The Holidays are almost upon us once again. And that can only mean one thing—it's time to go crazy with online shopping.
Unfortunately, the evil underbelly of the web is lurking, waiting to take advantage of your generous spending binges. Criminals want your credit card details, your cash, your identity, and your soul. Okay, maybe not your soul. But they'll go to any lengths to achieve their malicious objectives.
To ensure you stay safe while shopping during this holiday season, here are all the ways to protect yourself when shopping online.
1. Use a Familiar and Trusted Website
The first rule of online shopping is simple; stick to trusted websites. This can be Amazon, eBay, Etsy, Target, Walmart; basically the big names. Prioritize websites that have an established brand reputation to protect, and who would go out of their way to ensure a seamless online shopping experience for their customers.
Although this does a huge disservice to the smaller brands trying to make a living, it is your safest bet. If you choose to order from less popular websites, here's how to spot fake retail websites so you don't fall a victim to scam. If you want to go the cheap route by buying from eBay or AliExpress, here's how to buy safely from AliExpress. We've also put together some eBay scams you should watch out for.
2. Stick to Using HTTPS
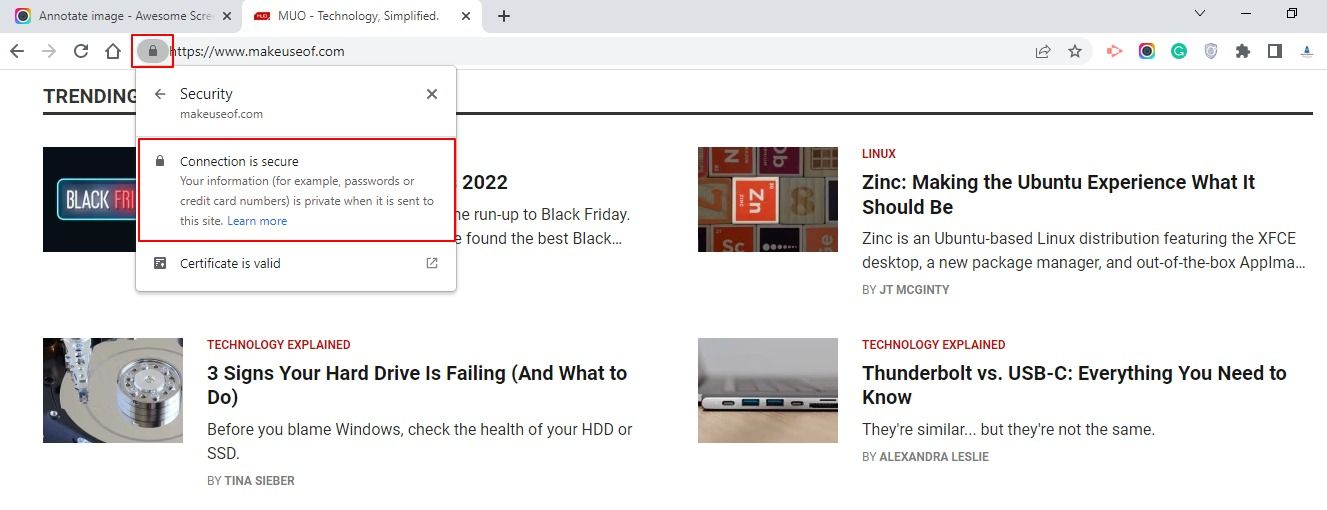
HTTPS is the more secure alternative to HTTP (Hypertext Transfer Protocol). Without getting too technical, HTTPS uses an additional layer of security to protect transported data. To identify a page using HTTPS, you should see https:// with an s as part of the page URL, instead of http:// without an s.
What does this mean? It means that your data is encrypted when you visit websites using the HTTPS protocol. This is very important when visiting websites where you'll need to pay for goods or services. HTTPS ensures that your payment details are encrypted from your end to the seller's end, ensuring that the details are not intercepted in transit by a malicious third party.
Also look out for the padlock next to the web address. This means the site is secure and encrypted. No padlock? You might want to reconsider buying from that website. However, HTTPS is only a piece of the safety puzzle, read on for more.
