In this day and age, our computers also double as a treasure trove for private information. As such, it's a good idea to learn how to track what someone is doing on the computer---especially when that "someone" is snooping where they shouldn't be.
Let's break down how to track computer activity and catch spies red-handed.
1. Revealer Keylogger
If you want to know how to track keystrokes, look no further than a keylogger. Keyloggers are unique programs that monitor keyboard activity and log everything that's typed.
While keyloggers are typically used for malicious purposes, you can use them yourself to log your own (or someone else's) typing. These are the easiest way to catch intruders, as a single key-press will give the game away.
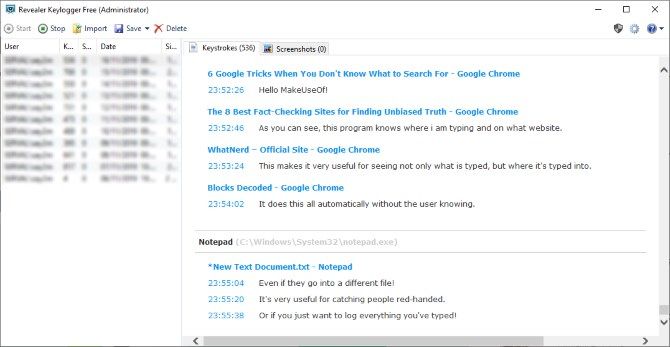
If you’d like to stick with free solutions, Revealer Keylogger is a good choice. This handy utility logs keystrokes as they occur. It also registers the exact time the key was pressed, and what application the letter was typed into.
The software can be hidden from the user so they have no idea they're falling for your trap. When you return, you can reveal the program by pressing Ctrl + Alt + F9 and check the logs.
You can buy the full version to unlock the screenshot tool, which will take photos of your screen when it detects keyboard activity.
Due to keylogger's malicious history, anti-malware software may quarantine this tool upon download. You’ll need to remove the quarantine before you can install it.
Download: Revealer Keylogger (Free, only 32-bit installer available)
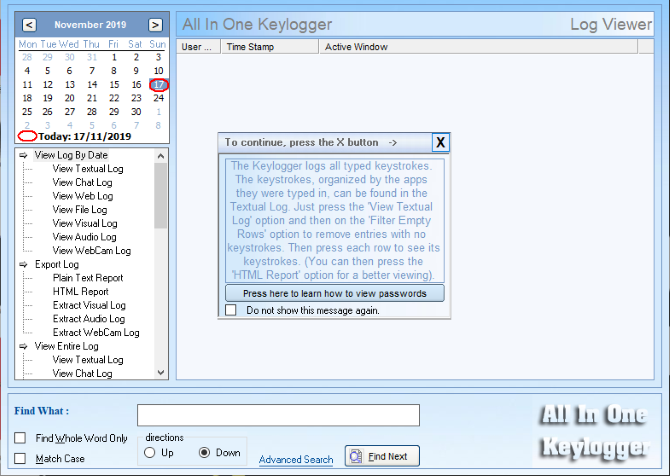
2. All In One Keylogger
Want more features and options? Then you should take the paid route. One of the better options is All In One Keylogger, which captures keystrokes like any other software. On top of this, it has advanced log filtering options and the ability to send logs to specified email addresses, FTP servers or networked computers.
In addition, this software can take screenshots and record sounds via microphone. You can use this option free for seven days, but it’s $69.95 afterward.
All In One keylogger also comes at a discounted price if you purchase multiple copies in bulk. This is ideal for equipping an entire office to check for espionage.
Download: All In One Keylogger ($69.95, only 32-bit installer available)
3. SpyAgent Spy Software
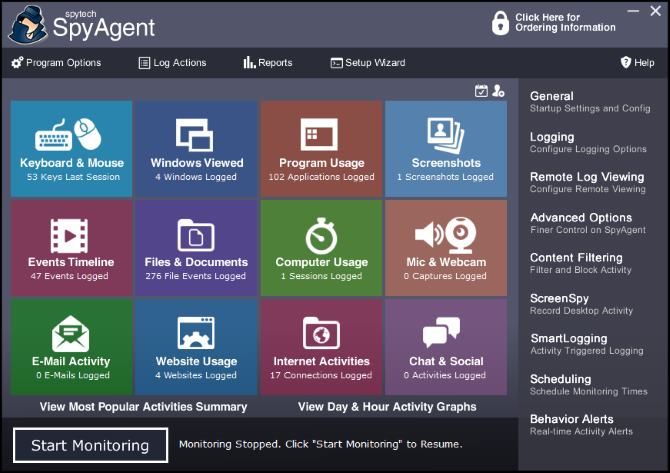
Spytech has a good selection of computer tracking software available, but their SpyAgent PC activity tracker is particularly impressive. It can track computer activities such as keypresses, clicks, software used, browsing history, and more.
