If you’re anything like me, you’re pretty attached to your smartphone. I use mine almost constantly, checking for emails while I’m out and about; I play games on it, research work, chat, interact with social networks and enjoy videos. I also use the camera extensively to photograph family and friends.
I’m sure I’m not alone in this wide use of my handheld multimedia computer and communication device. But do you have security software installed? Are you even aware of the risks to your smartphone?
There seems to be a sort of general malaise among users – the tech savvy and everyday users alike – that because your computer fits in your pocket, it can’t be infected by malware, Trojans, worms or other threats. This is, of course, ridiculous, and perhaps stems from the age-old misunderstanding of the nature of malware transmission.
The benefits afforded to us by smartphones are immense; the threats they can introduce into our lives if left unprotected are considerable.
Threats from SMS
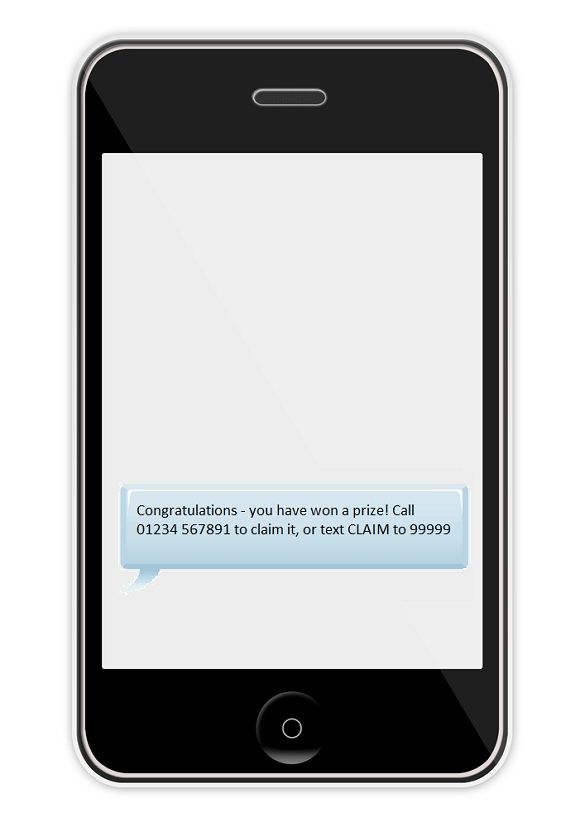
Remarkable as it may seem, the old school SMS text messaging service is a popular choice for rogue programmers working for hacking gangs around the world. SMS spam is bad enough, but have you considered that it might be a form of Smishing?
This term is used to name phishing attempts sent via SMS, and is used to fool victims into giving up personal data, perhaps to a fake delivery company. Smishing can be achieved either wholly through a return message or by being prompted to call a number where the information is recorded.
Once recorded, this information can be used to create a fake bank account.
The answer, of course, is to delete any such messages, whatever they're offering.
Wi-Fi and Bluetooth Security Risks
Free Wi-Fi hotspots always look attractive, but they can prove to be both rife with malware and provided by scammers looking to capture your personal data such as passwords, credit card data and other user-identifiable information. If you find free Wi-Fi in a public place that isn’t provided by a reputable business, avoid it. Similarly, if you are using your smartphone as a mobile hotspot, make sure you have set a secure password. You should change this each time you use the hotspot feature.
Another threat is War Texting, in which smartphone-connected car systems can be hacked by sniffing the authentication codes sent from phone to car. The best outcome of this is that you are tracked; the worst is that your car is stolen, without a key.
As such systems become more popular and widespread in cars, so many more people will become targets – as things stand, few cars can be activated in this way.
Any password that you use on your phone, whether it is for unlocking, accessing voicemail or setting up Bluetooth, should be changed from the device to something memorable. Failure to do this can lead to all sorts of problems.
Location-based Threats
Thanks to wireless networks, cellphone triangulation and GPS, it is possible to take advantage of many location-based tools for smartphones and tablets. These might be sat-nav tools or social ones, but there are many threats to be aware of too.
One of these is geotagging, a default option on many smartphone apps that you should disable if you wish your current location to remain a secret.
Social network check-in features can also be used to track you. When a criminal knows your whereabouts he or she might be planning to assault you or use your absence from your home or car to cause criminal damage or theft.
The Danger of Rogue Apps
There are rogue apps on any platform. On Android they can usually be spotted pretty quickly thanks to the reviews of others (although on iPhone and Windows Phone such apps are unlikely to be permitted to be listed) but it could be too late if you’ve already installed the app. This is why you should only install apps from trusted repositories.
This can be a particular problem for Android users, mainly because there are several online marketplaces from which software can be installed. It’s no surprise that the number of threats for Android has increased over the past few years. One example is Android.Spyware.GoneSixty.Gen – discovered in 2011, this malware if installed, sends important information from your phone to a remote server and uninstalls itself within a minute.
You’ll never know it was ever there - frightening stuff.
On the subject of apps, you should also be aware that shortened URLs in Twitter and email can be dangerous. This is as important on smartphones as on desktop computers, as the resulting links can be effortlessly tailored to serve malicious code depending on the device that is connecting.
So You Want to Stay Safe?
If you would rather your smartphone or tablet didn’t become a key to steal your car, a listening or tracking device or a means to send all of your personal data to a band of criminals specializing in ID theft, there are certain steps you should take.
- Apply a lock-screen password. This is particularly important if you’re using a modern Android device where the drag-to-start feature looks amazing. What you should do is forget about how good it looks and how responsive it is, and employ a password.
- Don’t Jailbreak your iPhone or root your Android. The advantages to users requiring particular types of app are excellent on a rooted device, but this process also gives access to intruders, either through apps or directly over the Internet. Many of the MakeUseOf team are fans of unlocking their phones, but this shouldn't be done without considering the implications and taking the necessary steps for protection.
- Avoid non-secure access points. If you’re out and about using a smartphone or tablet (or even a laptop) then you should be using either your own portable wireless access point (provided by your phone) or a secure, password protected point. Open networks can prove to be a hive of malware!
- Avoiding untrusted apps. This is wise for several reasons, not least because the peer review on offer in online app stores is unparalleled. Google Play is a good example, and is so successful despite competing Android app stores partly because of this reason. As there is no real need to install untrusted or poorly regarded apps, avoid! Also look out for fake apps that appear to be genuine, as these can often be dangerous.
- Employing backup tools and security software. There’s no reason anyone receiving emails and storing data on their handheld computers (as this is what smartphones essentially are!) should not have either a backup tool OR anti-malware software installed (preferably both).
Overall: Be Aware
There are plenty of threats that you should be aware of, ready to strike your phone over Wi-Fi, Bluetooth, SMS, from app stores or via location tracking.
Naturally, you can’t be aware of every specific threat, but with the help of the tips above you can be aware that threats exist, and that there are steps that you can take to minimize the risks.
Once you recognize this, you should act on it – and protect your smartphone, your data and your personal security.
Image Credit: Phone chatting template via Shutterstock, PDA security via Shutterstock, Black smartphone with eye via Shutterstock, iPhone image via Shutterstock