3. Be Cautious of Free Public Wi-Fi
Free Wi-Fi is tempting. If you use the free Wi-Fi at Starbucks, McDonald's or any public location to do your shopping, that's a dangerous practice you should stop. Unsecured hotspots are a big no-no, especially if you are not using HTTPS when shopping online.
What could go wrong? Well, it's a perfect opportunity for a Man-in-the-Middle (MITM) attack. In this case, an attacker could position himself between your Internet traffic and the website you're trying to access. So when you're submitting your credit card details or any important personal information, it passes through the attacker before reaching the website you're buying from.
This could be very devastating depending on the type of information the attacker gets hold of. If the temptation to use public Wi-Fi is too strong, we don't judge. However, try to protect yourself by sticking to HTTPS and using the best free VPN services you can get.
4. Use a Difficult Password
When buying this holiday season, you might end up creating a lot of customer accounts to put in your orders. Those accounts need a password to protect all the sensitive information you will be putting in there. Your address, cellphone number, credit card number, CVV number, and card expiry date, are the typical information you'll need to buy stuff online. They're also the kind of information that digital thieves will be hunting for.
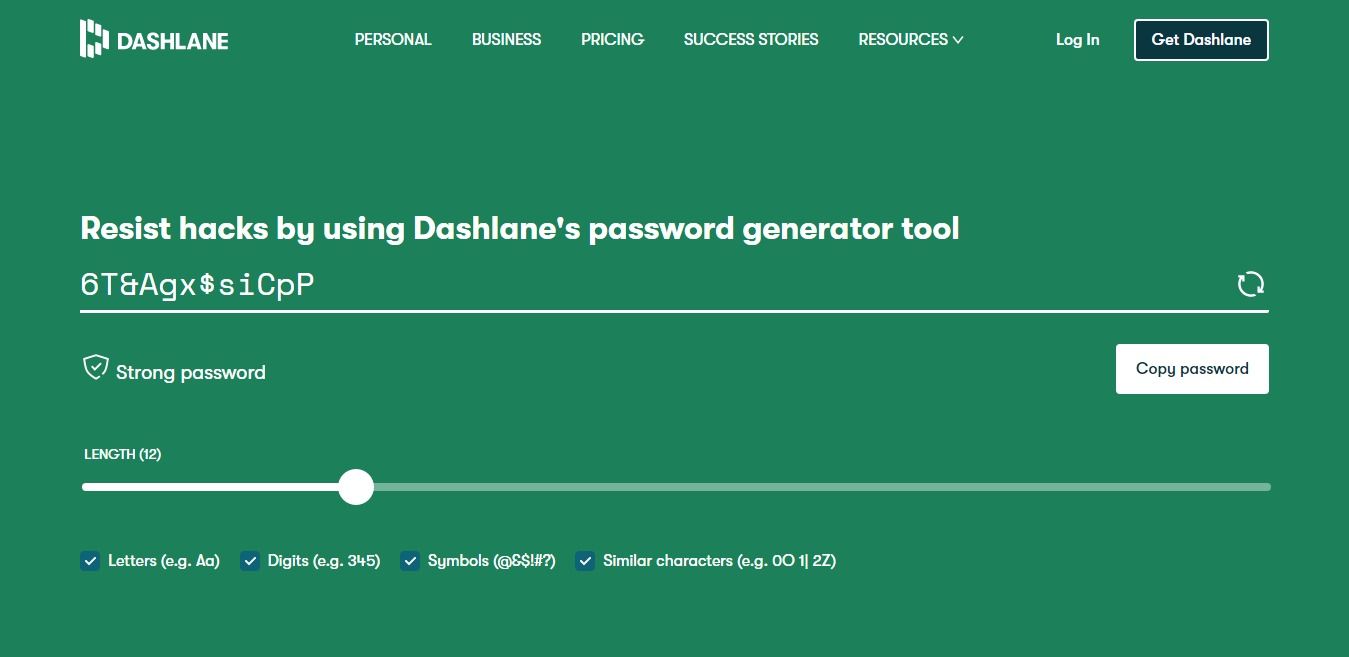
A strong password is one of the best ways to ensure that the information you submit while shopping online doesn't fall into the wrong hands. But what's a strong password? Everyone has their own idea of a strong password, but it should ideally be something incredibly hard or outright impossible to guess. Dashlane password generator tool, Passwordsgenerators.net, and LastPass password generator tool are great tools for generating strong passwords.
