one popular tool that can do this for you. This Chrome extension integrates right into Gmail (as well as GMX, Outlook, Yahoo, and others) and simplifies the process of encrypting and decrypting emails.
2. Enable Two-Step Verification
Another big non-negotiable feature is two-step verification, which is also known by its more technical name, two-factor authentication. This simple feature -- which requires very little effort on your part -- can instantly double or triple the security of your email account.
Two-step verification just means that you need to have two forms of verification in order to log into your account: the first is your regular account password and the second is a verification code that's sent to your mobile phone.
In other words, in order for someone to hack into your account, they'll need to have your password and your mobile phone -- an incredibly unlikely scenario. And while two-factor authentication isn't flawless, it's still strong enough that you shouldn't overlook it.
To enable two-step verification:
- Open your profile icon at the top right of Gmail and click My Account.
- Under Sign-In & Security, select Signing Into Google.
- Under Password & Sign-In Method, select 2-Step Verification.
- Enter your phone number and select a verification method.
3. Sign In Using Incognito Mode
Nowadays it's more common to check on-the-go email with a mobile device rather than a shared computer, but shared computers are still used regularly (e.g. libraries, Internet cafes, or even just hopping onto your friend's laptop).
But if you aren't diligent, you might accidentally stay logged into your Gmail account on said shared computer, and now you've left yourself vulnerable to potentially malicious people. Your friends might cut you some slack, but strangers at the library could really wreak havoc.
That's why whenever you log into Gmail on a shared computer, you should always use Incognito Mode. On non-Chrome browsers, this is also known as private browsing mode.
There are several reasons to using private mode, but the most important is that it automatically logs you out of everything whenever the private window is closed. Just be aware that your account could still be compromised by keyloggers if you aren't careful.
4. Keep Good Password Habits
Do you know the most common password-breaking methods used by hackers today? The truth is, most of the passwords used by regular folks are surprisingly easy to break, and there's a good chance that your own password is much weaker than you think it is.
An unbreakable password has many elements, but here are the key points that you need to follow:
- Longer is better. At 1,200 password attempts per second, an eight-character password takes about 5.5 years to break while a nine-character password takes about 363,500 years to break. Every additional character offers exponential protection.
- Use special characters. Letters are the most commonly used characters. Numbers are popular too, but not as popular. Hackers know this, and alphanumeric passwords are easier to break because of it. All other factors being equal, a password with special characters is more secure.
- Be unique and change frequently. If you use the same password on all of your accounts, one compromised account can destroy all of your accounts. Always use a unique password for important accounts, and change the password at least once every six months.
Managing such complex passwords can be a headache, especially when you have to juggle dozens of different accounts, which is why we highly recommend using a password management tool. It'll keep you safe and relieve much of your stress.
It can be tempting to shrug and skip all of this, but good security habits are the difference between those who get hacked and those who don't.
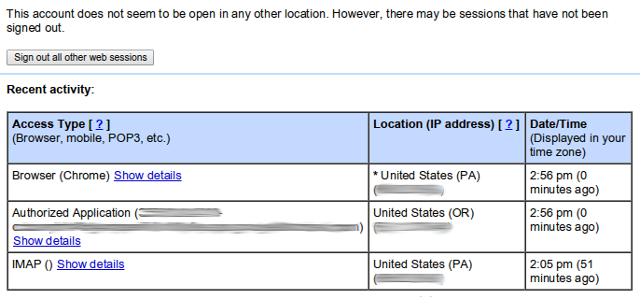
5. Check Account Activity History
At the very bottom of Gmail's web interface, there's a small bit of inconspicuous text that says "Last Account Activity", which tells you the last time there was activity on your account. Intersting but not very useful, is it?
Go ahead and click on the "Details" link and a new popup window appears, complete with a list of the last 10 IP addresses that accessed your account.
If you check this session history once every week or so, you can keep an eye out for potentially suspicious activity. Most of the records will be from your own IP address, and every once in a while you'll see the IP address of an authorized third-party app, but if you see something else altogether, then you may have been breached.
At the bottom, you can enable an alert preference that will show alerts whenever Google determines a particular activity to be unusual. Also, at the top, you can force all sessions on your Gmail account to log out by clicking "Sign out all other web sessions".
Got Any Other Gmail Tips to Share?
Other email security tips should be heeded if you want maximum security, but the tips outlined above should be more than enough for casual Gmail users. At the very least, enable two-step verification and use a unique password, and be wary of email attachments.
If you really need a super safe email, however, Gmail might not be the best choice. Rather, you should look into truly secure and encrypted email providers instead.
What steps have you taken to ensure Gmail security? Are there any that we missed? Share them with us in the comments below!
Image Credits: Encrypted Email by xtock via Shutterstock