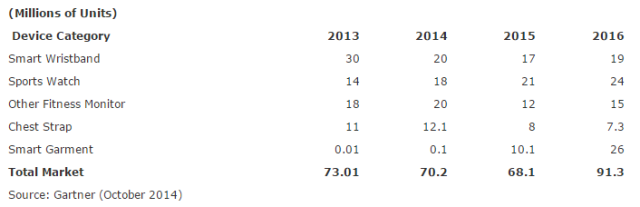Why does our security and privacy get worse with every new technological service or gadget that's released?
Televisions get better, phones get more powerful, Internet speeds increase – almost everything tech-based is on an upwards trend in terms of quality.
Everything it seems, except security. New phone? More malware. New TV? It's listening to you. New email provider? The government is watching you.
Here are five new technologies that are posing a threat to your security and privacy right now.
Smart Cars
It's like something out of a horror movie.
One minute you're happily heading to Walmart with Mozart's finest playing on the radio, but moments later your car has taken over – you're locked in, you've been taken onto the nearest freeway, and you're heading into the wilderness at 150 mph while Black Sabbath pumps out of your speakers.
Sounds silly, but this could be a reality as more and more cars connect to the Internet.
Of course, in the middle of last year we saw the "Jeep Hack". Two security researchers found a problem with Chrysler's Uconnect system (the software that allows users to make phone calls, control entertainment, and create a Wi-Fi hotspot while driving). By exploiting this flaw, they were able to take over the engine, the brakes, the in-car entertainment systems, and the peripheral electronics, like windscreen wipers and headlights.
Chrysler quickly fixed the flaw – but it would be naïve to pretend that this will be an isolated incident. In the same way that more laptops and mobile phones mean more viruses, more smart cars will undoubtedly mean more hack attempts.
The Internet of Things
Whether you either need or want a fridge that has the ability to give you the weather forecast in Beijing and play songs on your dog's iPod is immaterial – the fact is the Internet of Things is coming now and it is coming fast.
This blurring of the virtual and physical world brings a whole host of new security threats and privacy concerns – some of which we've covered in great detail elsewhere on the site.
In truth, the risks need little explaining. There are so many access points collecting data that manufacturers and product providers will have a better understanding of your life than everyone except your very closest family.
You only have to look at Samsung and Microsoft's on-stage demonstration at CES 2016 a few weeks ago. Microsoft's Bryan Roper went on stage to explain how Cortana would be able to control a Samsung washing machine. That sounds great in principle – but towards to end of the demo he started pulling up stats about how much time each household member was spending using each in-home appliance. Is that necessary? And even if you deem it useful, do Samsung and Microsoft really need (or deserve) that information?
Fitness Trackers
Everyone from small start-ups to some of the world's biggest sports companies have been diving into the world of wearable fitness trackers in the last few years.
There were an estimated 68 million units sold last year, and although Gartner expects a slight decrease in sales over the coming years as smartwatches gather steam, the industry is still expected to be booming well into the next decade.
Worryingly, there are an increasing number of security flaws being discovered in the devices.
Consider this; according to research by Symantec, someone who hacks your device will have access to where and when you go running, where you live, and where and when you are on vacation – as well as lots of other data.
If that alone isn't not enough to send shivers down your spine, they also state that "some third-party applications are communicating with up to 15 different remote locations, including analytics companies and a variety of different organizations."
Do you want all that data being freely shared with companies?
Smart Medical Equipment
The potential health-based implications of ever-improving technology are tremendous.
For example, if you need a pacemaker in your heart, you can now get a "smart" one. These devices have the capability to send a steady stream of analytics, data, and feedback to your doctor, allowing them to stay abreast of developing health issues that can be tackled before they become too dangerous.
So far, so good. But what if someone with nefarious goals manages to hack your device? Could they kill you? It's certainly not out of the question.
Famously, former US Vice President Dick Cheney asked for his smart pacemaker to be disabled in case an advanced terrorist organization managed to gain access to it. Furthermore, research from the University of Michigan suggests that a device as small as a mobile phone could be used to hack multiple devices at the same time in crowded spaces like sports events and concerts.
It's hugely worrying.
Li-Fi
Li-Fi (short for "Light Fidelity") is being touted in the media as Wi-Fi 2.0, with the potential to offer speeds that are up to 100 times faster than the current ubiquitous standard.
In practice, however, it still has several problems to overcome – not least the fact it'll require entirely new infrastructure in the home and that it has serious problems working in adverse weather conditions.
Regardless of these problems, it seems Li-Fi will be slowly introduced. An Estonian start-up company called Velmenni has already installed the tech in an industrial environment and is conducting tests in private clients' homes.
So what security issues will these trailblazers face?
Actually, Li-Fi is probably more secure than Wi-Fi. For example, the signal cannot travel through walls so it cannot be intercepted from outside, and the fact the technology ultimately relies on light rather than a more traditional radio wave-based router makes the underlying gadgets less "hackable". Ultimately, a hacker can only access the network if they can get to where the LED light is.
There are still issues though – for example, there is speculation that the Li-Fi signal could be intercepted by someone with a telephoto lens and a fine-tuned optical sensor.
Which New Gadgets Or Technologies Are You Wary Of?
Are you concerned about the security and privacy implications of new gadgets, or are you happy to accept the risks as part of the increasing tech-based world in which we live?
Let us know your thoughts and feedback in the comments section below.