Have you ever wanted a physical key for your computer?
Now that passwords are becoming obsolete, a real key would be more than a tricky gimmick. Indeed, requiring a physical component to unlock your PC may just be the most secure option right now, and if you have a spare USB thumb drive lying around, you can set up a key in just a few minutes.
So, here's how you turn any USB flash drive into a security key.
USB Unlock Keys: The Good and The Bad
Relying on passwords alone is a big security misstep that may cause problems for you down the road. Even if you create strong passwords and practice good security habits, one flaw remains: once discovered, a password is useless. In that sense, a physical key is harder to compromise, and tangible keys are harder to steal than intangible thoughts.
Another obvious benefit is that you relieve yourself of the burden of password memory, although this is less of an issue if you use a secure password manager. Additional benefits exist depending on the software you use for creating the USB key.
But it's not all sunshine and roses.
For one, you'll suffer some headaches if you ever lose or damage the USB key; key recovery is more of a headache than resetting a password. Other drawbacks include the fact that the key permanently occupies USB port space, and if you ever want to grant someone else access, you have to hand them the key physically.
Before plunging ahead and setting up a USB security key, you'll have to decide for yourself whether the pros are worth the cons.
3 Tools to Turn a USB Flash Drive into a USB Security Key
If you like the sound of a USB security key and have a USB flash drive to spare, check out these three tools. They're mostly easy to use and will guide you through the process of creating a USB security key.
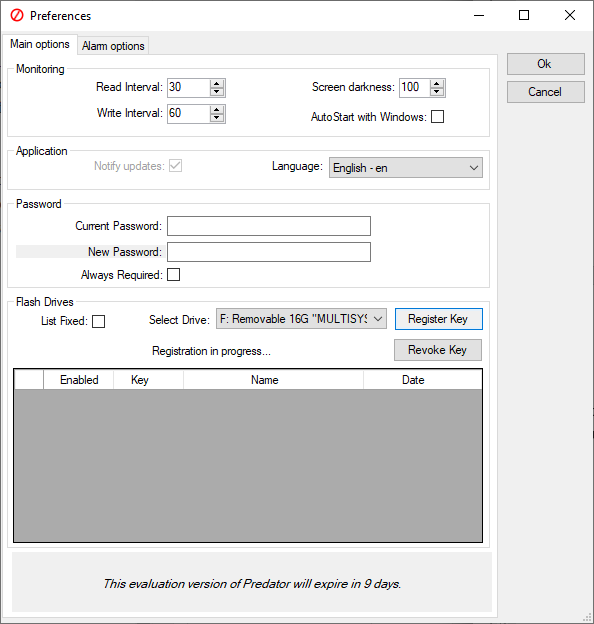
1. Predator
Predator is one of the most popular tools for turning a USB drive into an access control device on Windows.
Predator was once completely free for Home users. However, that situation has now changed, with a Home Edition license setting you back $10. For professional and commercial environments, it costs $15 per computer with no customer support. For Predator Professional with one-year support, you're looking at $30 per computer.
As long as the USB drive is plugged in, access to the computer is allowed. USB drives used as keys will remain completely unaltered. No files will be deleted or modified in any way.
Advanced features include:
- One USB drive can be used to lock/unlock multiple computers.
- Multiple USB drives can be assigned to various users.
- Built-in scheduler that can limit computer access to certain times of day.
- Schedules can be determined on a per-user basis.
- In case of a lost or broken USB key, per-user passwords can be entered instead.
- The USB drive security codes are regularly changed, limiting the effectiveness of copied USB drives.
Predator is a great option if you want a quick and simple USB security solution. It is one of the most powerful and flexible programs on this list.
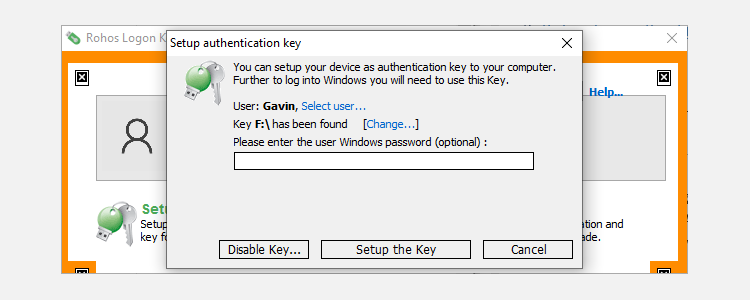
2. Rohos Logon Key Free
Rohos Logon Key Free is a multi-platform access control program available to create USB keys on Windows and Mac.