Of course, there's no point in creating strong passwords if you are going to forget them or end up storing them where they can be seen by attackers. To fix this, we recommend using password managers for storing your passwords.
5. Use 2-Factor Authentication (2FA)
You've probably read about 2-Factor authentication and how useful it can be. If you've neglected the idea, now is probably the time to take it seriously. Yes, it can be a pain having to complete a longer authentication process, but it makes it extremely difficult, perhaps even impossible, for intruders to break into any online account that has 2FA enabled.
Although not all sites support 2FA, whenever you shop at an online store that has the option, turn it on.
6. Choose Your Payment Methods Wisely
When it comes to using the checkout feature to pay, you need to give serious thought as to how you want to pay. If it is a big-name merchant like Amazon, Barnes & Noble, Walmart, etc., then there are fewer safety concerns with giving them your card details. But for the smaller sites, try other options like Apple Pay, Venmo, Stripe, PayPal or other payment channels that don't involve handing over your card details to retail websites. This way, you save yourself from the risk of your card details falling into the wrong hands. You'll also be able to take advantage of buyer protection programs that any of the payment channels may offer, should things go wrong.
7. Don't Be So Forthcoming With Your Information
Holiday seasons are typically doted with freebies. But be careful of the ones you accept. You'll find a lot of offers that asks you to fill a form to get a gift. All you have to do is provide little information about yourself. Be cautious. The information you give out today may come back to haunt you later. Even when you need to provide your personal information when buying from legitimate websites, give out only what is necessary and nothing more.
If you're not planning to be a repeat customer with a website, use temporary email, burner phone numbers and VPN. Remain as anonymous as possible. Data breaches often happen. You don't want your data in the wild just because you bought a $20 Christmas light from some random website that got hacked.
8. Be Cautious of Discounted Offers
Remember the old saying, "if it's too good to be true, it usually is." You're not going to get the latest MacBook Air for under $300 because some random site with a phony name says so. Yes, it's holiday season, and you'll find a lot of goods at heavily discounted prices. You'll naturally be on the lookout for such deals.
Fraudsters know this, and they'll try to milk the opportunity. That product you think you're getting at a discounted rate could turn out to be a refurbished unit, an older version, a Chinese clone or an outright attempt to scam you out of money.
9. Scan Suspicious Shopping Links before Clicking
You've probably given out your email address to more websites that you can keep track of. Once scammers get hold of your email and personal information, they'll use it to target you by emailing you deals you'll most likely want to grab. There's one problem though—it's a bait.
They're probably trying to get you to click on some phishing link. While some of such emails will end up in the spam folder (where they belong), some will make it to your primary inbox, and it'll be tempting to click. You don't want to miss out on a genuine offer because of unfounded fear. So you'll need to cautiously investigate such links before clicking. If you're not sure how to, here are some websites for checking whether a link is safe.
10. Be Cautious Meeting In Person With Private Sellers
Be very careful when going to pick up something from a seller in person. You might think you are smart saving those shipping fees from that Craigslist poster. But what if the "seller" happens to be an uncontrollable psychopath off his meds? You think that's too far-fetched? What if he's an armed robber?
Just practice some common safety tips. Don't get into a stranger's vehicle. Don't meet at their home or any dark alleyways. Instead, meet in a very public place, such as a shopping mall. Or a Burger King. Always tell a friend where you are going and when you are going. And ask them to check later to see if you got back okay.
Be Vigilant While Shopping Online
Holiday shopping should be a blissful activity. Unfortunately, the bad guys are out to spoil it. You can stop them on their tracks by being proactive with your security measures. Be vigilant. As a rule of thumb, trust no one until your goods arrive. Even when it does, double check it. You can never be too safe.