When you first start the software, you need to give it a password. This is used for both starting and stopping the recording so that nobody else can tamper it. When you want to monitor your PC, click the Start Monitoring button, enter your password, and then minimize it into stealth mode.
While it's hidden, SpyAgent will begin monitoring any PC activity that occurs. It doesn't let the user know it's running, and even if it is discovered, the intruder can't stop the monitoring unless they know your special password.
When you come back, you press a special hotkey to bring the window out of hiding. Once stopped, SpyAgent will give you the details on everything that transpired during the session. It will even show you periodic screenshots of the monitor so you can see what was going on.
SpyAgent goes into impressive detail when recording what changed. It even detects files being deleted or created on the operating system, so you can tell if someone tampered with your files. This makes for a great one-size-fits-all solution that can monitor every part of your computer.
You can download the free trial to give SpyAgent a shot. If it impresses you, you can purchase the full software for $69.95.
A word of warning: As SpyAgent is an in-depth PC activity tracker, your antivirus will likely have a panic attack when you download the trial. Be sure to tell it to leave the file alone, else you'll never get past the installation step.
Download: SpyAgent ($69.95, only 32-bit installer available)
4. iSpy – Automatic Webcam Recording
Let’s say that unauthorized computer use is just the beginning of your problems. What if you’re also concerned about what’s going on around your computer? A keylogger or activity monitor can’t help you there.
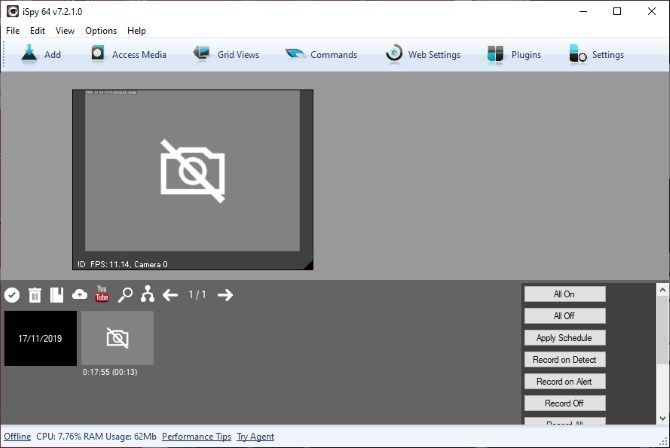
That’s where iSpy comes in. This free, open-source software can track computer activity through your webcam. It has motion tracking and scheduling features that allow you to record only when you need to.
It also has the ability to automatically upload the recorded video to the web, including YouTube. That’s handy because it allows for remote storage of video immediately, keeping it safe from any attempt to delete it.
When you first install and run iSpy, it asks you to add a camera. Once you do so, it'll show your feed and a green bar underneath it. The green bar may look like the microphone sound levels, but don't be fooled. This bar is actually how much motion iSpy is detecting. The more movement iSpy detects, the more the green bar fills. If the bar goes over the red arrows, it'll start recording.
As such, it's a good idea to get used to iSpy before you use it for real. Leave the program running and get out of the webcam's viewpoint. Then, pretend to be an intruder, sit down, and start using the computer.
Once you're done, you can then view when iSpy triggered, and what movements started the recording. Make sure that background movement doesn't register; you don't want 30 minutes of footage of the cats walking around.
Download: iSpy (Free, 32 and 64-bit versions available)
Keeping Your Privacy Safe From Snooping
With the above tools, you now know how to track PC activity even when you're not in the room. You can find out what was typed, what websites were visited, what files were downloaded, and what emails were sent. You can even see what’s going on in front of your computer remotely via your webcam.
If you'd like to monitor intruders without downloading tools, be sure to try these ways that tell if someone was snooping on your computer.