There is an unlimited free version with several key features missing (no pun intended), though it's only available for Windows. If you want full security and protection, or if you're using a Mac, then you'll need to pay the full $35.
Rohos works by storing your login information and automatically inputting your credentials when the USB is plugged in. Alternate logon methods exist for Android and iOS, allowing you to unlock your Windows or Mac computer access through your smartphone.
Features include:
- Secure two-factor authentication using a USB key and PIN code.
- Emergency logon system that grants you access in case of a lost or broken USB or a forgotten PIN code.
- Passwords stored on USB key devices are encrypted with AES-256 and protected against unauthorized duplicates.
As far as ease of setup is concerned, Rohos is easier and more straightforward to use than Predator. However, that's because Rohos is a simpler program that's fundamentally different. It's a literal replacement for typing in credentials: you plug it in to unlock at the unlock screen.
This, of course, makes it less secure than Predator, so you should only use Rohos if you specifically need the USB-as-login-credential functionality rather than Predator's keep-plugged-for-access functionality.
Furthermore, you should note that the two-factor authentication option is not available to free accounts. As an important security feature, this should be a consideration for your USB security key selection.
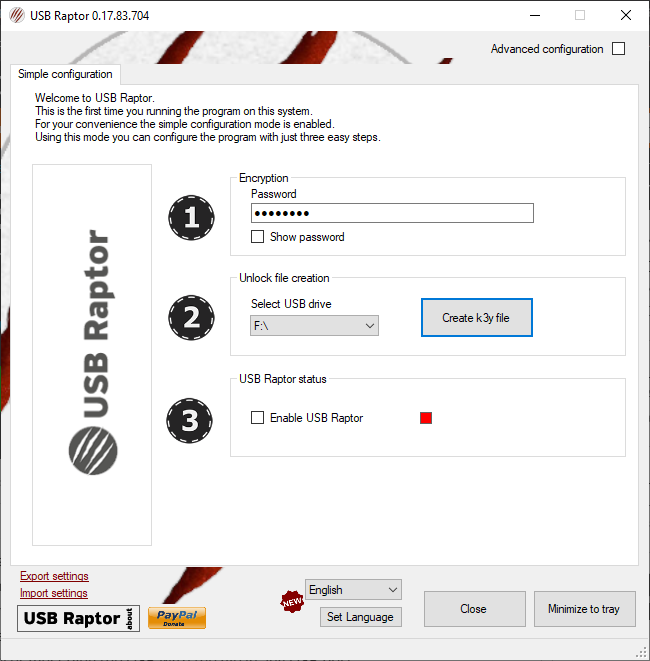
3. USB Raptor
USB Raptor is a free USB security key app you can use to lock your Windows machine. Like other USB security options, Raptor locks your machine when you remove the USB flash drive from the system.
One thing to note about USB Raptor is that it functions as a portable app. You don't need to install USB Raptor to use it on your system, only run the executable to configure your USB drive and the app.
Features include:
- Password or network command override
- Pair unlock file with the USB flash drive serial number
- Lock drive screen customization
- Always start system locked
USB Raptor is easy to use. The ability to tie the USB security drive unlock function to your USB flash drive's serial code is a handy security boost, just so long as you remember to set a password override in case you lose the drive.
What About Hardware Security Keys?
If you don't want to get involved with third-party USB security keys, there are off-the-shelf USB security key options, too.
Some examples include the extremely popular Yubico YubiKey and its variants, the Google Titan Key, the Thetis Fido U2F, and the Kensington Verimark Fingerprint key. These are just a few options but represent some of the best options currently on the market.
Whichever option you choose—a third-party USB security key or an off-the-shelf option—you're taking a great step toward increasing your security.